In my previous analyses of the Charming Kitten leak, I examined the organizational structure, target lists, financial infrastructure, and operational capabilities of Iran's APT35 hacking unit. The disclosures identified key personnel, front companies, and thousands of compromised systems across five continents. Now, additional materials from the same network access reveal three significant findings: complete salary records for both male and female operative teams, expanded footage of the Kashef surveillance platform, and a classified 2004 document showing Iran obtained confidential IAEA inspection materials, with a direct connection to an individual previously identified as a Department 40 assassination target.
Salary Records: The Financial Reality of IRGC Cyber Operations
The leaked materials include payslips and financial records documenting compensation for operatives in both the Sisters Team (Aqiq) and Brothers Team (Pelak1). These documents provide unprecedented visibility into how Iran compensates its state-sponsored hacking personnel.
Sisters Team Payslips
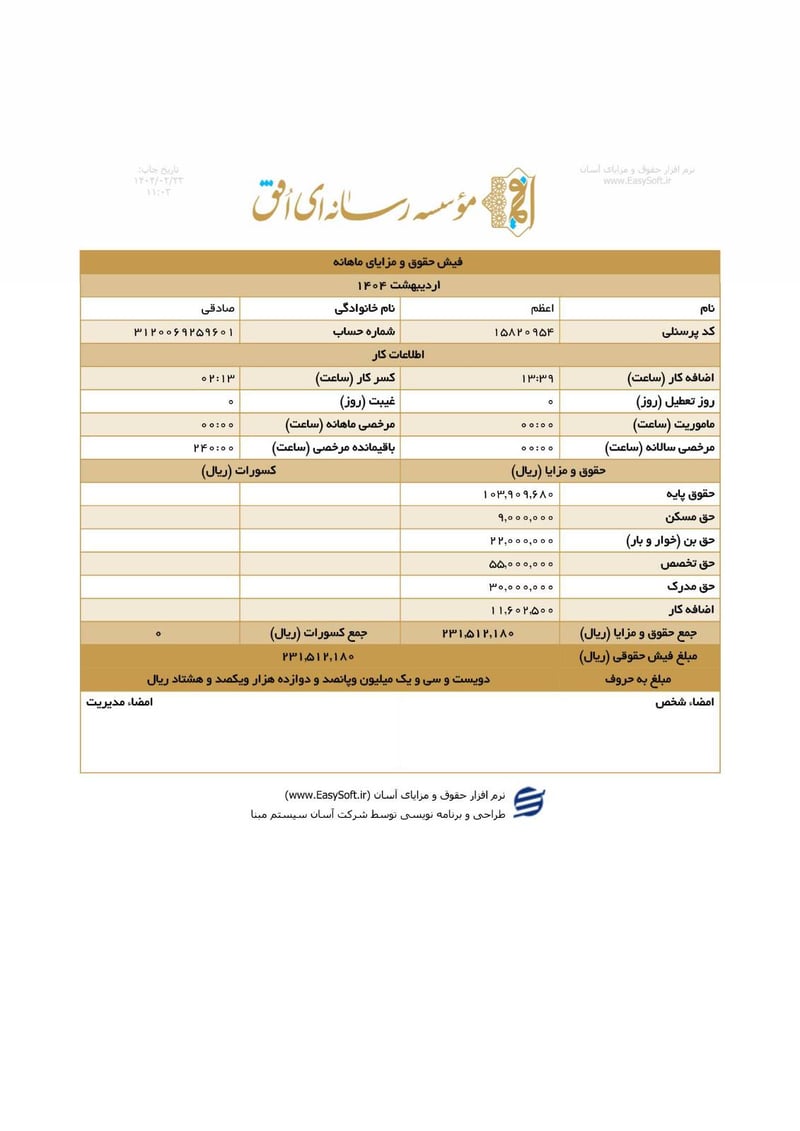
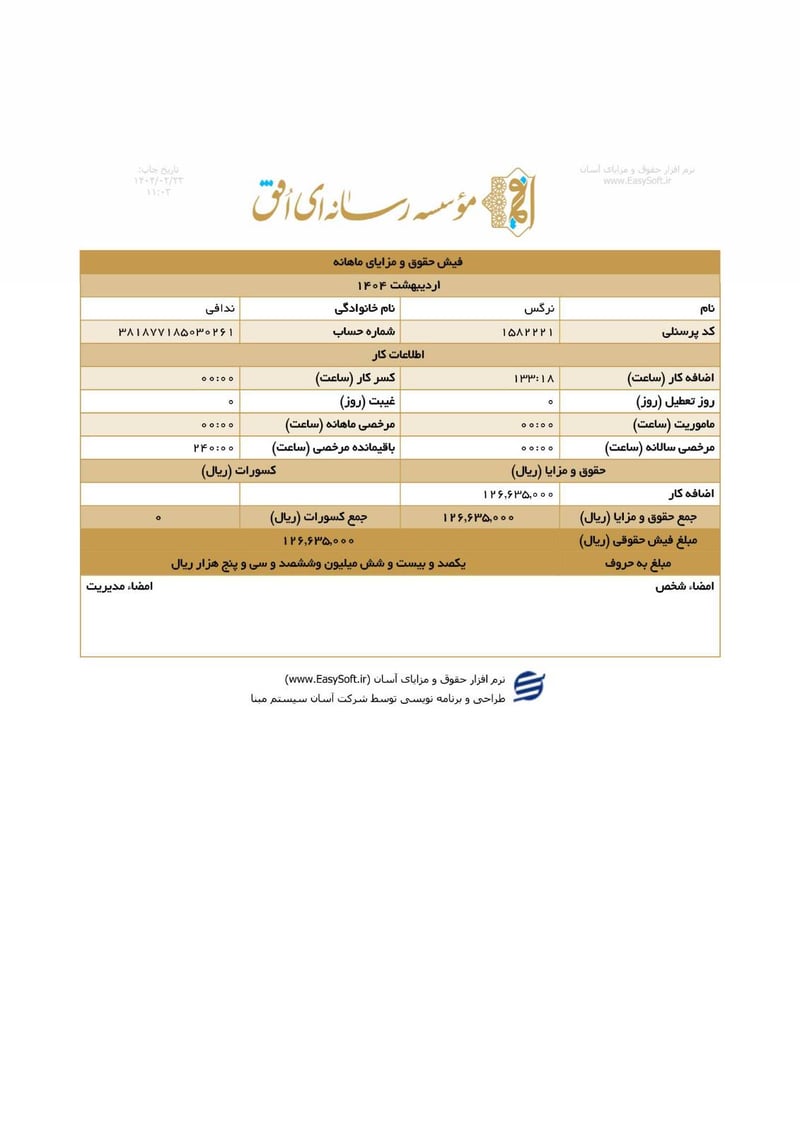
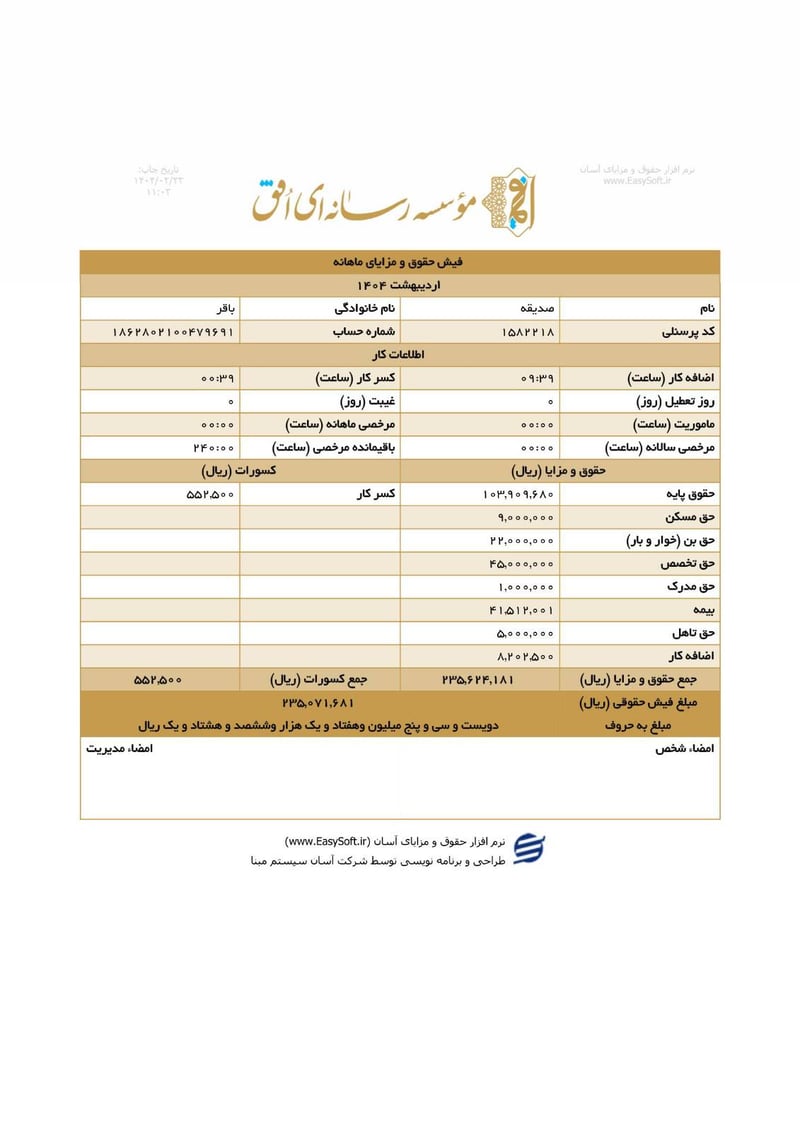
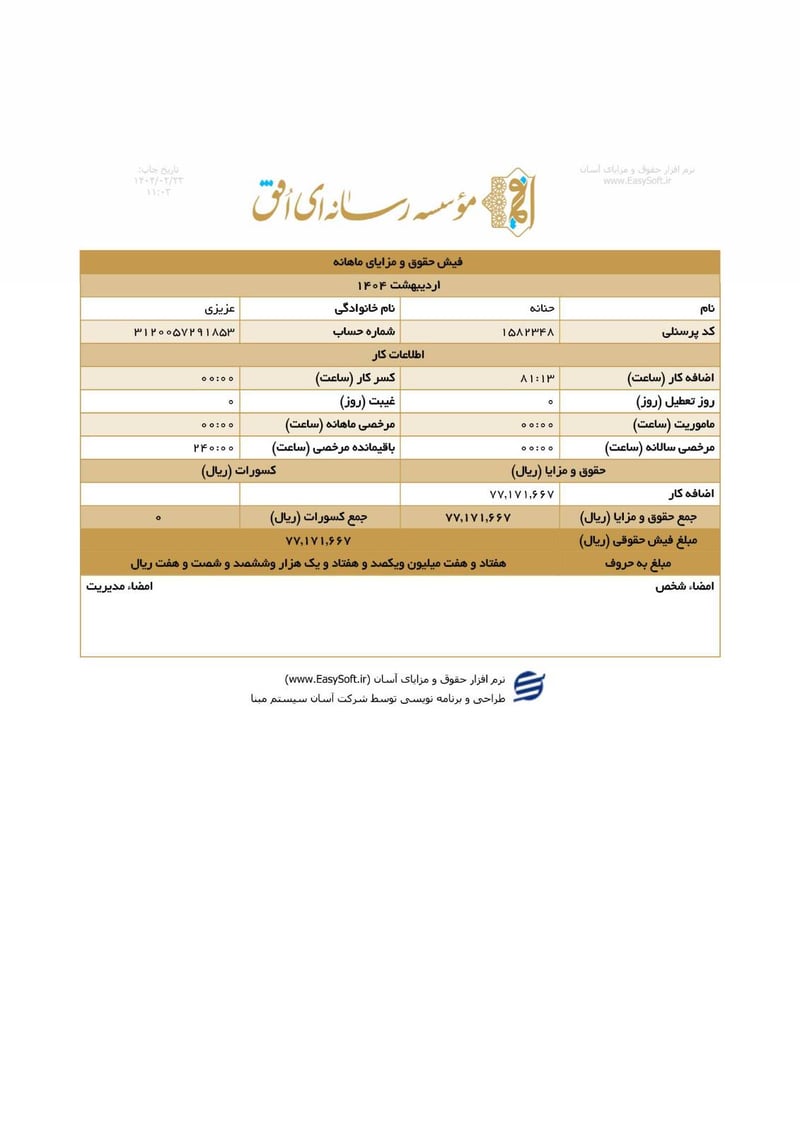
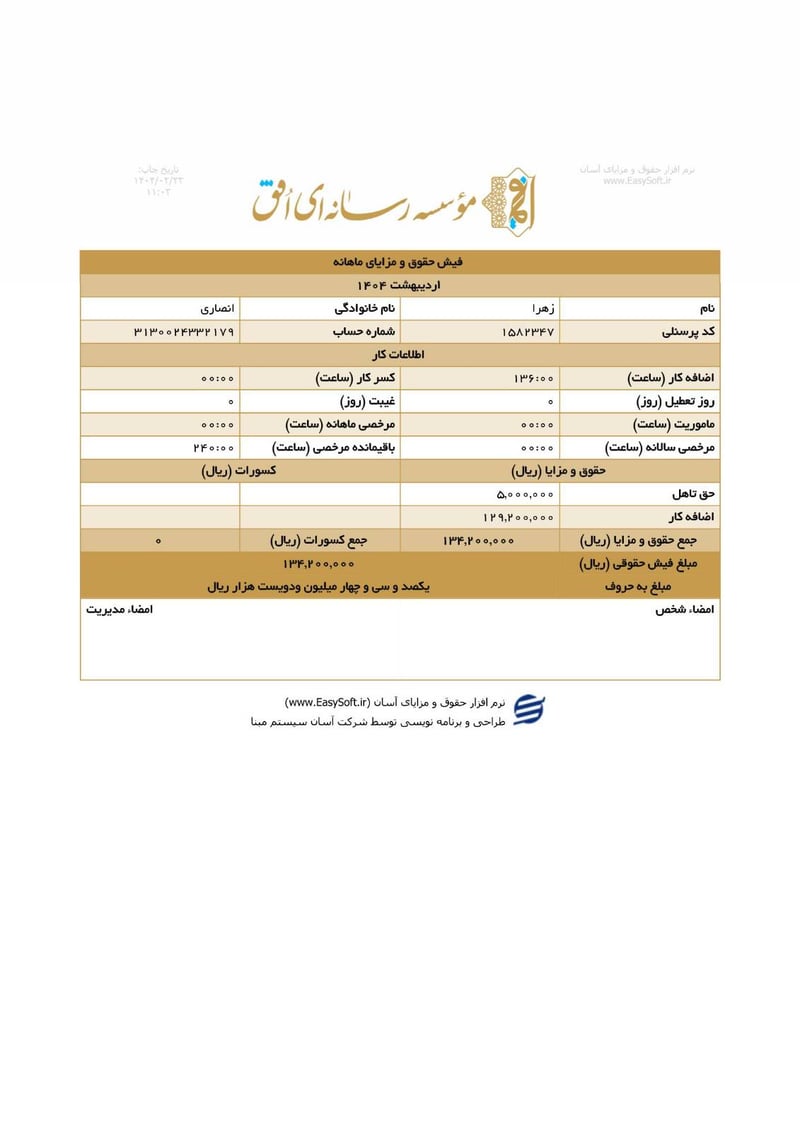
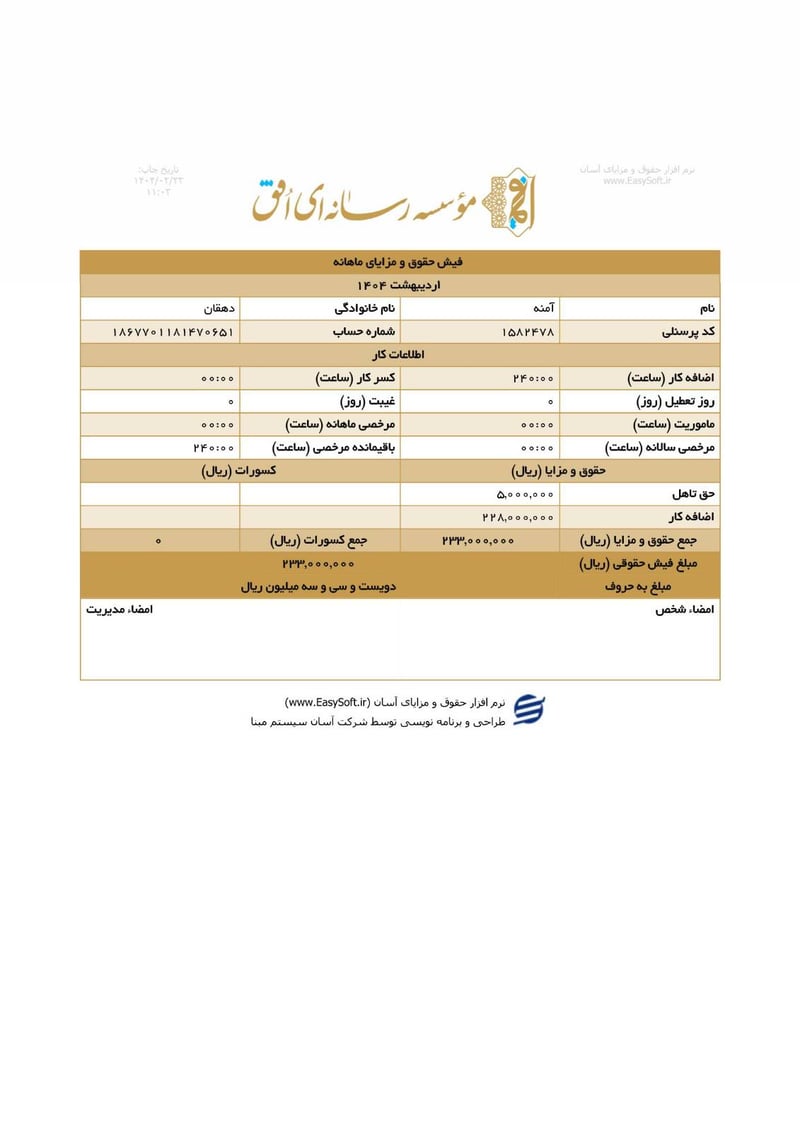
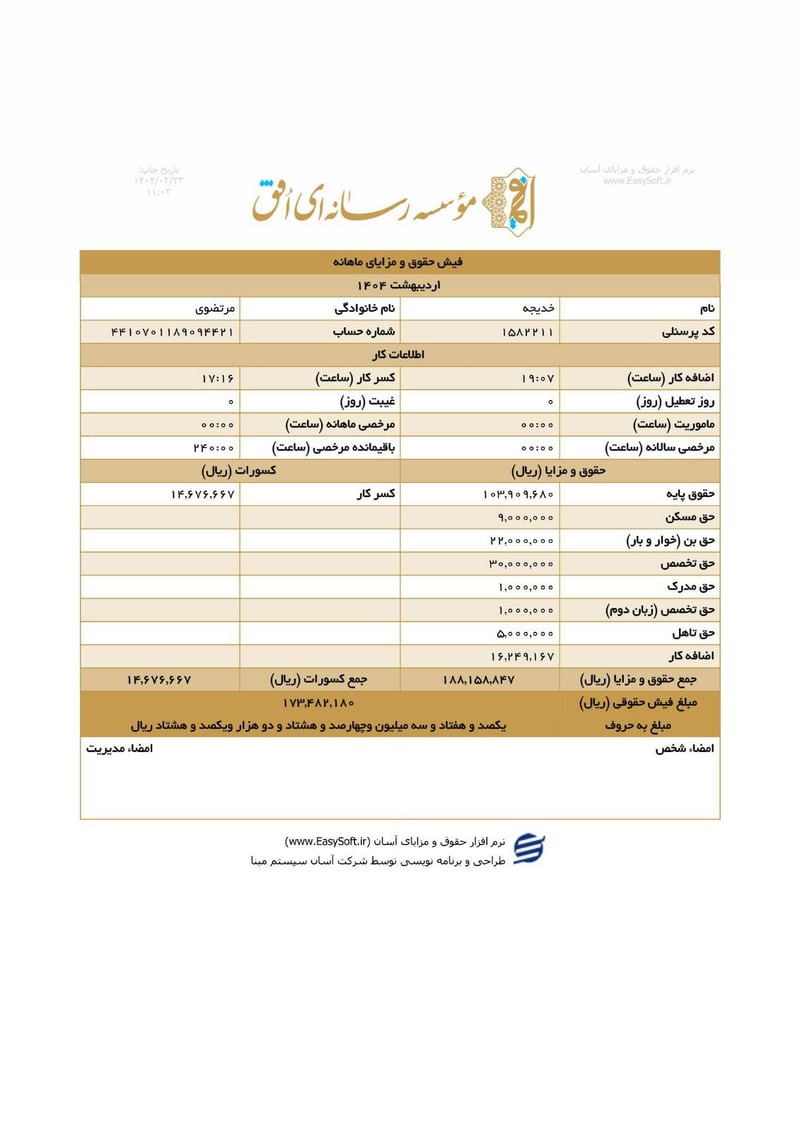
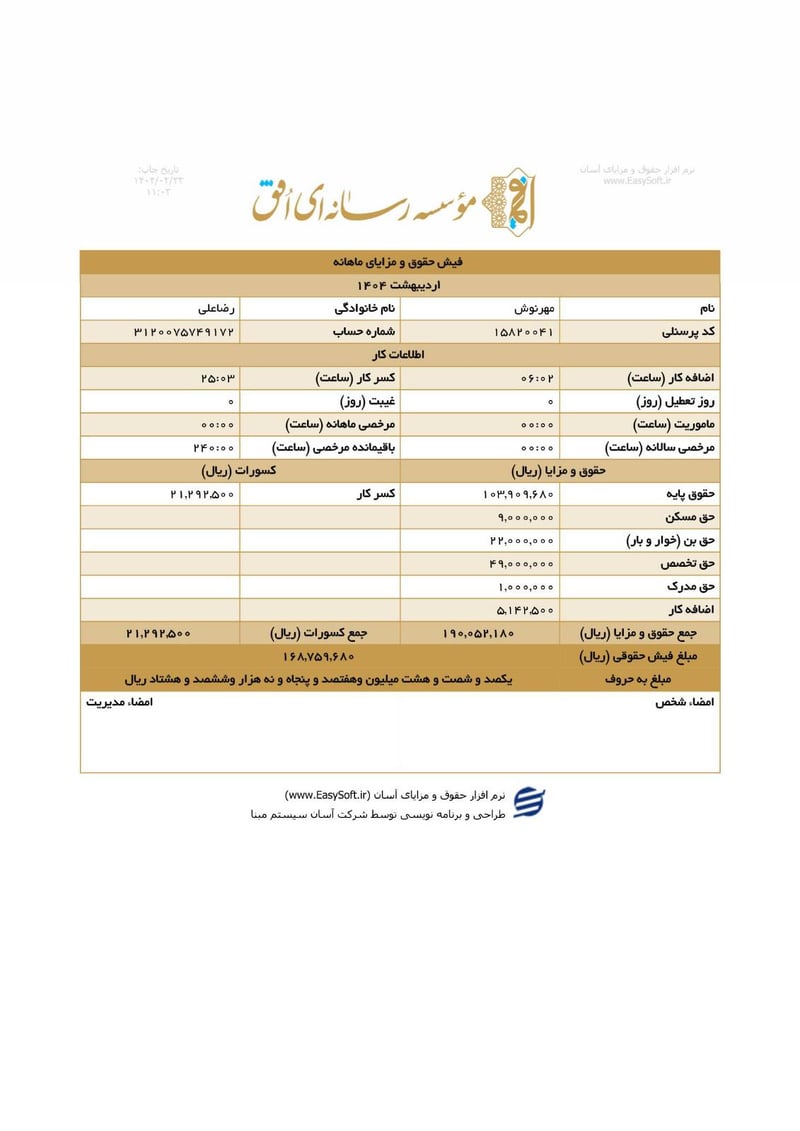
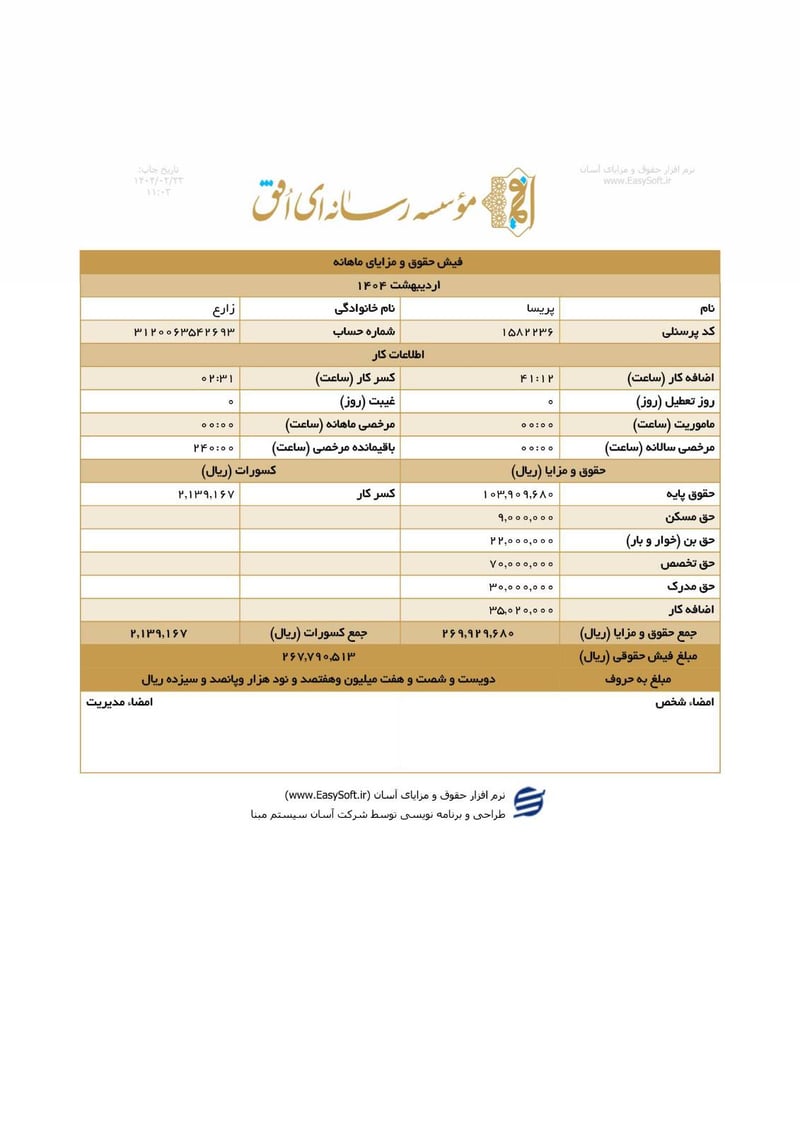
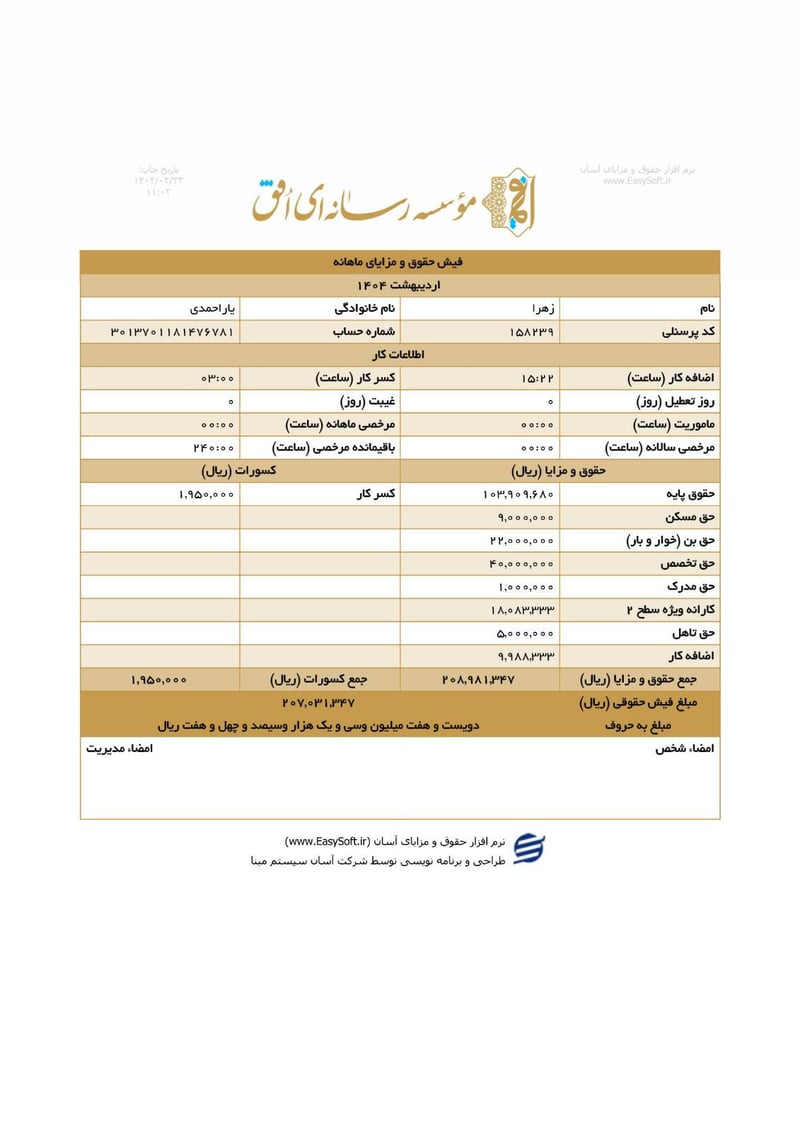
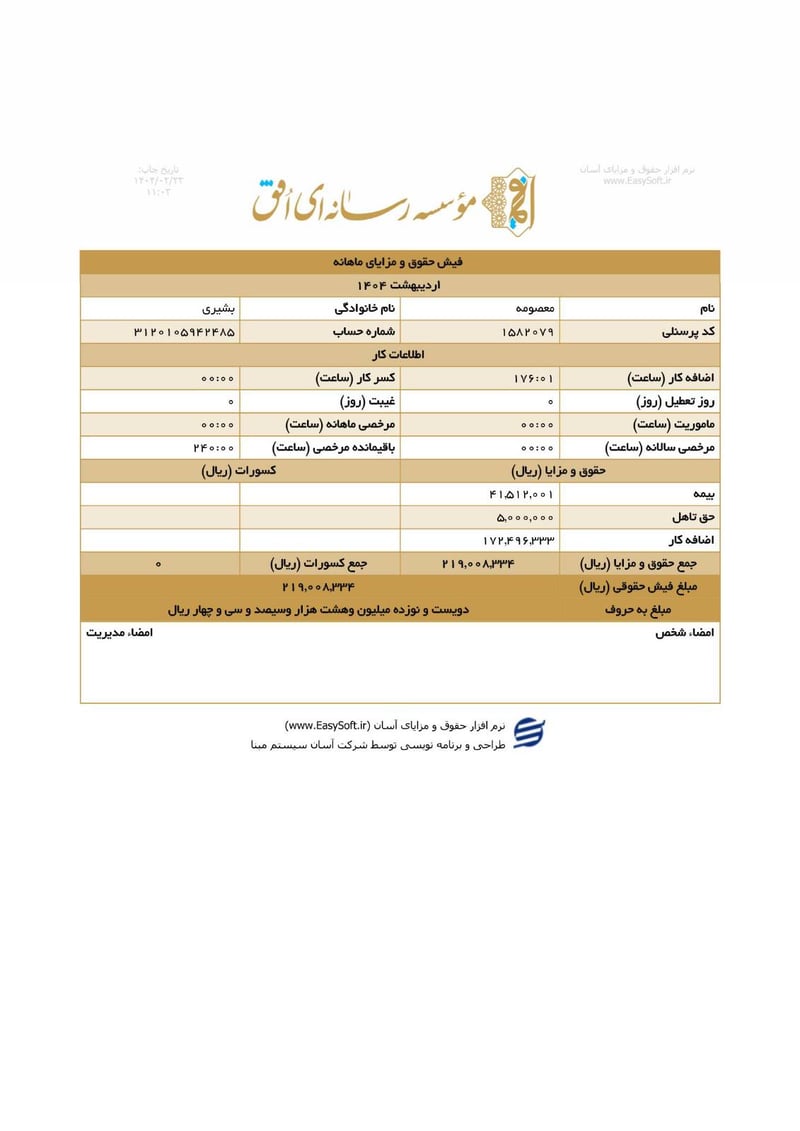
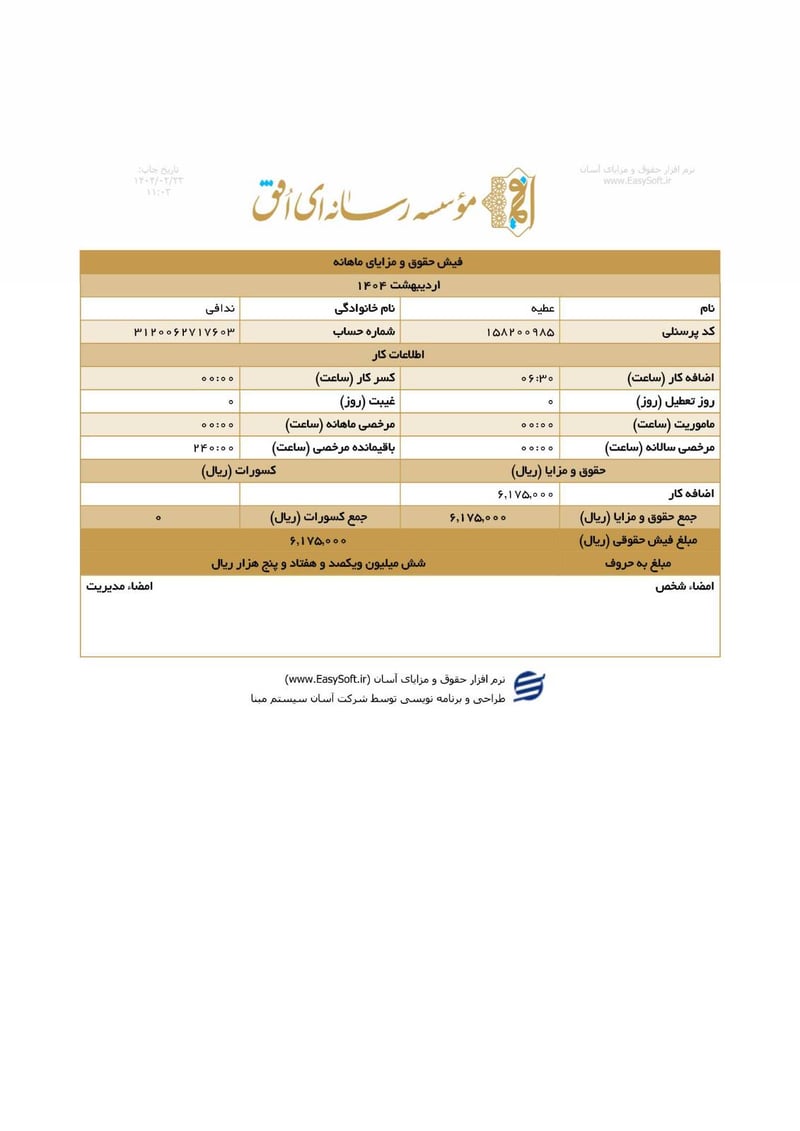
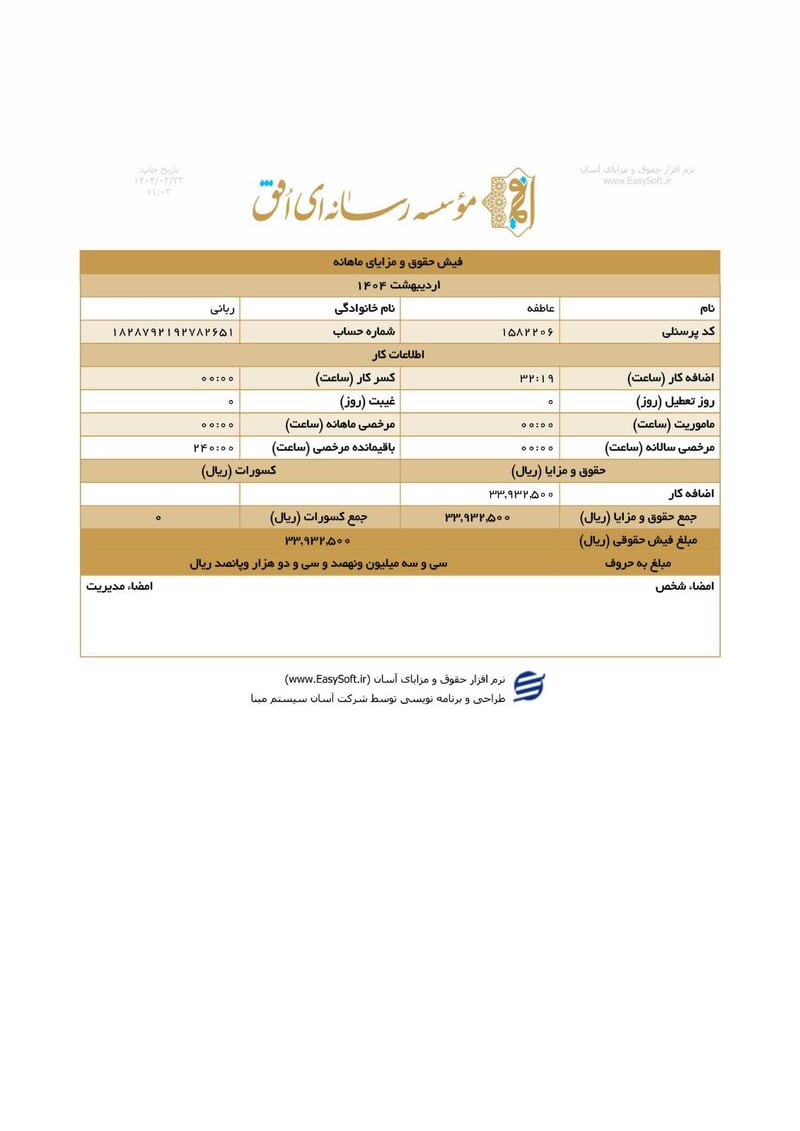
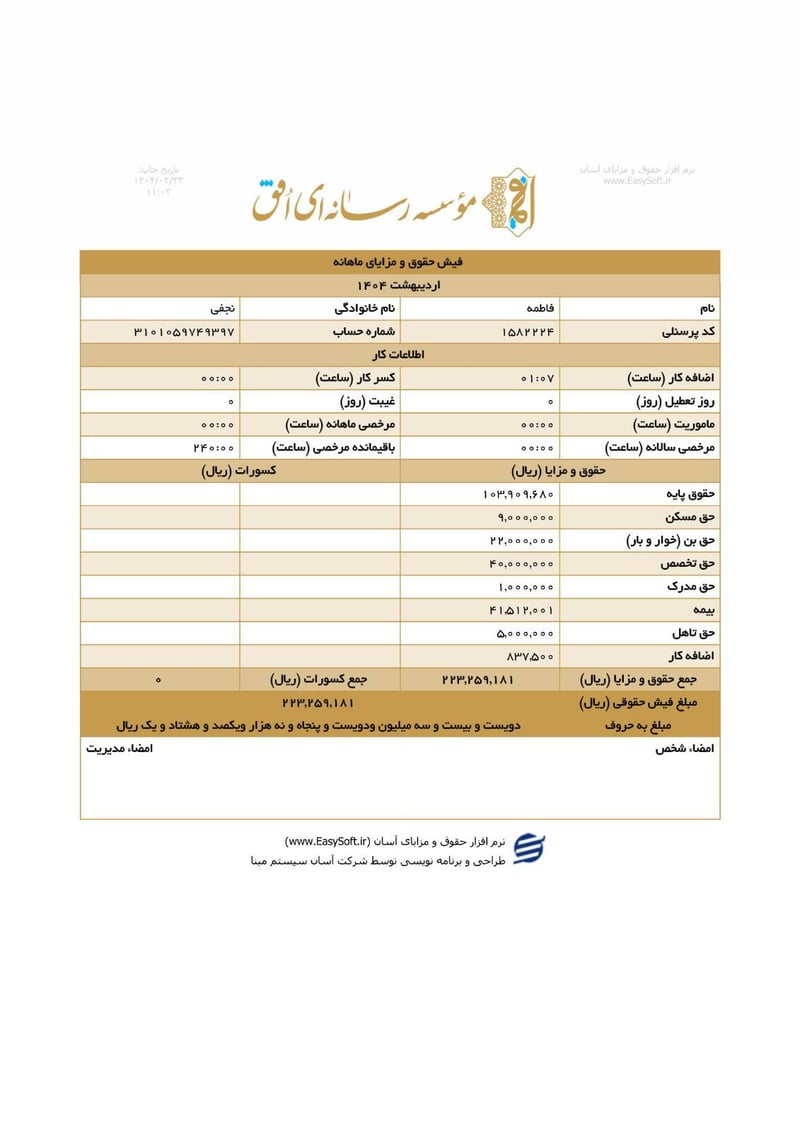
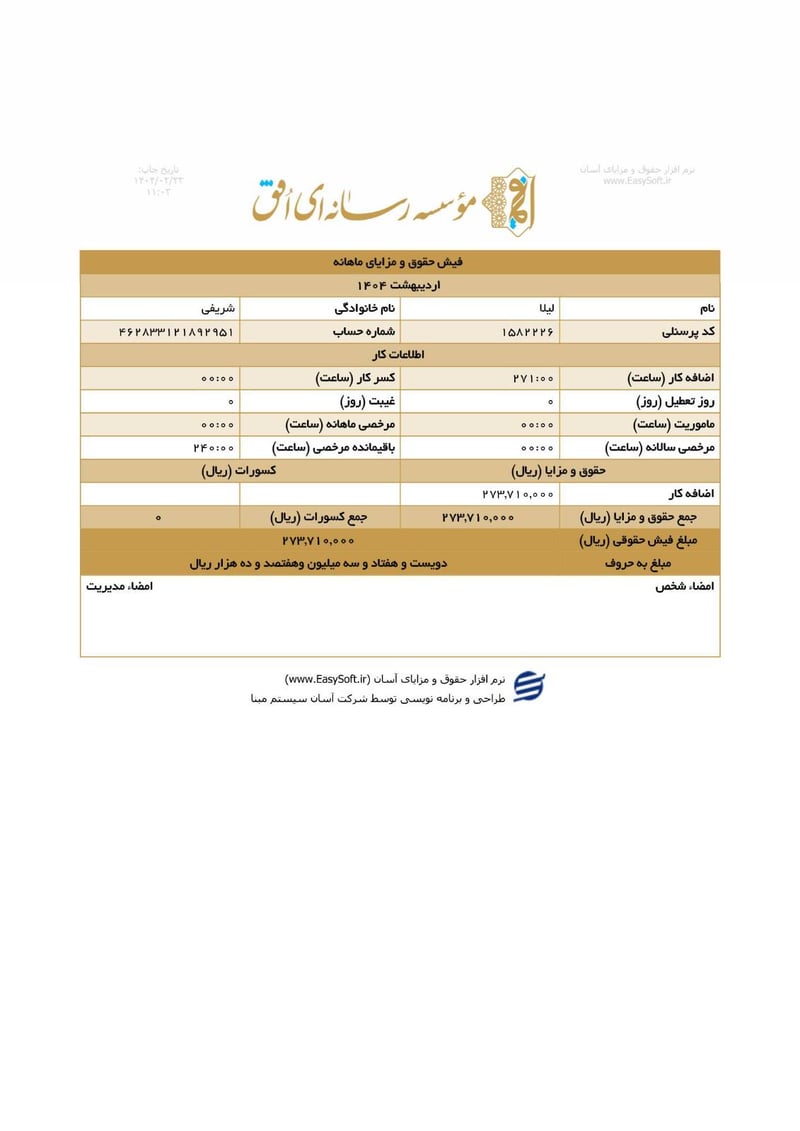
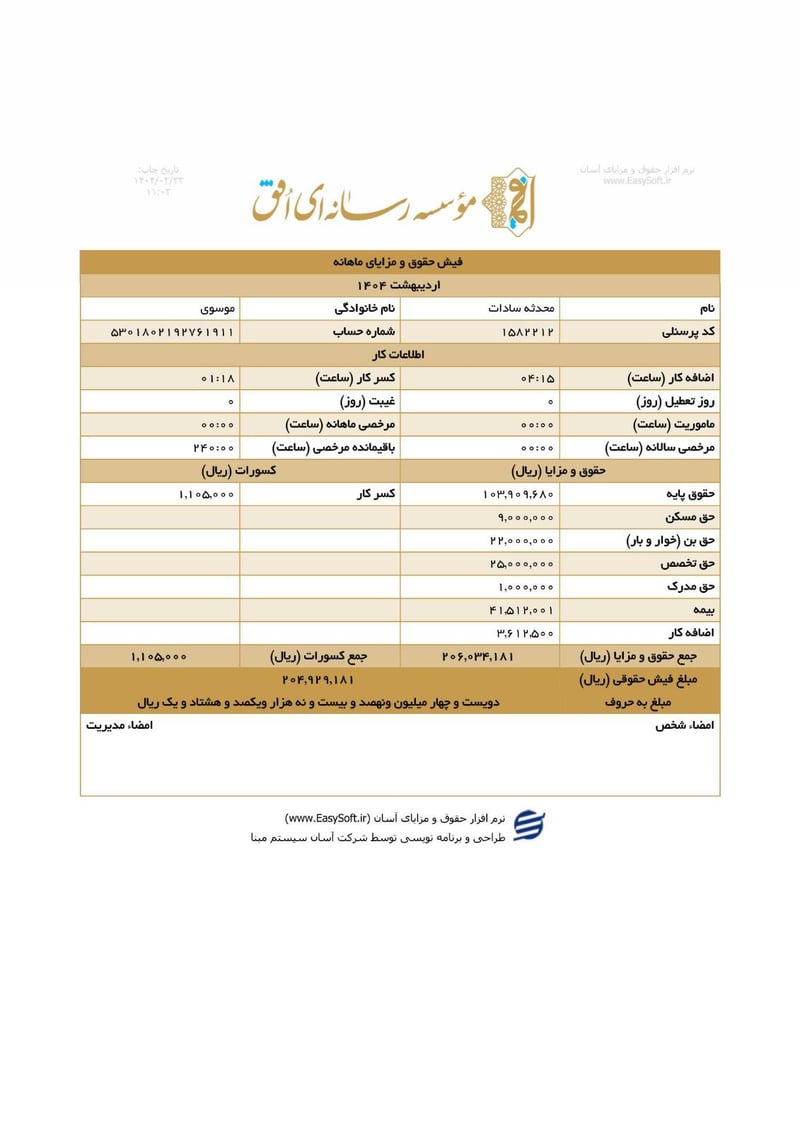
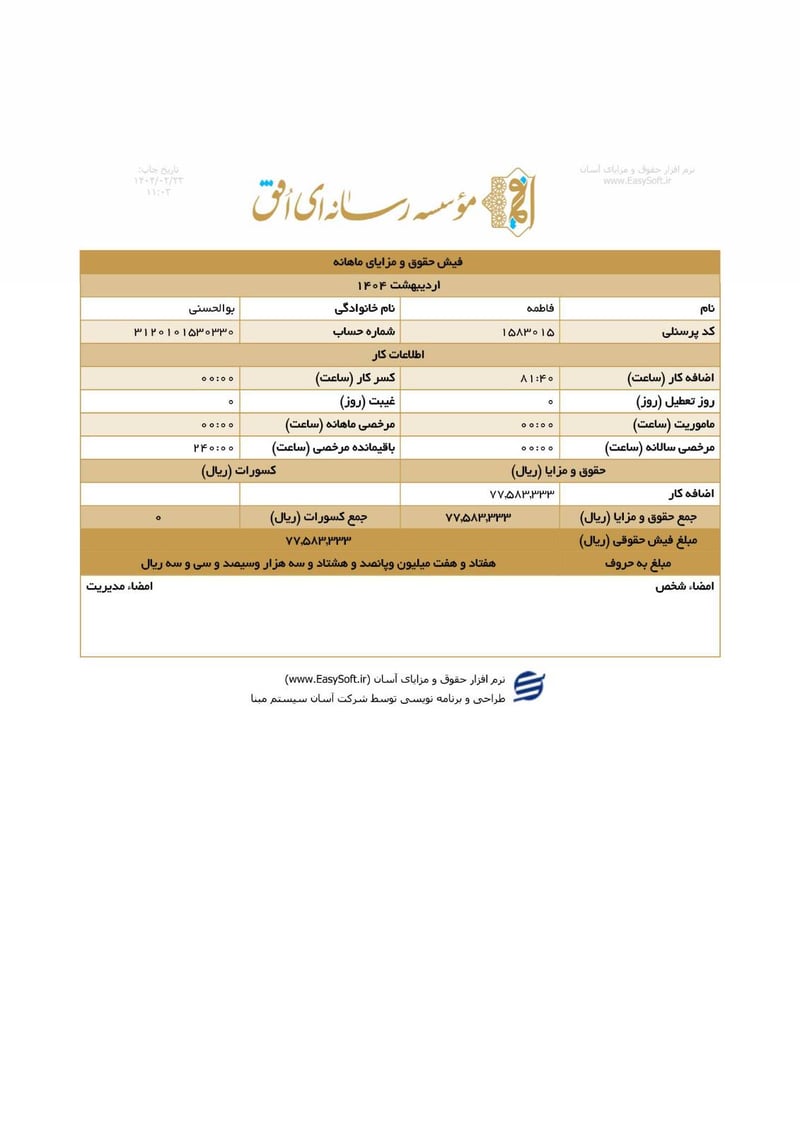
Sisters Team Payslips (Ordibehesht 1404 / April-May 2025)
Seventeen monthly salary slips (فیش حقوق و مزایای ماهانه) from the women's division reveal the following:
| Name | Bank Account | Net Salary (Rials) | Net Salary (USD) | |
|---|---|---|---|---|
| Leila Sharifi (لیلا شریفی) | 462833121892951 | 273,710,000 | ~$220 | |
| Parisa Zare (پریسا زارع) | 3120063542693 | 267,790,513 | ~$215 | |
| Sedigheh Bagher (صدیقه باقر) | 1862802100479691 | 235,071,681 | ~$189 | |
| Ameneh Dehghan (آمنه دهقان) | 1867701181470651 | 233,000,000 | ~$187 | |
| Azam Sadeghi (اعظم صادقی) | 3120069459601 | 231,512,180 | ~$186 | |
| Fatemeh Najafi (فاطمه نجفی) | 3101059749397 | 223,259,181 | ~$180 | |
| Masoumeh Bashiri (معصومه بشیری) | 3120105942485 | 219,008,334 | ~$176 | |
| Zahra Yarahmadi (زهرا یاراحمدی) | 3013701181476781 | 207,031,347 | ~$166 | |
| Mohaddeseh Sadat Mousavi (محدثه سادات موسوی) | 5301802192761911 | 204,929,181 | ~$165 | |
| Khadijeh Mortazavi (خدیجه مرتضوی) | 4410701189094421 | 173,482,180 | ~$140 | |
| Mehrnoosh Rezaali (مهرنوش رضاعلی) | 3120075749172 | 168,759,680 | ~$136 | |
| Zahra Ansari (زهرا انصاری) | 3130024332179 | 134,200,000 | ~$108 | |
| Narges Nadafi (نرگس ندافی) | 381877185030261 | 126,635,000 | ~$102 | |
| Fatemeh Bolhasani (فاطمه بوالحسنی) | 3120101530330 | 77,583,333 | ~$62 | |
| Hananeh Azizi (حنانه عزیزی) | 3120057291853 | 77,171,667 | ~$62 | |
| Atefeh Rabani (عاطفه ربانی) | 1828792192784651 | 33,932,500 | ~$27 | |
| Atieh Nadafi (عطیه ندافی) | 3120062717603 | 6,175,000 | ~$5 |
The salary distribution reveals a clear hierarchy within the Sisters Team. Senior operatives like Leila Sharifi and Parisa Zare earn over $200 monthly, while junior or part-time personnel such as Atieh Nadafi receive minimal compensation. The presence of two individuals with the surname Nadafi (Narges and Atieh) at different pay grades suggests possible familial recruitment patterns within the unit.
Brothers Team Financial Records
A separate spreadsheet documents eighteen male operatives in the Brothers Team, including their names and bank account numbers:
| Name | Bank Account | Net Salary (Rials) | Net Salary (USD) | |
|---|---|---|---|---|
| Davood Ghanbari (داوود قنبری) | 1810701451116417 | 216,248,062 | ~$174 | |
| Milad Gholami (میلاد غلامی) | 1051702183947351 | 150,000,000 | ~$121 | |
| Mohammad Rahimi Farab (محمد رحیمی فاراب) | 1870756659865614 | 136,000,000 | ~$109 | |
| Seyed Mohammad Keshvari Hashemi (سید محمد کشوری هاشمی) | 3120096233454 | 160,828,024 | ~$129 | |
| Alireza Moghadam (علیرضا مقدم) | 381870188841701 | 195,374,294 | ~$157 | |
| Ahmad Habri (احمد حبری) | 3130010221779 | 158,208,110 | ~$127 | |
| Akbar Boshagh (اکبر بسحاق) | 381870172465511 | 156,558,944 | ~$126 | |
| Amir Pour Ghadimi (امیر پور قدیمی) | 2228300188911 | 232,000,000 | ~$187 | |
| Arman Karami Goudarzi (آرمان کرمی گودرزی) | 302833121092311 | 225,561,840 | ~$181 | |
| Vahid Ghorbani Badakhsh (وحید قربانی بدخش) | 3130169041901 | 300,060,392 | ~$241 | |
| Erfan Hamidi Aref (عرفان حمیدی عارف) | 1810701169605181 | 214,560,962 | ~$173 | |
| Davood Akbari Mojadar (داوود اکبری مجدر) | 551233100109751 | 410,750,000 | ~$330 | |
| Davood Bayat (داوود بیات) | 185670154154661 | 48,000,000 | ~$39 | |
| Amir Ali Mansouri (امیر علی منصوری) | 748301234705 | 156,448,552 | ~$126 | |
| Omid Fallah (امید فلاح) | 3812701178325141 | 314,500,000 | ~$253 | |
| Mohammad Hassan Hassanzadeh Vozhdeh (محمد حسن حسن زاده وژده) | 3833701179296291 | 334,500,000 | ~$269 | |
| Hassan Arab Ahmadi (حسن عرب احمدی) | 5394874161641101 | 269,560,392 | ~$217 | |
| Alireza Feizi (علیرضا فیضی) | 4615701184072211 | 184,908,667 | ~$149 |
These records complement the organizational structure previously documented, confirming the approximate size of both teams and providing financial identifiers that enable sanctions authorities and financial investigators to trace IRGC payment networks.
Kashef Surveillance Platform: Expanded Capabilities Revealed
A second video obtained from the leaked data provides additional insight into the Kashef system (سامانه کاشف), the surveillance platform I previously documented. The new footage reveals the full scope of data integration across IRGC intelligence departments and the system's comprehensive tracking capabilities.
Intelligence Department Integration
The Kashef platform aggregates data from multiple IRGC Intelligence Organization departments, each responsible for specific geographic or demographic targets:
| Department | Designation | Focus Area | |
|---|---|---|---|
| 1530 | اداره 1530 - حوزه خلیج فارس | Persian Gulf Zone | |
| 1540 | اداره 1540 - رژیم صهیونیستی | Zionist Regime (Israel) | |
| 1550 | اداره 1550 - آمریکا | United States | |
| 1560 | اداره 1560 - اداره اتباع | Foreign Nationals |
Beyond these geographic divisions, the system incorporates specialized databases tracking:
- Foreign Travels of Iranians (سفرهای خارجی ایرانیان) - 777+ records visible in footage
- Dual Nationals (دو تابعیتی ها)
- Students Abroad (دانشجویان خارج از کشور)
- Visits to Diplomatic Premises (تردد به اماکن دیپلماتیک) - 494+ records visible
- Iranian Embassy Staff (کارکنان سفارتخانه های ایران)
- Companies Related to Foreign Entities (شرکت های مرتبط با خارج)
- International Journalists (خبرنگاران بین المللی)
Personal Data Collection
The video demonstrates the extensive personal information Kashef collects on each individual:
Identity Information:
- National ID (کد ملی)
- Passport number (شماره گذرنامه)
- Birth certificate number (شماره شناسنامه)
- Birth date and place
- Province of birth
Family Relations:
- Father's name (نام پدر)
- Mother's name (نام مادر)
- Spouse's name (نام همسر)
- Children's names (نام فرزند)
- Aliases (نام مستعار)
Contact and Professional:
- Phone numbers
- Email addresses
- Occupation
- Field of study
- Education level
Religious Profiling:
- Religion (دین)
- Sect, specifically Shia or Sunni (مذهب)
The inclusion of sectarian identification is notable. The system explicitly categorizes Iranian citizens by whether they are Shia or Sunni, enabling religious profiling of the population.
Embassy and Diplomatic Surveillance
The footage shows Kashef's capabilities for monitoring visits to foreign diplomatic premises in Tehran. Sample records reveal surveillance of embassies including Germany, Turkey, Japan, and South Africa. For each visit, the system records:
- Residence status of visitor
- Embassy or country visited
- Vehicle details (make, model, color)
- License plate number
- Date of visit
- Entry and exit times
- Intelligence notes
- Reference file number
The intelligence notes field contains annotations such as "Internal agents" and "Embassy agents," indicating human intelligence sources reporting on diplomatic visitors.
Border Crossing Records
The system maintains detailed records of all border crossings, including passport numbers, specific border points (such as Lar Airport and Shiraz Airport), and religious sect. Sample queries shown in the video track travel from Fars Province to the UAE, demonstrating the granularity of movement surveillance available to operators.
Cross-Reference Capabilities
A progress indicator visible in the footage shows a "merge process" (فرآیند ادغام) at 99% completion, indicating the system's ability to cross-reference and combine records across multiple databases to build comprehensive profiles on individuals of interest.
The IAEA Document: A Twenty-Year Connection
Among the files retrieved from Department 40's compromised infrastructure, one document stands apart from the operational files. This classified 2004 communication from Iran's Ministry of Intelligence was found on the personal computer of Abbas Rahrovi, the department head I identified in previous reporting. Rahrovi's machine contained highly classified Revolutionary Guards documents beyond the unit's cyber operations. This document reveals that Iranian intelligence obtained confidential IAEA inspection documents two decades ago.
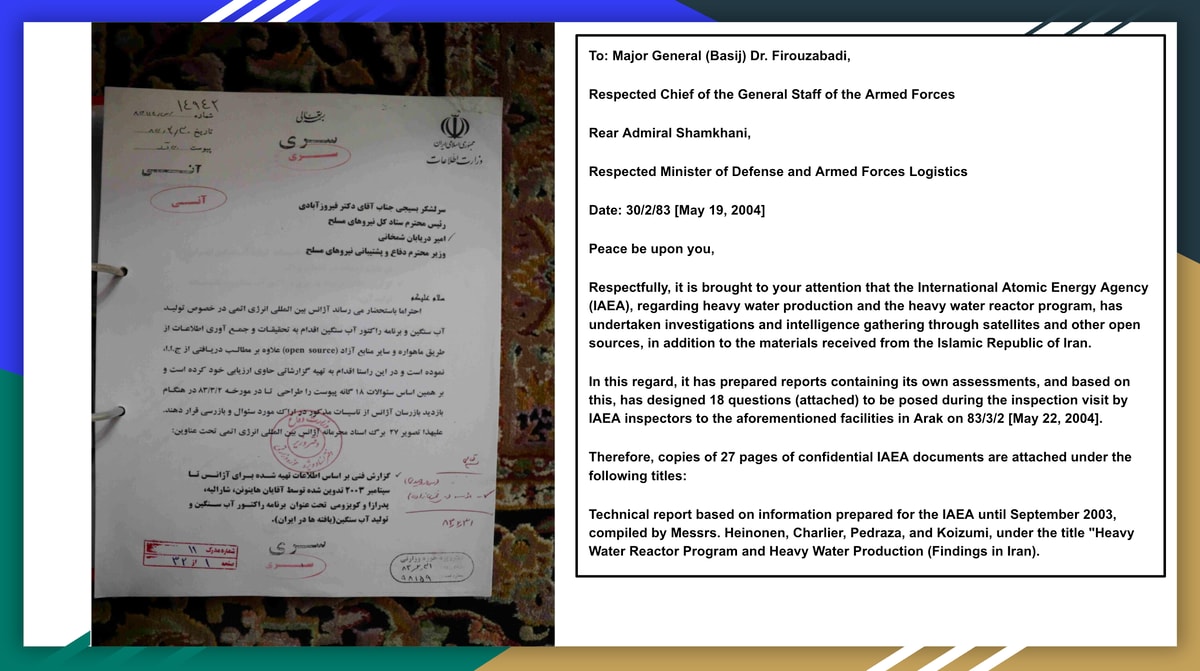
The letter, classified SECRET with URGENT priority, dated May 19, 2004, was addressed to Major General Firouzabadi, Chief of the General Staff of the Armed Forces, and Admiral Shamkhani, Minister of Defense. It notifies senior military leadership that Iranian intelligence had obtained internal IAEA documents regarding heavy water production and the heavy water reactor program at Arak. The document confirms that 27 pages of confidential IAEA documents were attached, including a technical report compiled by Heinonen, Charlier, Pedraza, and Koizumi under the title "Heavy Water Reactor Program and Heavy Water Production (Findings in Iran)." The letter also references 18 questions the IAEA had prepared to pose during their May 2004 inspection visit to Arak.
The Olli Heinonen Connection
The first name listed among the IAEA report authors is Olli Heinonen, who served as IAEA Deputy Director-General for Safeguards from 2005 to 2010. Heinonen was the agency's chief nuclear inspector and played a central role in investigating Iran's nuclear program during this period.

In my previous reporting on the Department 40 leak, I documented that Heinonen appears on the unit's target list for surveillance and potential assassination operations. The department that conducts cyber espionage also maintains target packages on individuals for kinetic operations, and Heinonen was identified as a high-priority target.
This 2004 document, stored on the same network infrastructure, provides context for why Heinonen became a target. As the lead author of IAEA technical assessments on Iran's nuclear program and the architect of inspection questions, Heinonen possessed detailed knowledge of what the agency knew, and what it suspected, about Iranian nuclear activities. The fact that Iranian intelligence obtained his confidential reports demonstrates both the sensitivity of his work and Iran's interest in understanding exactly what he knew.
The Handwritten Annotations
The document contains handwritten marginal notes that reveal who was involved in handling this intelligence. Two names appear: "سردار وحیدی" (Sardar Vahidi) and "موسسه فخریزاده" (Fakhrizadeh Institute), with a date of 83/2/31 (May 20, 2004)
Ahmad Vahidi was IRGC Quds Force commander at the time, later served as Minister of Defense (2009-2013), and is currently Iran's Minister of Interior. He remains wanted by Interpol for his alleged role in the 1994 AMIA Jewish center bombing in Argentina that killed 85 people.
The reference to "Fakhrizadeh Institute" is more significant. Mohsen Fakhrizadeh headed Iran's AMAD Project, the covert nuclear weapons program. Israeli intelligence described him as the "father of the Iranian nuclear bomb." He was assassinated near Tehran in November 2020 in an operation widely attributed to Israel.

That Fakhrizadeh's organization appears handwritten on a 2004 document concerning IAEA inspections of nuclear facilities at Arak directly connects his institute to the nuclear program years before his role became publicly known internationally. This document sat on the computer of the man whose unit later compiled target lists that included nuclear inspectors.
Why This Document Was on Rahrovi's Computer
The presence of a twenty-year-old Ministry of Intelligence document on the personal computer of an IRGC cyber operations commander raises questions about information sharing between Iranian intelligence agencies, and about Rahrovi's role beyond hacking operations. Department 40 operates under the IRGC Intelligence Organization, separate from the Ministry of Intelligence (MOIS) that authored this document.
That Rahrovi personally retained this classified material alongside other highly sensitive Revolutionary Guards documents suggests he was not merely a technical operations manager. The document may have been provided as background material when Heinonen was designated as a Department 40 target. Its presence on Rahrovi's machine, rather than in general network storage, indicates the department head's direct involvement in operations concerning individuals connected to Iran's nuclear program oversight.
Implications
The exposure of salary records transforms abstract threat actor designations into documented employment relationships. These thirty-five individuals now have their financial ties to IRGC cyber operations confirmed through their own payroll records. Combined with previously leaked Iranian data, researchers can now cross-reference these bank account numbers against other data points to build more complete profiles on each operative, potentially uncovering additional identities, addresses, and connections not visible in the Department 40 files alone.
The expanded Kashef footage demonstrates that Iranian surveillance infrastructure extends far beyond cyber operations. The system's integration of religious sect data, embassy visit tracking, and cross-referencing capabilities reveals a comprehensive domestic surveillance apparatus targeting Iranian citizens based on their travel, contacts, and even their branch of Islam.
The IAEA document provides historical depth to Department 40's targeting of Olli Heinonen. This was not arbitrary selection. Heinonen authored the confidential assessments that Iranian intelligence successfully obtained, making him a person of enduring interest to a regime concerned with understanding and countering international nuclear oversight.
The materials continue to emerge from the same network access that exposed Charming Kitten's operations. Each disclosure adds detail to the picture of how Iran's cyber capabilities integrate with broader intelligence and security objectives, from compensating operatives through front company payrolls to maintaining target packages on international officials who scrutinized the nuclear program two decades ago.



