In what appears to be one of the most significant breaches of an Iranian state-sponsored hacking operation to date, an anonymous source has published internal documents, employee information, and operational records from Charming Kitten, an advanced persistent threat group linked to Iran's Islamic Revolutionary Guard Corps.
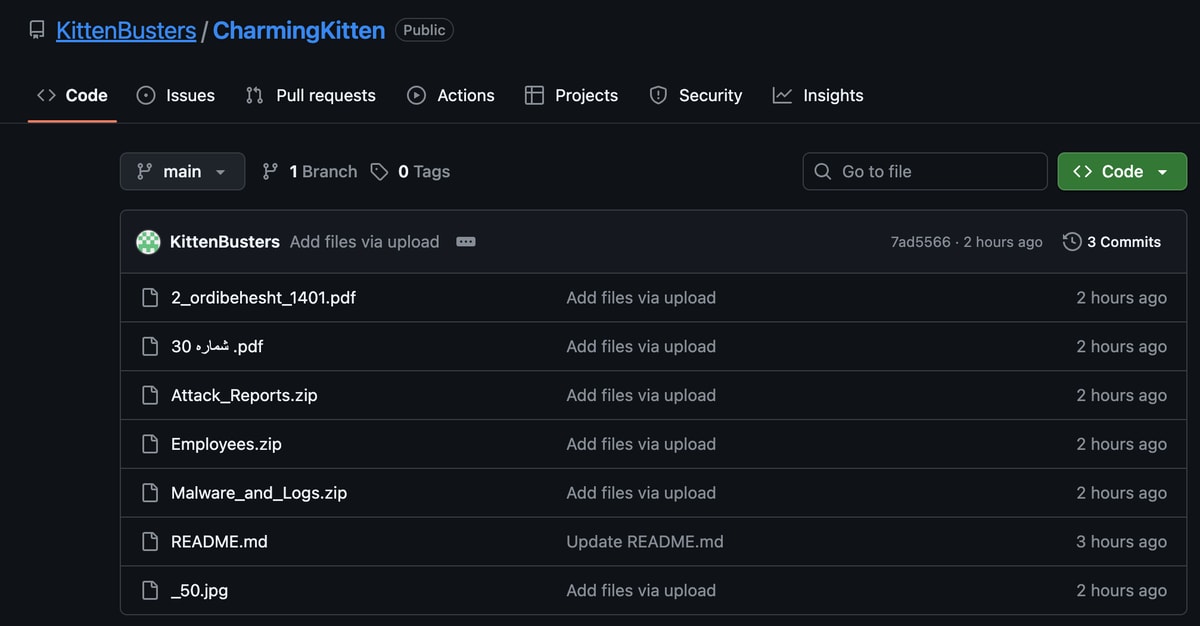
The leak, posted to GitHub under the name "KittenBusters," includes hundreds of files spanning attack reports, daily operational logs, internal communications, malware samples, and photographs of personnel allegedly working for the group. The disclosure identifies Abbas Rahrovi, also known as Abbas Hosseini, as the operation's leader, providing his Iranian national identification number [4270844116] and alleging he manages the hacking unit through a network of front companies.
A Group With Reach Across the Middle East
Charming Kitten, tracked by various cybersecurity firms under names including APT35, Phosphorus, and Newscaster, has operated for over a decade as one of Iran's most active cyber-espionage units. Western intelligence agencies and security researchers have tied the group to Iran's Intelligence Organization of the Islamic Revolutionary Guard Corps, specifically its counterintelligence division known as Unit 1500.
The group has historically focused on intelligence collection rather than destructive attacks. Their targets have included dissidents, journalists, academics, and government officials across the Middle East and beyond. Microsoft, Google, and Facebook have all publicly disclosed efforts to disrupt Charming Kitten operations over the years, typically involving sophisticated social engineering and credential harvesting campaigns.
What distinguishes this group from other Iranian cyber actors is its patient, methodical approach. Charming Kitten operators often spend weeks or months building trust with targets through fake personas, posing as journalists, conference organizers, or fellow academics before deploying malicious links or documents.
Inside the Breach
The leaked materials, organized in a detailed directory structure, reveal the operational tempo of a state-sponsored hacking unit. Daily reports span multiple years, with file names indicating activities from the Persian calendar year 1403, corresponding to 2024 in the Gregorian calendar. Other documents date back to May 2022, suggesting the leak encompasses at least two years of operations.
One folder labeled "All_Proxy_Shell_Targets" contains subfolders for Iran, South Korea, Kuwait, Turkey, Saudi Arabia, and Lebanon. The files appear to document exploitation of Microsoft Exchange servers using ProxyShell vulnerabilities. The targeting of exchange servers aligns with previous Charming Kitten tactics of compromising email systems to gain persistent access to communications.
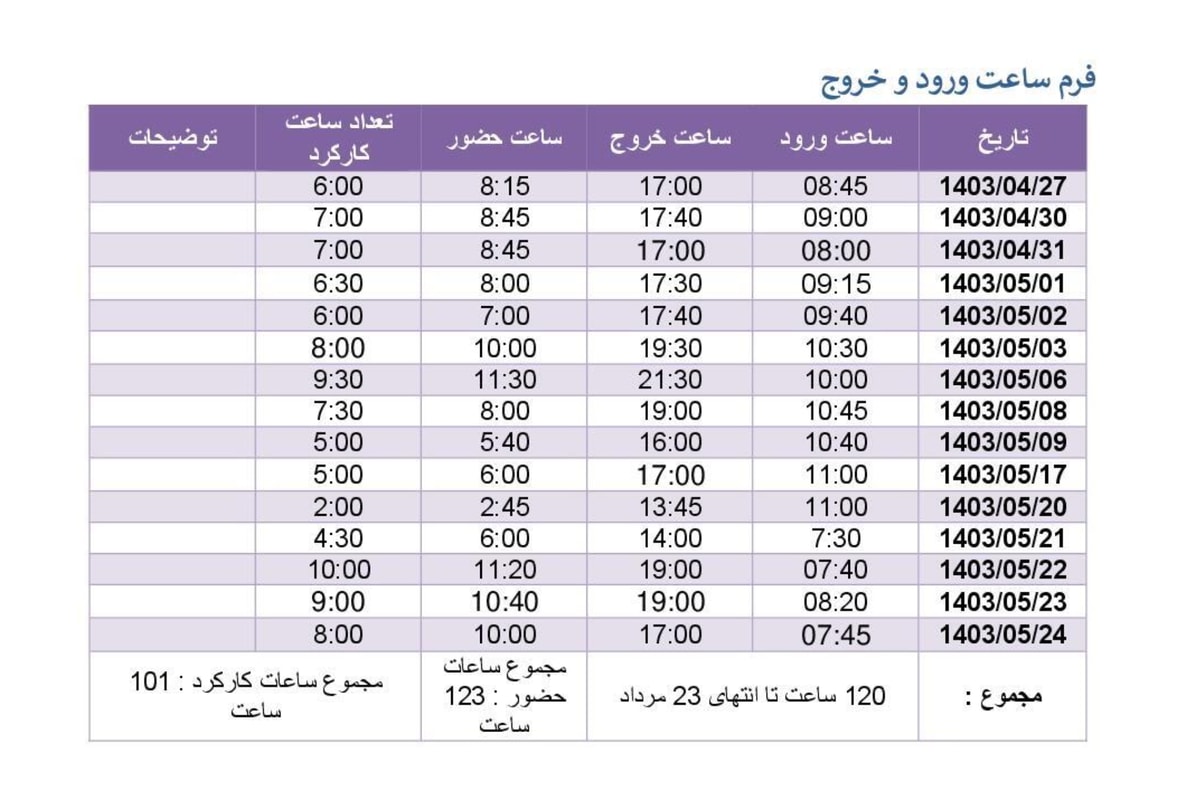
The leak includes folders labeled "Attack Reports" with documents in Persian, many featuring the phrase "گزارش عملکرد ماهانه" (monthly performance report) in their filenames. Individual daily reports from operators with names like Majid, Mehyar, and Hosein detail mundane tasks: monitoring Instagram accounts, conducting OSINT collection, setting up phishing infrastructure. The reports even track hours worked, revealing the bureaucratic routine of state-sponsored hacking.
Perhaps most striking is a folder containing employee photographs, with Persian-language filenames that appear to include personal names. The inclusion of this material represents an extraordinary breach of operational security for an intelligence unit that has historically operated in the shadows.
Additional folders labeled "Malware_and_Logs" and "CMPGN_PST" suggest the leak contains both the tools used in operations and logs of campaign activities. The personnel files include ID cards with photographs and full names - conference entry badges and internal access credentials that identify specific individuals by name.
Targeting Iranian Citizens Abroad
According to the leak's introduction, Charming Kitten has devoted significant resources to tracking Iranians identified as "regime opponents" both inside Iran and in other countries. This targeting of diaspora communities and political activists has been a consistent pattern in Iranian cyber operations, often running parallel to surveillance and intimidation campaigns in the physical world.
Human rights organizations have long documented how the Iranian government uses both digital and physical means to monitor, harass, and in some cases harm dissidents living abroad. The revelation that a military intelligence unit maintains detailed operational records of such surveillance provides rare documentation of the bureaucratic machinery behind these efforts.
The leak arrives at a moment of heightened tension over Iran's domestic repression and regional activities.
Questions of Attribution and Motive
The identity and motivation of whoever is behind "KittenBusters" remains unknown. The GitHub account promises to release additional information "every few days" and provides an email address for contact. The decision to expose an intelligence operation of this nature carries obvious risks, suggesting either insider access or a significant breach of the group's operational security.
Previous leaks of Iranian cyber capabilities have come from various sources. In some cases, Israeli intelligence has been suspected of role in exposing Iranian operations. In others, disaffected insiders or rival factions within Iran's complex intelligence apparatus have been suggested as possibilities. Cybersecurity researchers have also occasionally gained access to Iranian operational materials through their own technical investigations.
The leak's level of detail and organization suggests whoever compiled it had systematic access to internal systems over an extended period. The inclusion of personnel photographs, internal chat logs, and operational documents from multiple timeframes indicates this was not a one-time breach but sustained access to core systems.
This leak delivers a serious blow to Iran's intelligence apparatus. Countries and organizations on the targeting lists now have concrete evidence for attribution, cybersecurity researchers will spend months analyzing the materials, and the identified individuals can no longer operate in the shadows. That a hacking unit with these resources could be compromised so thoroughly suggests even the most sophisticated intelligence operations remain vulnerable to insider threats or external breaches. KittenBusters has promised more releases are coming - if they materialize, they could provide an unprecedented look inside the machinery of state-sponsored espionage.



