A massive leak of internal documents has blown the cover off one of Iran's most active hacking groups. For years, the cybersecurity community tracked them as APT35, Charming Kitten, Fresh Feline. Now we know exactly who they are, where they work, and who they're targeting.
If you've followed my previous reporting on this group, you already know they've targeted journalists, activists, and researchers with sophisticated phishing campaigns. You've seen the fake interview requests, the compromised email accounts, the social engineering tactics. But until now, we only knew what they did. We didn't know who they were.
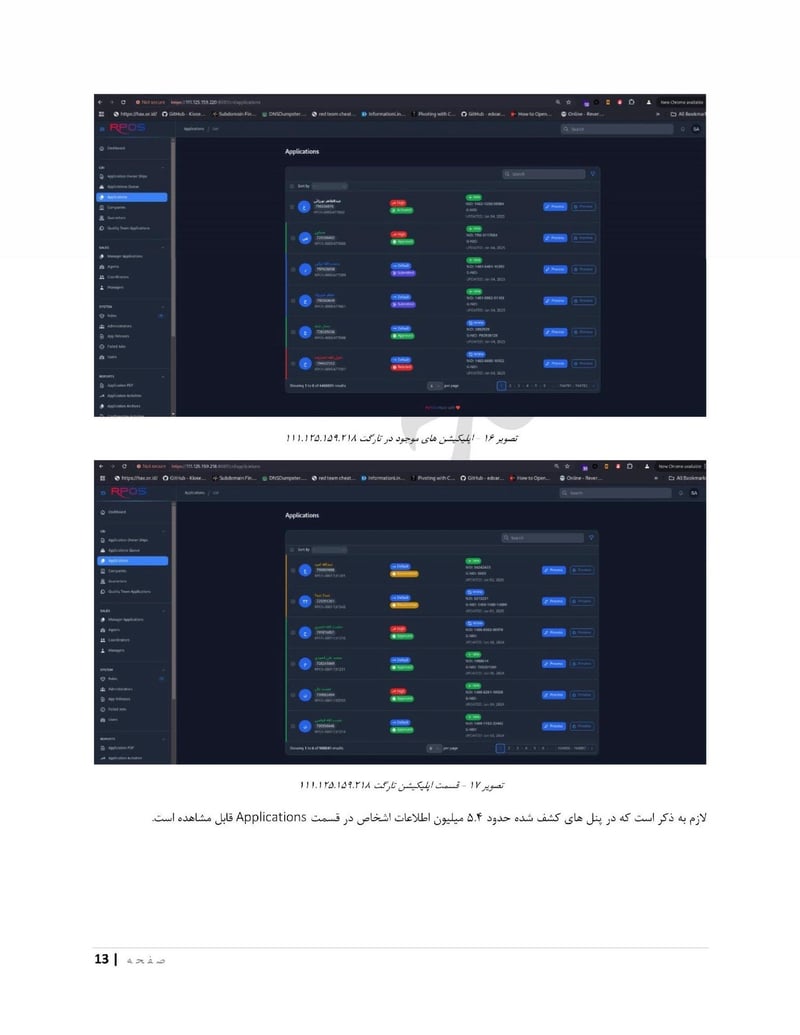
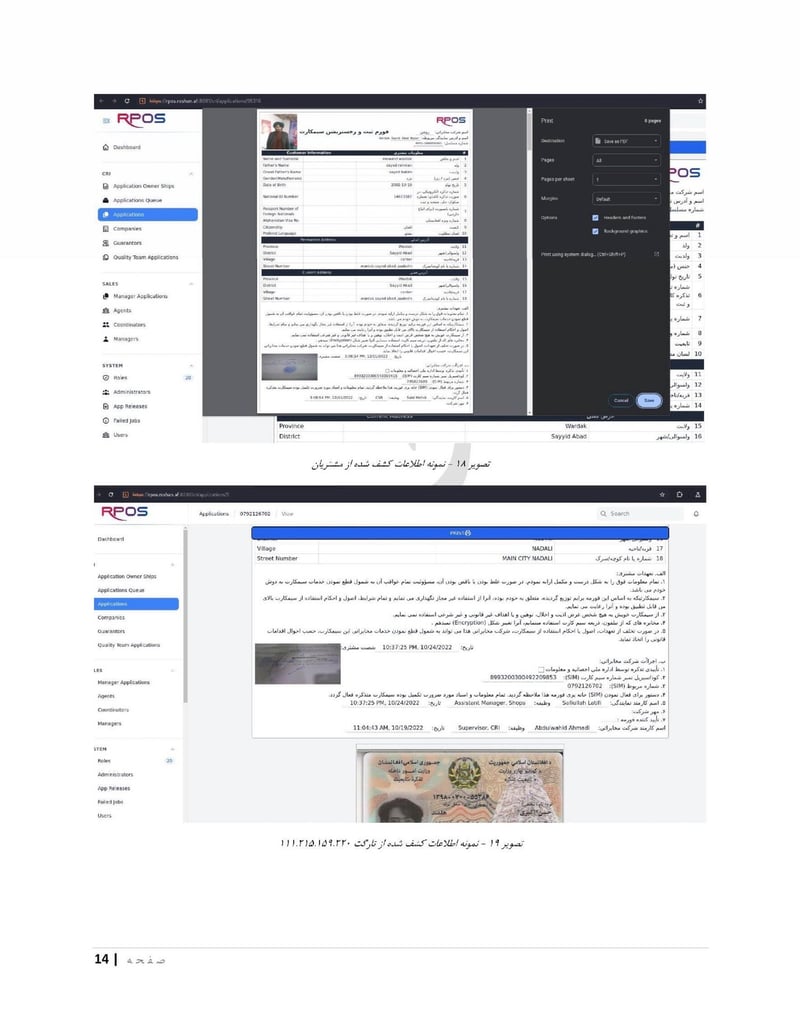
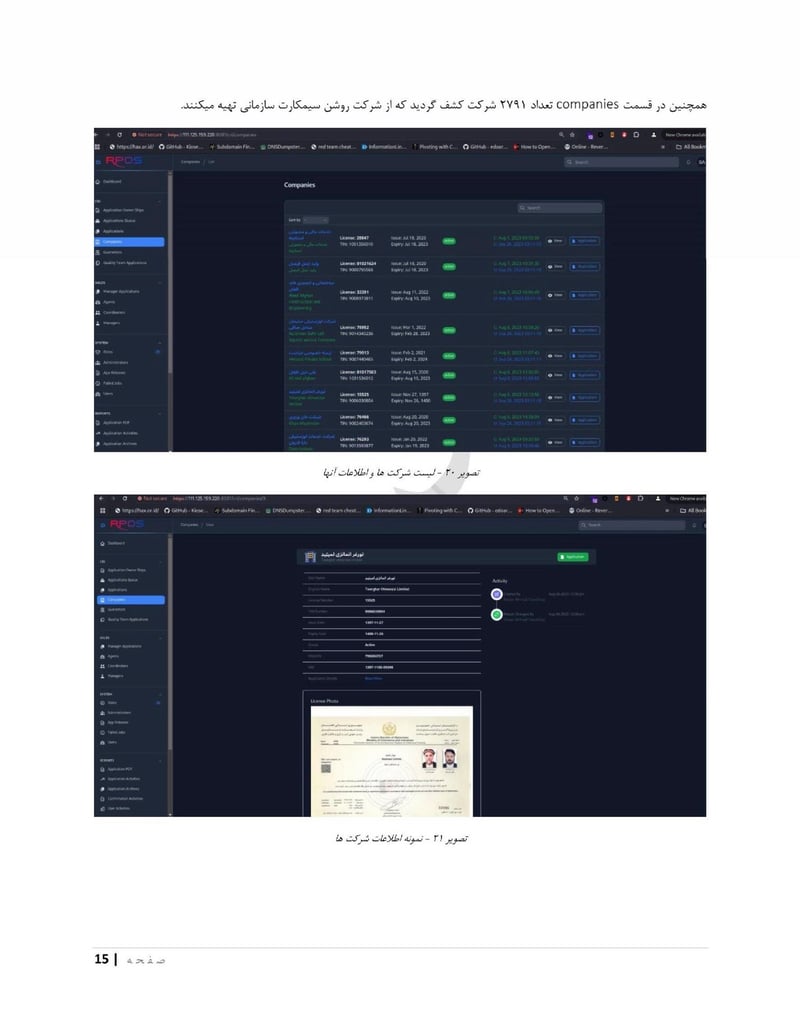
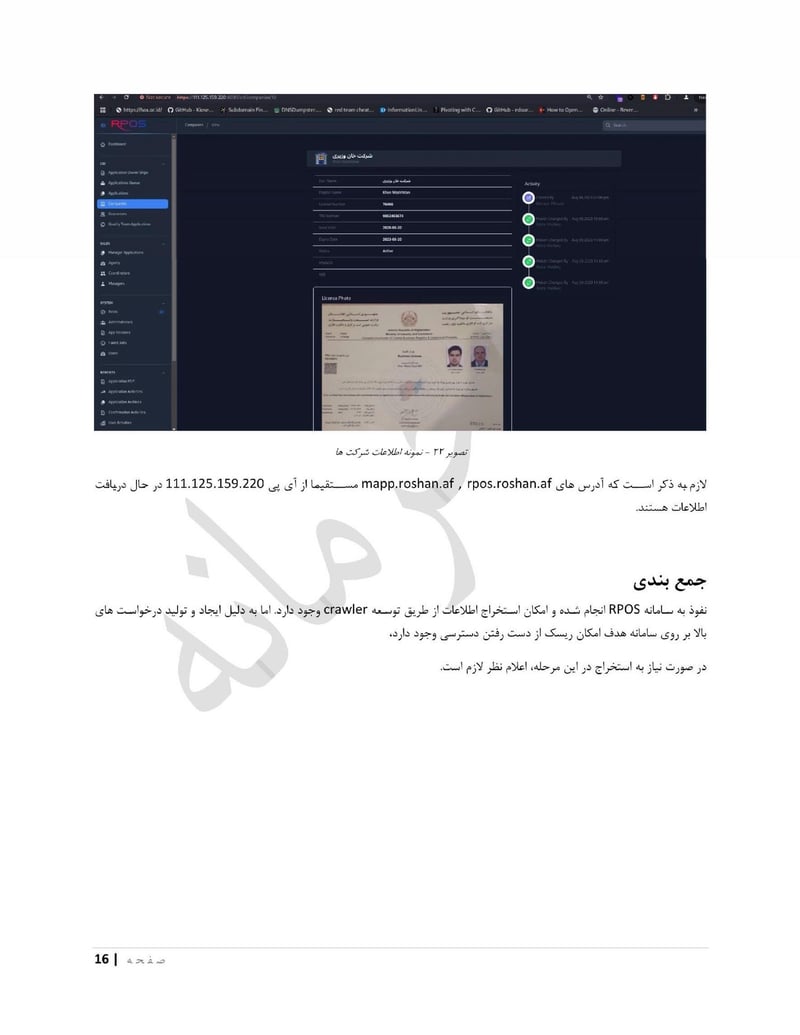
You can view their supplementary information on the website iranianthreatactors.com
The leaked files reveal everything: names, national ID numbers, photographs, facility addresses, organizational charts, attack reports, internal videos of their surveillance systems, and even drone test footage. The complete exposure of an IRGC cyber unit that has spent years attacking journalists, government agencies, and critical infrastructure across the Middle East, Europe, and North America.
The exposure also reveals the direct connection between cyber operations and terrorism. These hackers build the intelligence infrastructure that enables assassination operations. Every breached airline database, every compromised hotel booking system, every hacked medical clinic feeds into a system designed to locate and kill people the Iranian regime considers enemies.
The Man Behind the Curtain: Abbas Rahrovi
Meet Abbas Rahrovi (عباس رهروی). Inside the IRGC, they call him "ACS."

Rahrovi runs "Department 40," the cyber arm of the IRGC's Intelligence Organization Division 1500. His national ID is 4270844116, son of Rasul Rahrovi, born in Zanjan. But you won't find his real name on any company documents. Instead, he operates under aliases. Mekhaeel Hosseini (ID: 4289995632) for official contracts and front company registrations. Abbas Hoseini when procuring explosives for drones.
The leaked documents include correspondence between Rahrovi and Division 1500 leadership requesting salary increases for his cyber personnel. They also show he registered his alias identity with a separate national ID number, creating a complete second identity for operational purposes.
Today he commands over 60 operatives working from five facilities across Iran. His wife, Niloofar Bagheri (ID: 4270932864), runs the women's division and serves as CEO of one of the front companies. The leaked payroll documents include both their national ID numbers, photographs, and detailed role descriptions.

Organizational Structure and Command Hierarchy
The leaked organizational chart reveals Department 40's formal position within the IRGC Intelligence Organization.
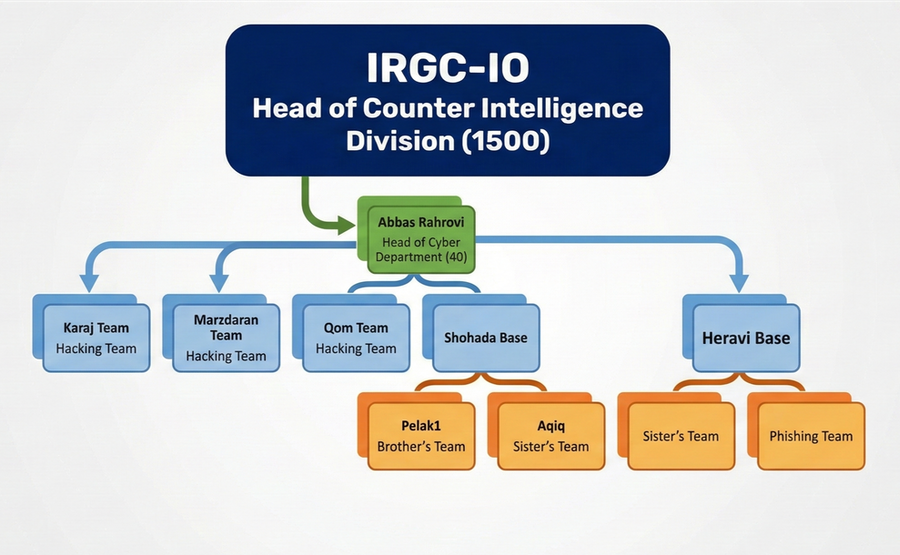
Division 1500 sits at the top of the hierarchy. This is the IRGC's intelligence division responsible for foreign operations. Abbas Rahrovi reports directly to Division 1500 leadership, receiving tasking and providing intelligence products.
Under Rahrovi, the structure branches into two main categories: hacking teams and operational bases.
Hacking Teams:
- Karaj Team - Offensive cyber operations
- Marzdaran Team - Offensive cyber operations
- Qom Team - Offensive cyber operations
Operational Bases:
- Shohada Base - Houses Pelak1 (Brother's Team) and Aqiq (Sister's Team)
- Heravi Base - Houses Sister's Team contingent and dedicated Phishing Team
Each team has designated leaders, codenames, and operational responsibilities. The chart shows a professional military-style organization, not a loose collective of hackers.
Operational Budget and Personnel Security
A leaked salary request document reveals Department 40 has been operational since at least 2017.

The Teams: Brothers, Sisters, and Hackers
Department 40 isn't a loose collection of hackers. It's a structured operation with specialized teams, codenames, and clear chains of command.
The Sister's Team (واحد خواهران)
Twenty women. Codename: Aqiq.
Led by Niloofar Bagheri, Rahrovi's wife, this team handles translation, social engineering, and psychological warfare. The leaked documents reveal their direct involvement in intelligence operations that extend well beyond language work.

Document Translation is their primary function. They translate materials from OSINT sources and documents accessed by the attack teams. In the past year, they worked extensively on extracting and translating data from the Dubai Police database after other teams breached it. They also analyze the content of emails from compromised accounts of targets around the world.
Company and Sector Profiling is another key task. The team compiles OSINT dossiers on companies, likely for future targeting by the hacker teams.
Psychological Warfare Infrastructure falls under their responsibility too. They manage content for the department's influence operation platforms, including personas like "Abraham Ax" and "Moses Staff." ; The Sister's Team was directly involved in intelligence gathering on Israeli targets in Turkey to support the Istanbul attack plot led by Division 1500, which was exposed in June 2022.
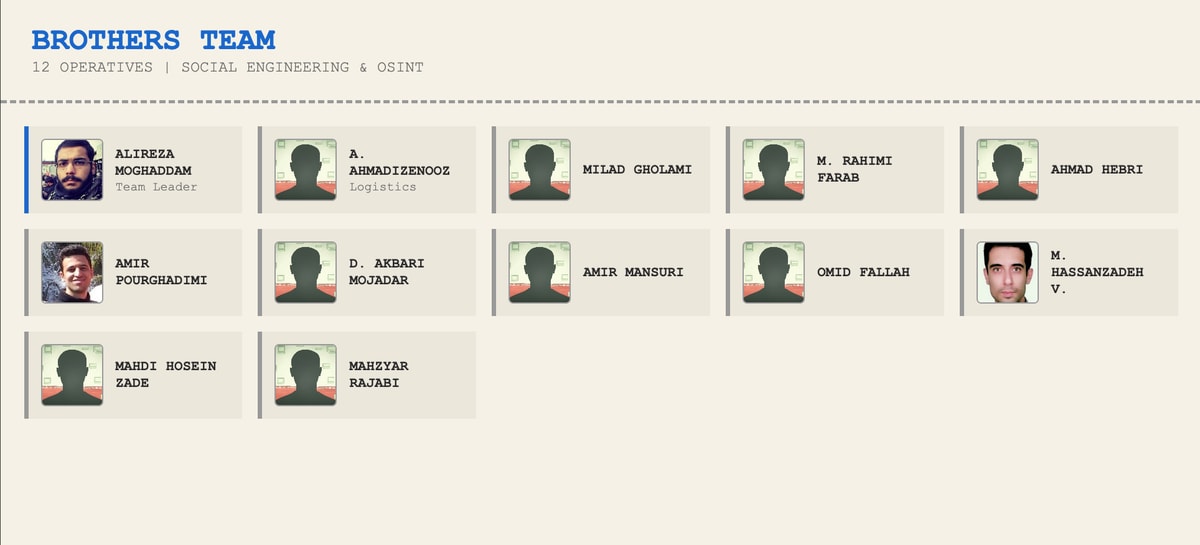
The Brother's Team (واحد برادران)
Twenty men. Codename: Pelak1.
This is the infrastructure and development crew. They maintain three dedicated networks: Tehran headquarters, Karaj, and Marzdaran. Their responsibilities extend beyond keeping servers running.

Infrastructure Maintenance and Development is their core function. This includes procurement, installation, and configuration of all operational infrastructure across the department's facilities. Mohammaderfan Hamidiaref (ID: 0023199709) is identified as the key figure for infrastructure operations.
System Development is equally critical. The team develops infrastructure systems and data extraction tools used in operations. The leaked documents reference specific systems under development, though full details are not included in the current files.
Intelligence Collection on Government Entities rounds out their mission. They target government bodies in various countries, gathering information to support both cyber and physical operations.
The Hacker Teams
Two dedicated attack teams operate from bases outside Tehran, plus a newly established unit:
Karaj Hacker Team (Team P8) operates from a facility in Karaj, west of Tehran. In the department's internal communications, they're referred to as "P68." This team was previously characterized as a base for deep-strike operations against countries surrounding Iran.
Led by Mahdi Sharifi (ID: 0322442567), a veteran attacker with the department, the team includes:
- Vahid Molawi (ID: 0323217087) - Hacker
- Alireza Feizi (ID: 0311915469) - Hacker
- Esmaeil Heydari (ID: 1382289537) - Hacker
- Amirhossein Aminnezhad (ID: 3770278070) - Hacker
- Amirhossein Inanloo (ID: 0311855911) - Hacker
Sharifi and Molawi's Role in the Dubai Police Breach: The leaked documents reveal that the Karaj team, under Sharifi's leadership, was directly responsible for the technical breach of Dubai Police systems. Once access was established, the Sister's Team spent months extracting and translating data from the compromised databases. This division of labor—hackers breach, women extract—represents Department 40's systematic approach to intelligence operations. The Dubai Police data gave the IRGC comprehensive visibility into anyone transiting through one of the world's major travel hubs, enabling them to track Israelis, Iranian dissidents, and other targets of interest in real time.

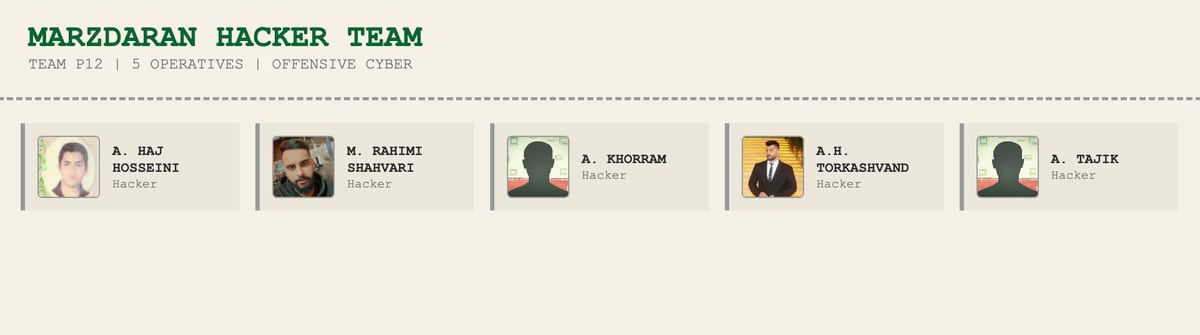
Marzdaran Hacker Team (Team P12) operates from a facility in the Marzdaran bolv. in Tehran. This team of approximately six attackers focuses on targeting countries surrounding Iran: UAE, Bahrain, Oman, Jordan, Egypt, and Israel.
Heravi Attack Team is the newest addition, established in early 2024 and currently based in Tehran. Just three members, but their job is pure offense:
- Creating phishing websites
- Sending spear-phishing emails
- Running targeted SMS campaigns
- Developing social engineering infrastructure
This team operates from the Heravi Base at Haravi, Hoseynabad, Meydan-e Haravi, Khatam ol-Moseyin, Vahed 202. Their focus on individual targeting suggests they're building the department's capacity for personalized attacks against high-value targets.
The Front Companies
You can't run a cyber army out of an IRGC building. So Rahrovi built shell companies. Three of them, all registered with the Iranian Companies Registry, all with traceable addresses and board members.
Zharf Andishan Tafakor Sefid (ژرف اندیشان تفکر سفید)
- Registration ID: 14008203298
- Postal Code: 1159963111
This is the main front, registered to the same address as their Tehran headquarters (Shohada Base). The CEO is listed as Manoochehr Vosoughi nayeri (منوچهر وثوقی نیری), but that's actually Mohsen Faroughi (محسن فروغی), an employee in the IRGC-IO's Division. Like Rahrovi, he operates with dual identities: his real national ID is 6039646969, but he also uses an alias ID of 1467932698. This pattern of creating complete second identities with separate national ID numbers appears to be standard practice for department leadership. Board member? Davood Ghanbari (ID: 0045741301), one of the Brother's Team logistics guys who also appears in the personnel files.
Amn Pardaz Ofogh Iranian (امن پرداز افق ایرانیان)
- Registration ID: 14012549409
- Phone: 02191096113
- Website: hxxp://apoi[.]net
CEO and Chairman: Niloofar Bagheri (ID: 4270932864). Yes, the department head's wife runs a front company. The same woman who leads the Sister's Team is listed as the official head of this registered business.
Aman Afzar Ofogh Iranian (امن افزار افق ایرانیان)
- Registration ID: 14011570578
- Postal Code: 1951715811
Board of Directors includes Mohammad Najafloo (محمد نجف لو, ID: 4270878835), a former senior official in the department, and Mekhaeel Hosseini (میکائیل حسینی), Rahrovi's alias.
The Target List
The leaked files include attack reports, access status documents, and reconnaissance data on targets across the Middle East. Here's what Department 40 has been hitting:
UAE - Deep Inside Security Services
- Dubai Police - Active access confirmed
- Abu Dhabi Police - Access status documented
- Fujairah Police - Attack report on file
- FlyDubai - Airline compromise
- EMARATECH - IT company with UAE security contracts
They're inside Gulf state police databases. Not trying to get in. Already in.
Jordan - Government Ministries
- Ministry of Justice (moj.gov.jo)
- Ministry of Defense
- NUCT University
- Jordan Enterprise Development Corporation
Egypt
- EgyptAir - Active access
- Public Business Development Ministry
Afghanistan
- Roshan (telecom)
- Etisalat (telecom)
- Ministry of Foreign Affairs
- Ministry of Interior
The Individual Targets
Department 40 also keeps files on individuals. The leaked documents include "email compromise reports" on specific people, documenting successful account takeovers and the intelligence extracted from their communications.
Olli Heinonen is perhaps the most significant name on the list. He served as the IAEA Deputy Director-General for Safeguards, the person who oversaw inspections of Iran's nuclear program. The department compiled a comprehensive intelligence dossier on him titled "Report on infiltration of email account - Part 1."

The Heinonen dossier is extensive. It begins with his complete biography: education at Helsinki University in radio chemistry, doctorate in 1981, and work at Finland's reactor research center on nuclear waste materials. He has multiple patents related to radioactive materials.
The dossier traces his entire IAEA career:
- Joined the IAEA in 1987
- Served for 27 years until 2010
- Deputy Director General, Head of the Department of Safeguards (2005-2010)
- Director of the Division of Safeguards Operations (1999-2002)
- Oversaw inspections in Iran, North Korea, Iraq, South Korea, Syria, and Libya
During his tenure, Heinonen oversaw inspections of Iran's nuclear facilities and was directly involved in assessing Tehran's compliance with international agreements. The dossier notes his post-IAEA positions at Harvard's Belfer Center and the Foundation for Defense of Democracies.
For the IRGC, Heinonen represents exactly the kind of high-value target outlined in their mission documents. His deep knowledge of nuclear safeguards processes, his connections to Western think tanks and policymakers, and his history of public criticism of Iran's nuclear activities made him a priority. Access to his email communications would reveal not just his personal correspondence, but potentially details about ongoing Western assessments of Iran's nuclear program and the network of officials and researchers he communicates with.
The dossier's existence demonstrates that Department 40 conducts comprehensive intelligence profiling before and during email compromise operations. They're not just hacking accounts; they're building complete pictures of their targets.
Nadereh Chamlou is an Iranian national. Her work on Iran policy and her platform in Western policy circles made her a target. Reza Neshat, an Iranian network engineer living in Sweden, appears in the files explicitly listed as a "regime opponent." His technical expertise combined with his opposition status put him on the department's radar.
Individual reports



The journalists on the list follow a pattern. Raheel Raza is a Pakistani-born Canadian journalist. Mohammad Ahmad Abdulqader Al-Zoubi is a Jordanian journalist. Giammarco Luciani works as an energy sector researcher. Each represents media or research that Iran's intelligence services want to monitor, influence, or silence.
These aren't random names pulled from social media. They're carefully selected individuals who either possess knowledge Iran wants, platforms Iran wants to control, or voices Iran wants to suppress. The department compiled detailed reports on each, documenting the compromise of their email accounts and the extraction of their communications.
The Mission Documents
One leaked file lays out the department's actual objectives. It's written in Farsi under the header of "Ofogh Media Institute" (موسسه رسانه ای افق), but there's nothing in the media about it. The document is marked "#PELAK-1" and describes comprehensive cyber offensive operations against what it calls "the Zionist regime."
IL offensive




The goals are broken down by target sector:
Human and Civilian Intelligence Collection
The department aims to build databases on Israeli citizens and those traveling to "occupied territories." Specific targets include:
- Civil registration systems
- Visa issuance and immigration management systems
- Banking systems and financial transaction records
- Hotel reservation platforms
- Airline booking systems
- Travel management platforms
Target countries explicitly listed: Turkey, UAE, Azerbaijan, Jordan, and others. The objective is to identify Iranians connected to "resistance movements" and track citizens of adversary nations.
Government and Institutional Penetration
Access government ministries, state organizations, and governmental bodies to:
- Obtain domestic and foreign statistics
- Gather economic, energy, and financial data
- Identify systemic weaknesses for future exploitation
- Access legal and judicial case files to identify potential recruits
Military and Security Infrastructure
Penetrate military, security, and intelligence networks to collect:
- Personnel information (positions, roles, capabilities)
- Equipment capabilities and deployment readiness
- Training scenarios and exercise plans
- Military software and infrastructure details
Critical Infrastructure Attacks
The document outlines offensive operations against:
- SCADA systems in oil, gas, and power sectors with the goal of "creating disruption and stopping operations"
- Transmission and distribution networks for electricity
- Industrial facilities including steel plants and mineral processing
- Transportation networks including traffic management and cargo systems
- Telecommunications including ISPs and data centers
Nuclear Sector Operations
Specifically targeting Israel's nuclear program:
- Identifying companies and individuals in nuclear energy sector
- Penetrating nuclear facility infrastructure
- Disrupting military nuclear unit operations
Psychological Warfare
The document describes media operations to:
- Disseminate achievements of cyber operations through news coverage
- Recruit journalists from target countries (direct and indirect methods)
- Exploit television and radio infrastructure
- Create perception that Israeli cyber capabilities have been weakened
- Use techniques including: labeling, softening/enlightening, confirmation, rumor spreading
This isn't hacking for profit. It's a comprehensive strategy for state-sponsored intelligence collection, infrastructure pre-positioning, and information warfare.
The Psychological Warfare Platforms
Beyond hacking, Department 40 operates platforms designed for recruitment and influence operations.
Tecret Platform
This is a front company operating in the UAE and Turkey. Its purpose: recruiting cyber professionals. The platform appears legitimate to potential recruits, but it's actually a pipeline for identifying and vetting talent for IRGC cyber operations.
Ameen Alkhalij Platform (امین الخلیج)
This website targets a different audience: UAE citizens and employees in the Emirates' security sector. The leaked recruitment document, written entirely in Arabic, reveals the platform's true purpose.

The platform's name translates to "Trustworthy of the Gulf," designed to appeal to Emirati nationalism while concealing its Iranian origin. The recruitment pitch emphasizes financial compensation and frames cooperation as protecting Gulf stability.
The Surveillance Operation
The leak includes something unusual: a physical surveillance report.
In late 2022 (Iranian calendar dates 27/09/1401 and 04/10/1401), department personnel conducted surveillance on a woman in Tehran. The report describes her as wearing a chador and niqab, observed doing "wall writing," graffiti with what were likely anti-regime slogans.
Surveillance



They photographed her over multiple days. They tracked her to a building on Goethe Street. They noted that multiple women in similar dress entered the same location. Their conclusion: it might be a "team house."
The Attack Reports
The leaked files include cover pages and reports from attacks on specific targets. Each document represents successful or ongoing operations against foreign organizations. These aren't aspirational targets. The reports document active access and data extraction.
UAE Targets
The UAE represents the department's most extensive targeting. The combination of police databases, airlines, and IT contractors gives them comprehensive visibility into Emirati security operations and the movement of people through the country.
Dubai Police is the most significant breach. The department compiled detailed access status reports showing active penetration of Dubai Police systems. The Sister's Team spent significant time extracting and translating data from this breach. Due to security considerations and the sensitive nature of documents related to the United Arab Emirates police force, the mentioned files have not been published in full on the blog. Emirati security officials can contact me via email so I can send them the original file.
Dubai Police Extraction Details:
- Email Communications: Downloaded emails from police officers and administrative staff
- Hotel Guest Identity Photos: Downloaded identity photographs of UAE hotel employees and travelers in 2022. Anyone checking into a Dubai hotel has their photo in this system
- Medical Clinic Database: Downloaded database from a medical clinic connected to Dubai Police network
- Access Expansion: Established persistent access for continued collection

FlyDubai represents the travel intelligence mission, and more specifically, the advance warning system for assassination operations. Airline systems contain passenger manifests, travel patterns, passport details, and payment information. The department's mission documents specifically list airline booking systems as priority targets for tracking the movement of Israelis, diaspora Iranians, and other persons of interest through the region.
FlyDubai access allows Department 40 to identify in advance when targets marked for attack will arrive. The department can see exactly which flight a target is on, when they will land, and where they booked onward travel. Assassination teams can then position themselves at airports, arrange surveillance along routes from the terminal, or set up at hotels where targets have reservations. Whether the targets are Israelis, Jews, Iranian regime opponents, Emiratis critical of Iran, or Europeans, FlyDubai's route network across the Middle East, Africa, and Europe makes it an ideal collection point for travel intelligence that feeds the kill chain.
Fujairah Police


Fujairah Police extends the coverage beyond Dubai. Fujairah's port is one of the world's largest bunkering hubs, making its police database valuable for tracking maritime movements and personnel.

Abu Dhabi Police access status documentation shows penetration of the capital's security services. Combined with Dubai and Fujairah, the department has coverage across multiple Emirates.
EmaraTech



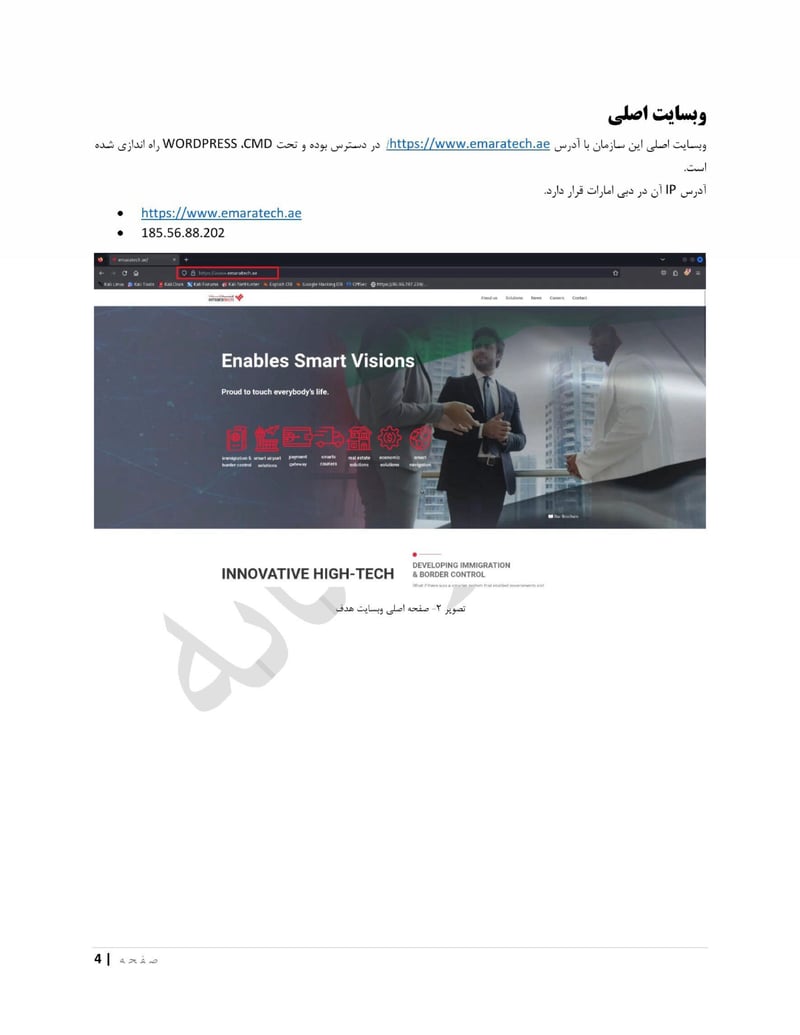
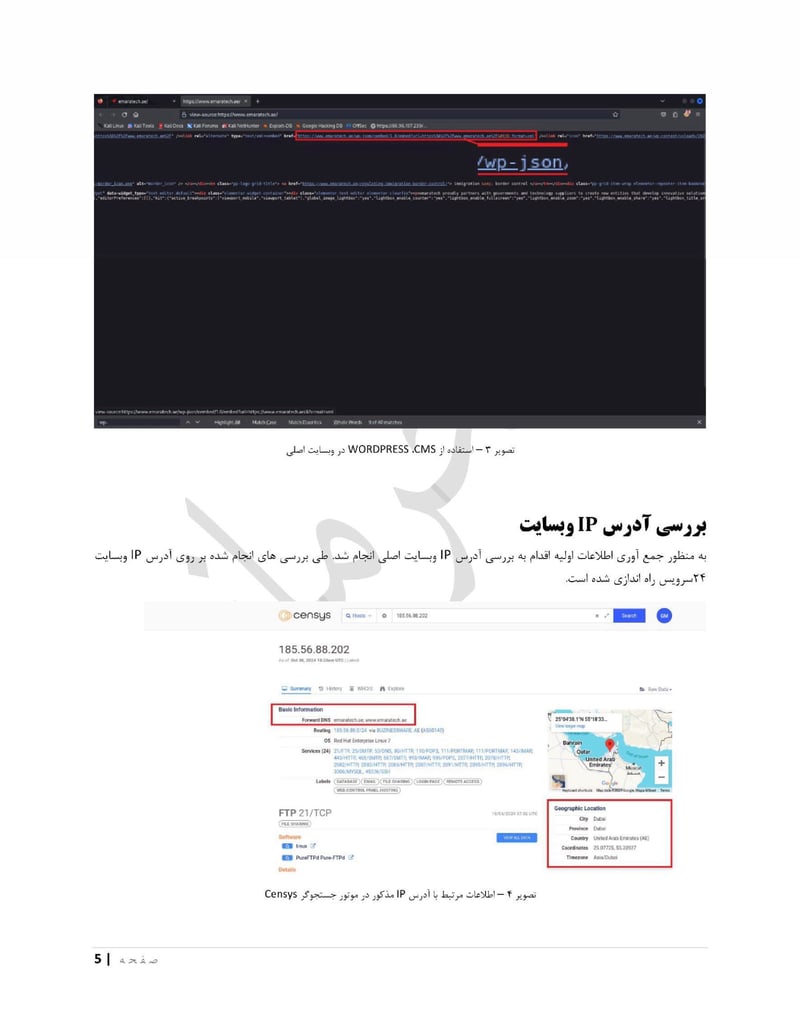
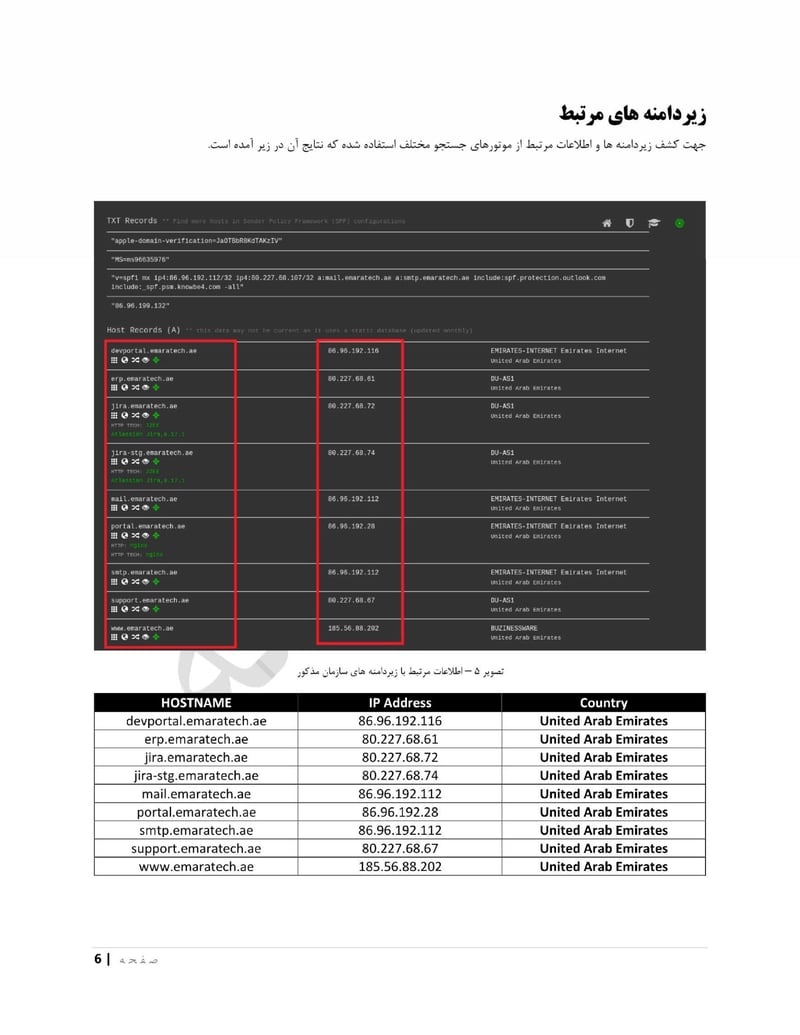
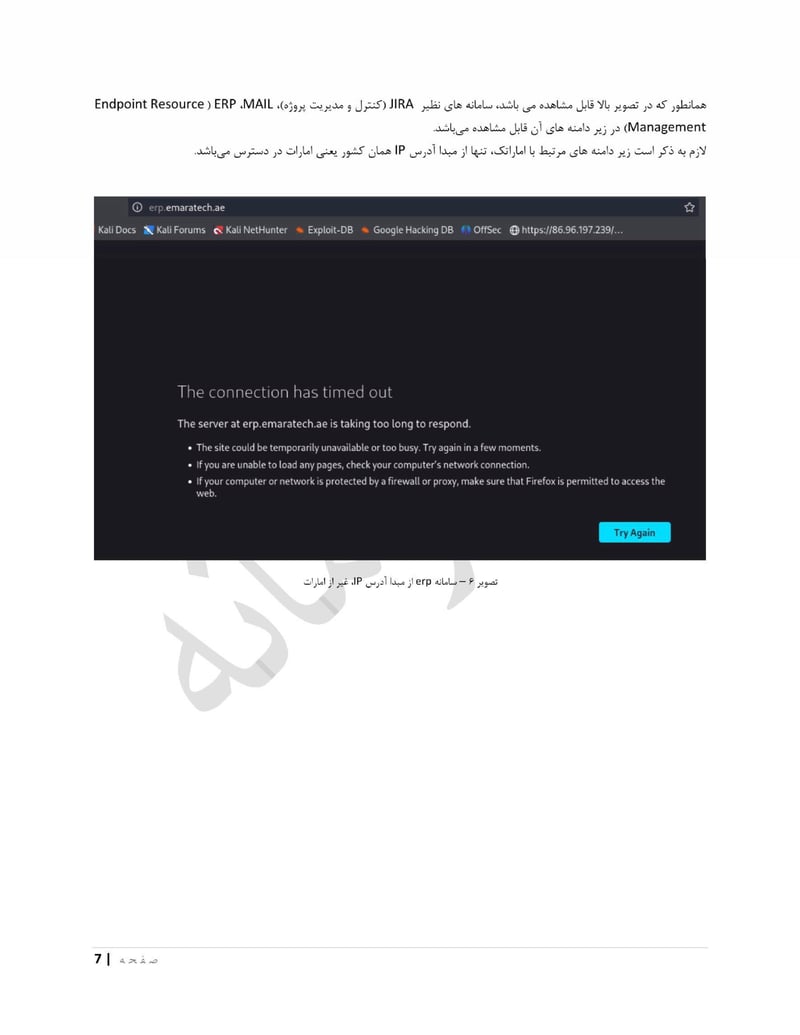

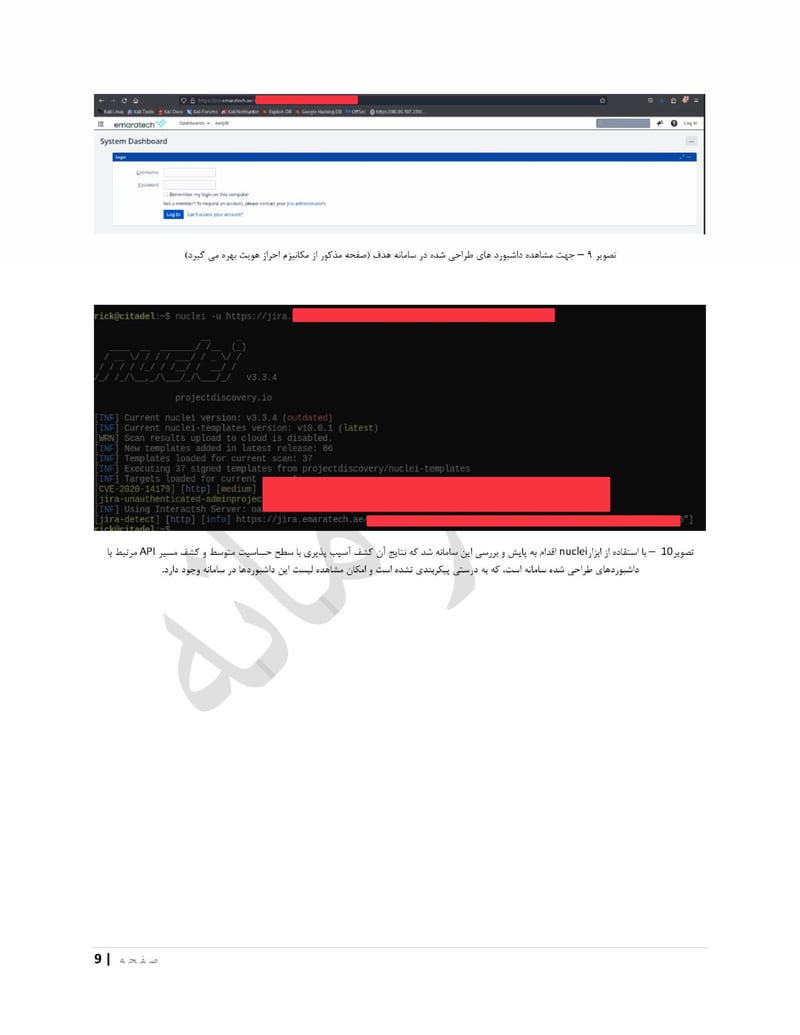
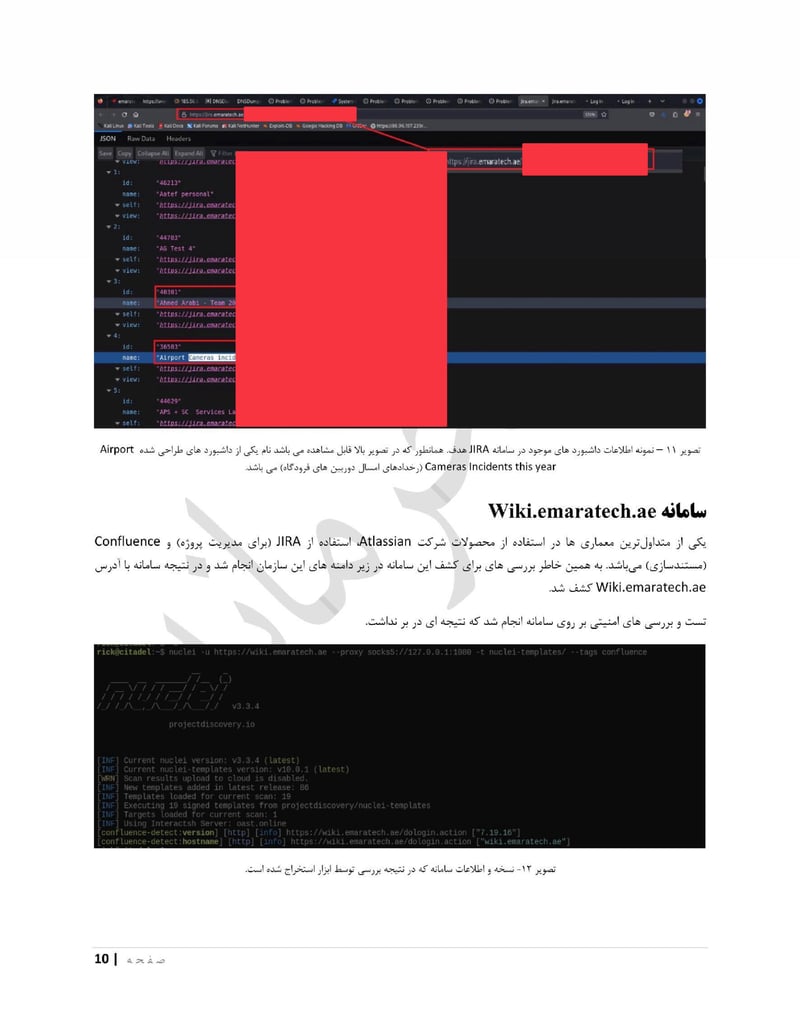

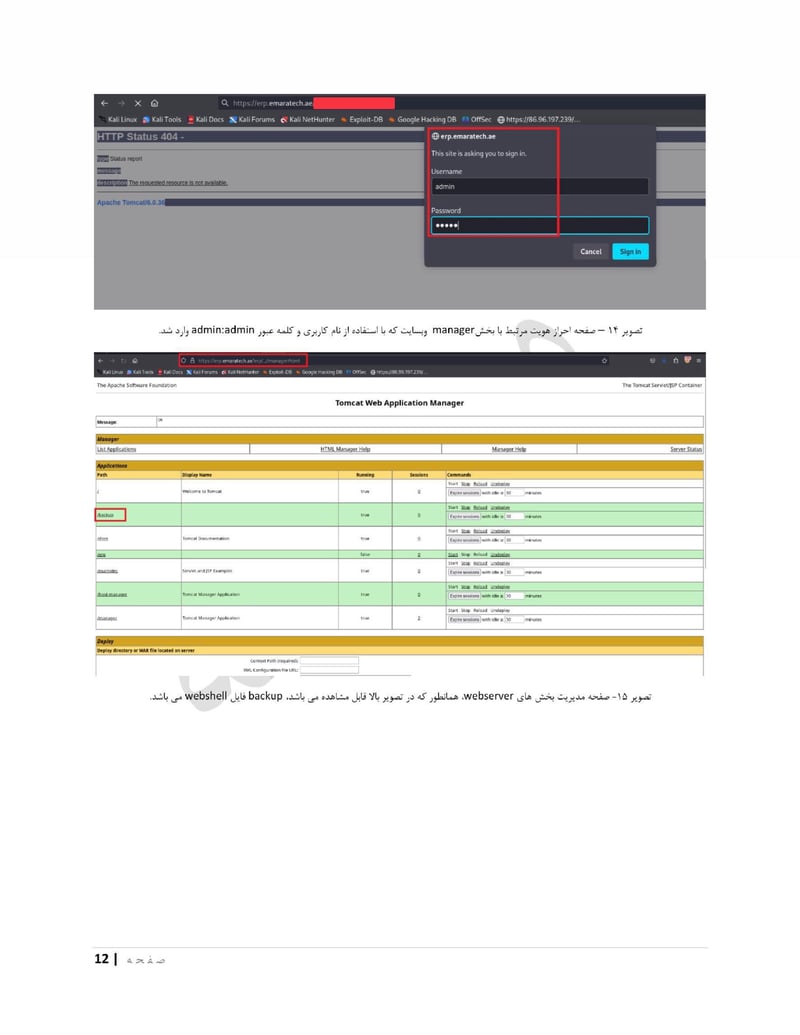
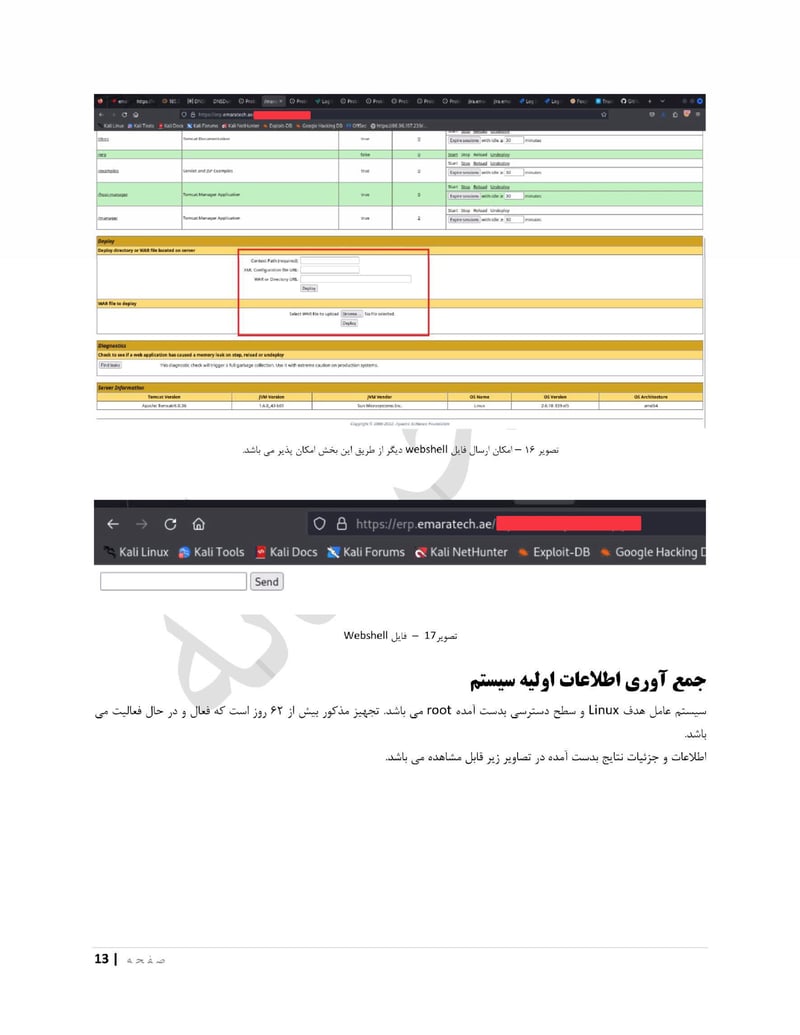
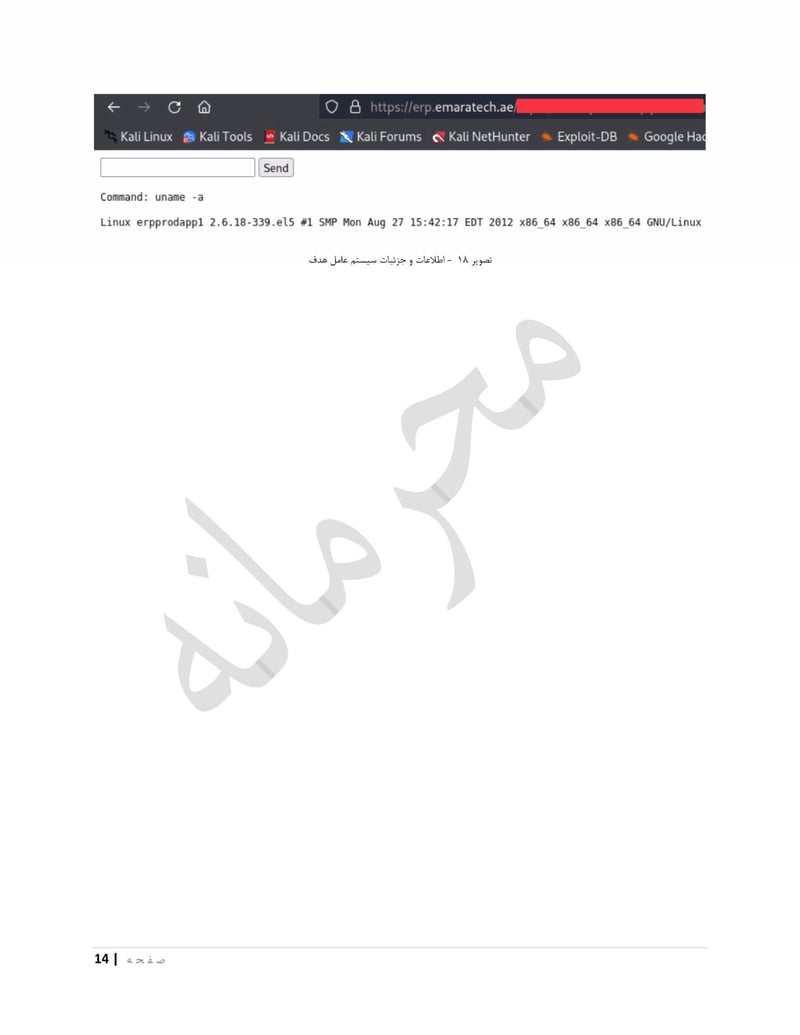

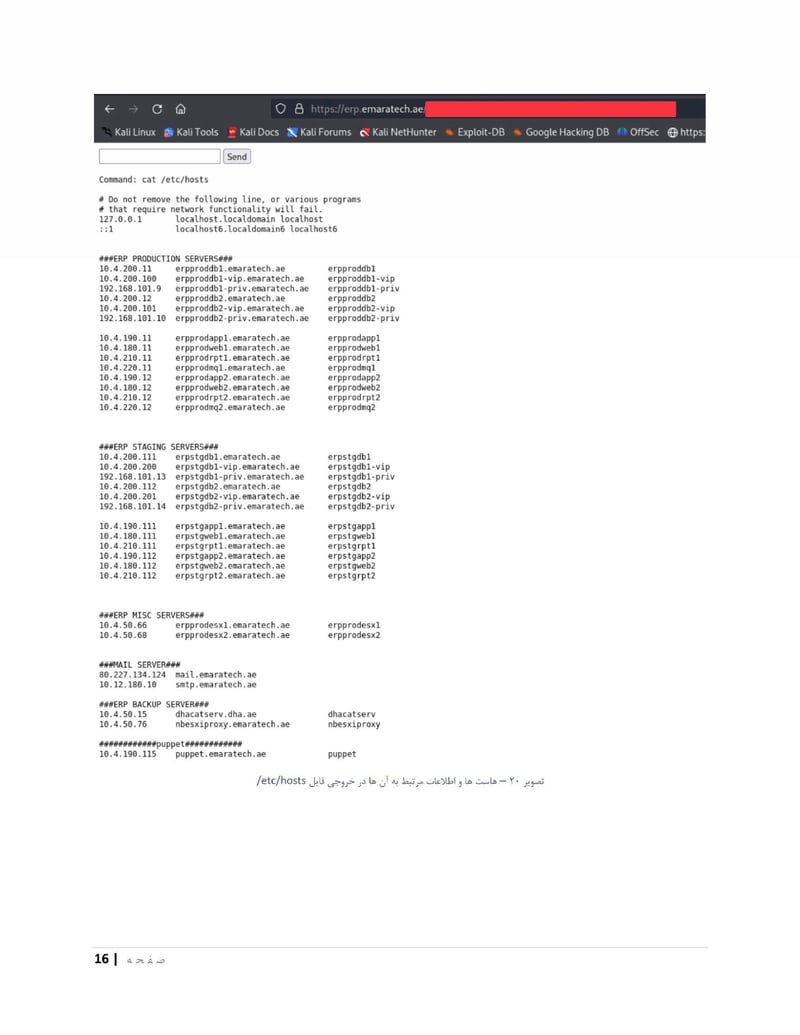
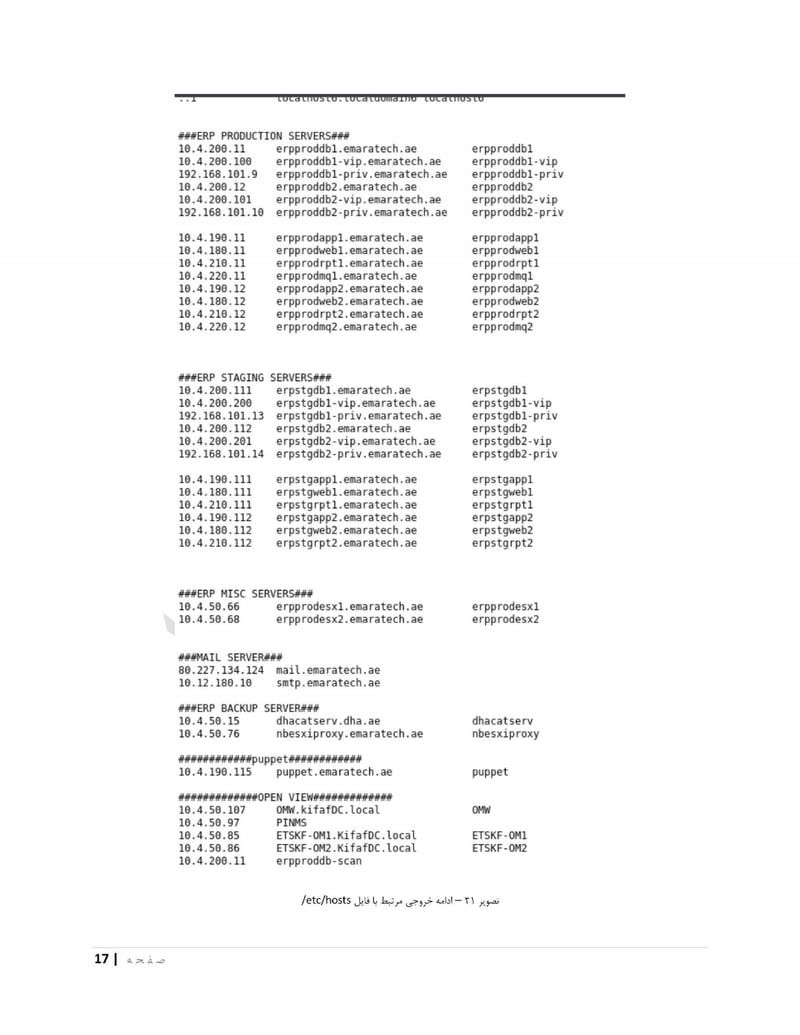

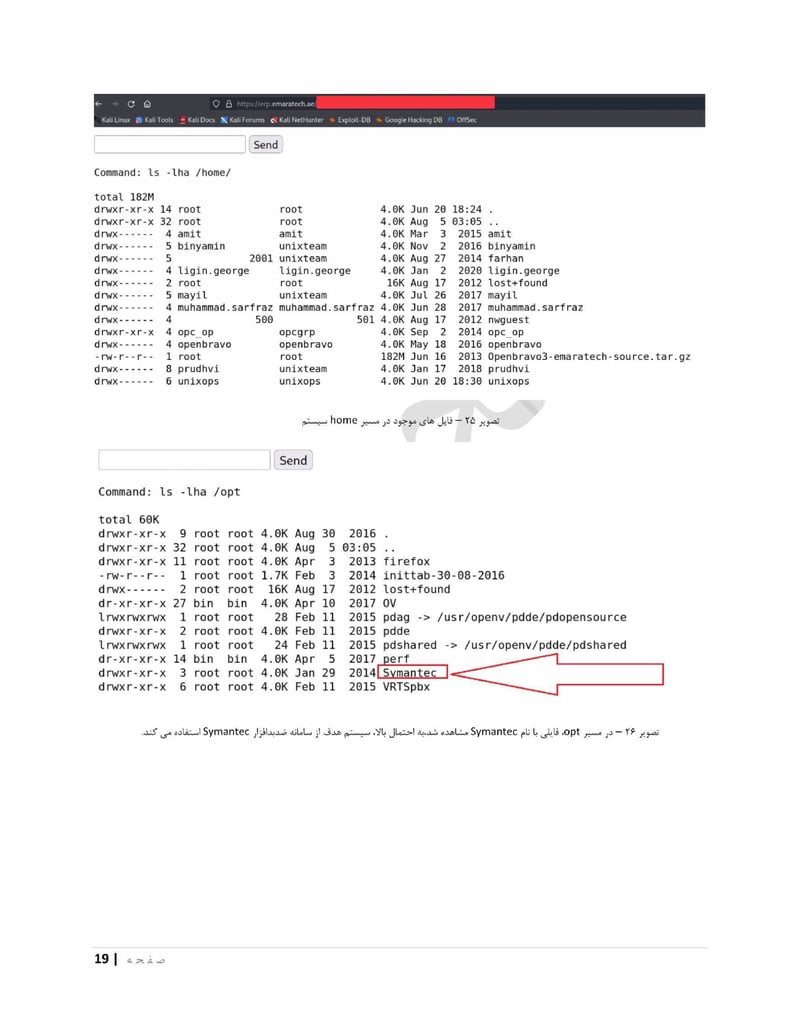


EMARATECH is a different kind of target. This IT company holds contracts with UAE security entities, making it a supply chain attack vector. Compromising EMARATECH potentially gives access to multiple government clients through a single point of entry. It also provides insight into the technical infrastructure of UAE security services.
Jordan Targets
Jordan's position as a Western ally bordering Israel makes it strategically valuable. The department targeted government ministries, educational institutions, and development organizations.
Russifah





Russifah Municipality sits in the Zarqa Governorate, one of Jordan's largest population centers with a significant Palestinian population. Municipal systems contain resident data, property records, and local administrative information.
Mojgov


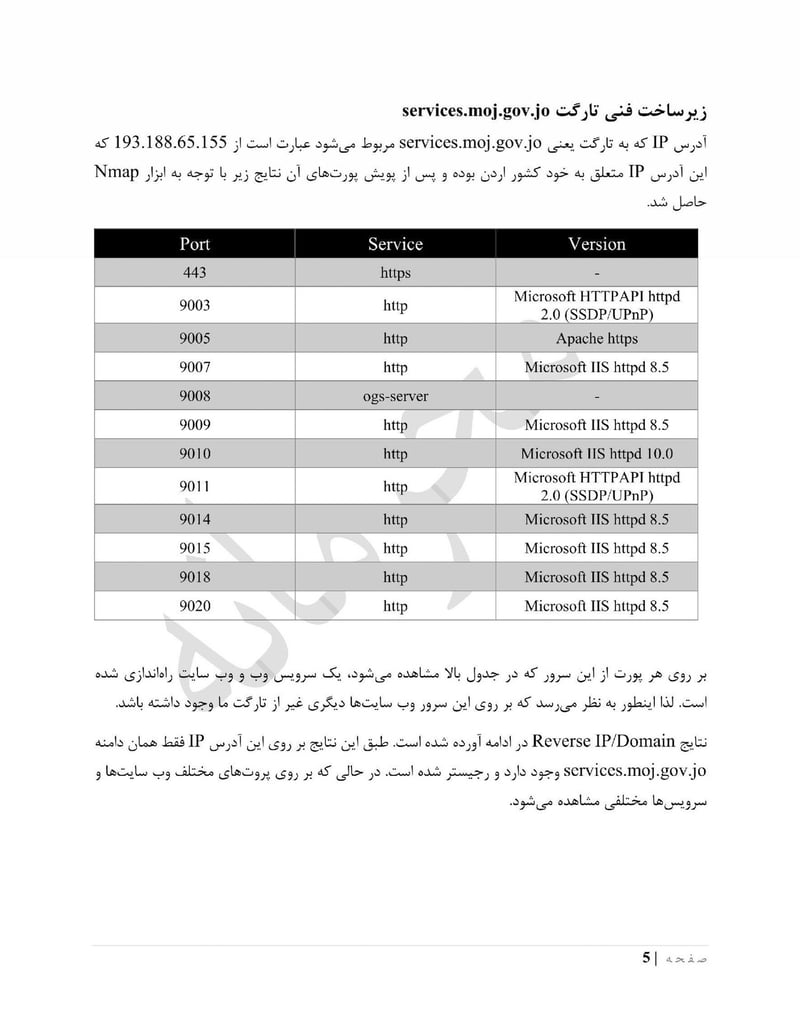
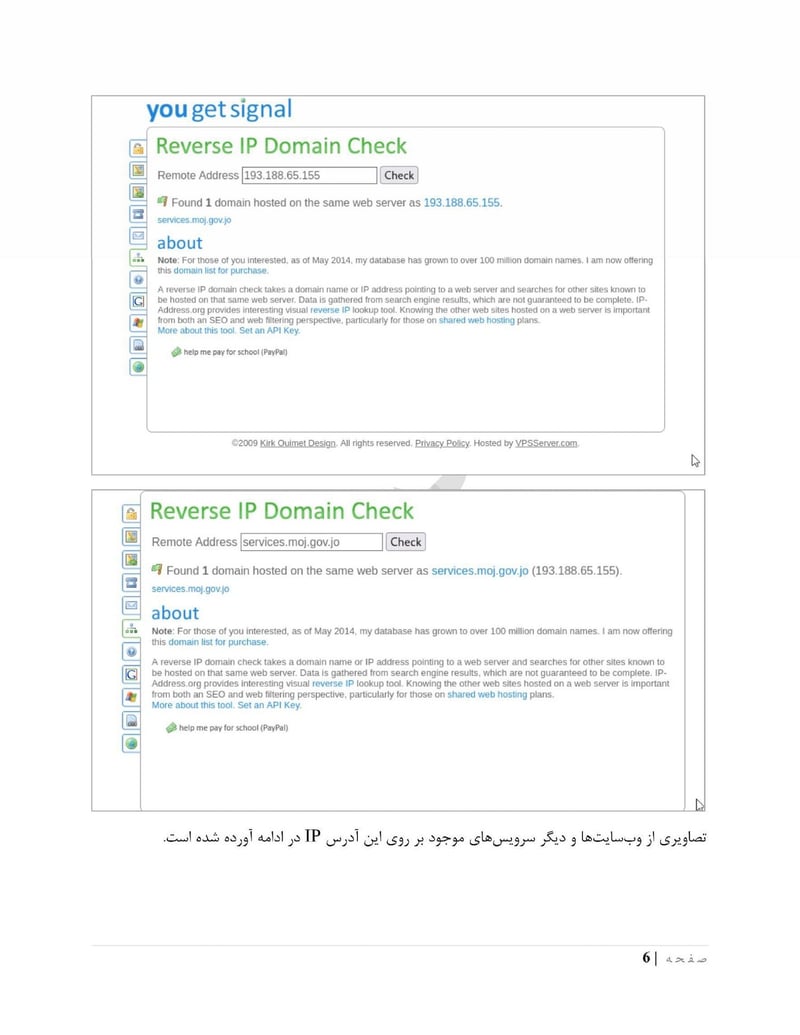
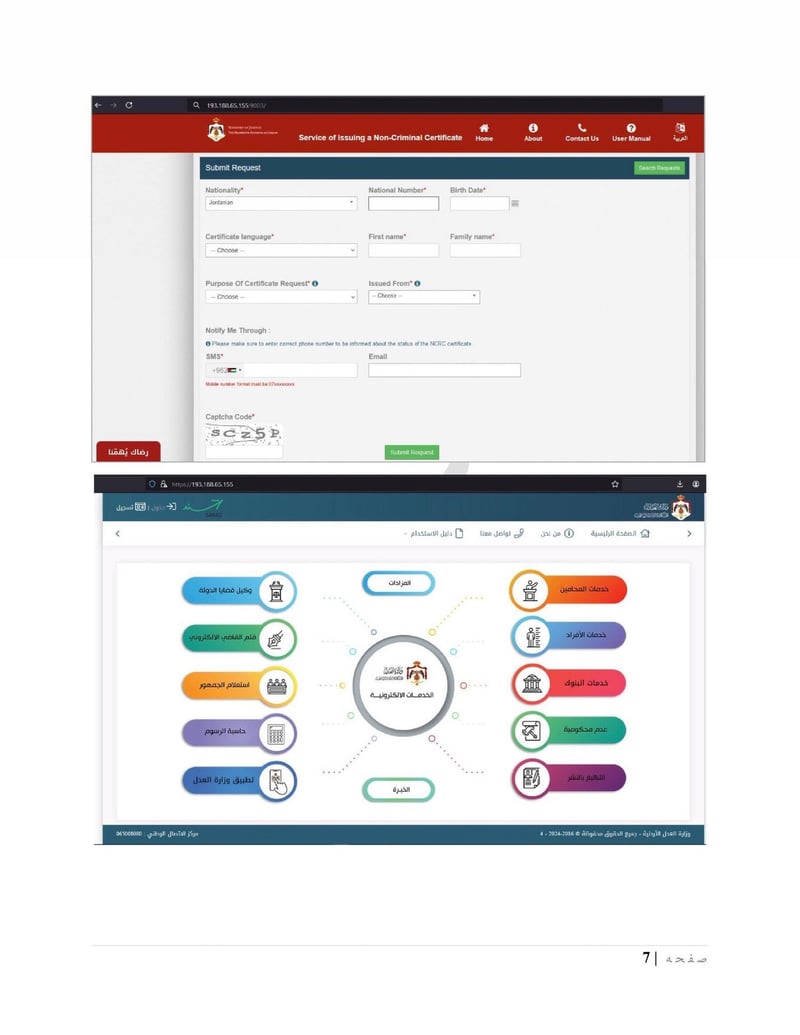






The Ministry of Justice (moj.gov[.]jo) holds legal case files, judicial records, and personnel information. The mission documents specifically mention accessing legal and judicial files to identify potential recruits and gather intelligence on legal proceedings.
Nuct edu



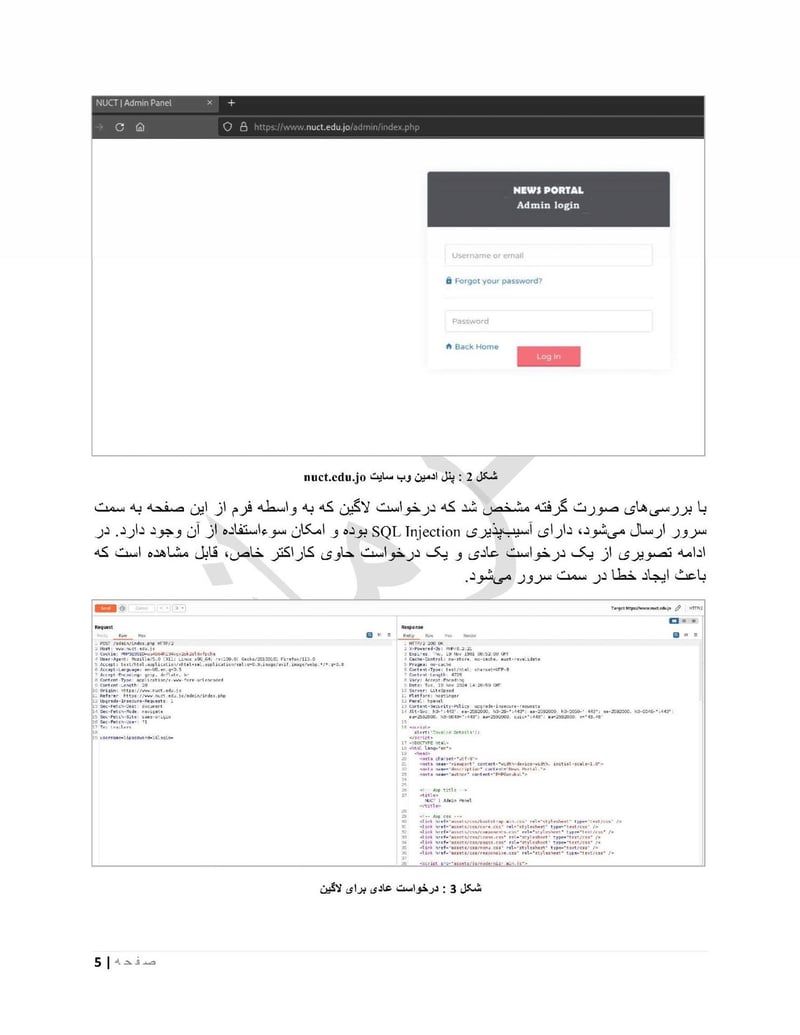
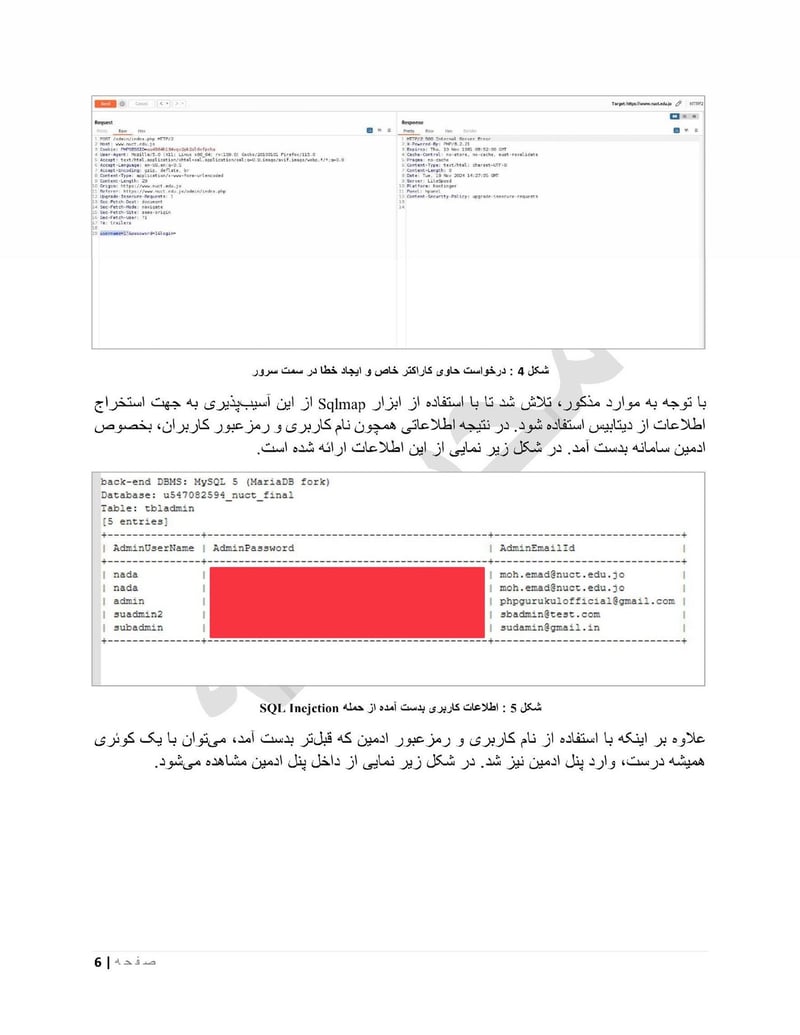
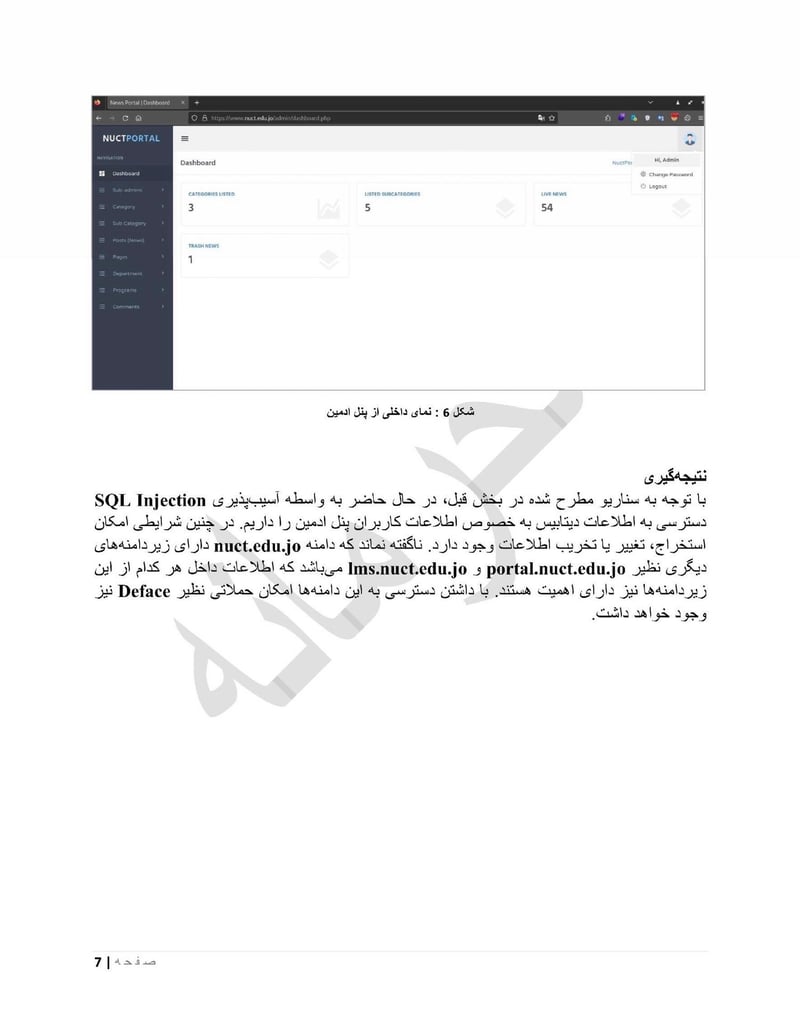
NUCT University (nuct.edu.jo) represents the academic targeting. Universities contain research data, faculty communications, and student records. They're also environments where the department could identify potential recruits or gather intelligence on technical research.
Jedco



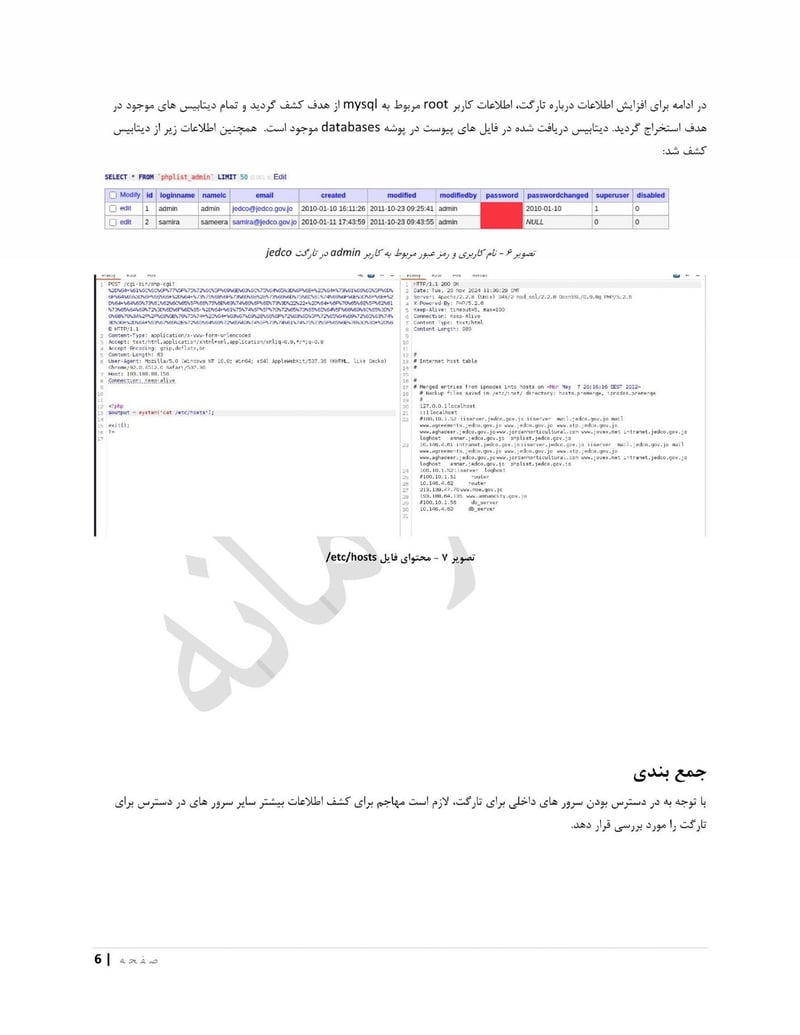
Jordan Enterprise Development Corporation (jedco[.]gov[.]jo) manages business development and investment in Jordan. Access here provides economic intelligence and information on companies operating in the kingdom.
Egypt Targets
Egypt's normalization with Israel and its role as a regional transit point make it a priority for the department.
EgyptAir access status reports show active penetration of Egypt's national carrier. The Target Status Report shows the extent of the extraction:
EgyptAir Extraction Details:
- Complete Flight Database: Downloaded the entire flight database.
EgyptAir's routes connect Africa, the Middle East, and Europe, giving the IRGC visibility into passenger movements across three continents. With the complete flight database, they can track any individual of interest traveling on Egypt's national carrier.
Public Business Development Ministry (mpbs.gov.eg) handles economic development and business registration. Access provides intelligence on Egyptian companies, foreign investment, and economic planning. It also offers insight into businesses that might be fronts or have connections to Israeli entities.
Afghanistan Targets
Afghanistan's telecommunications sector was a major focus, giving the department visibility into communications across the country.
Roshan


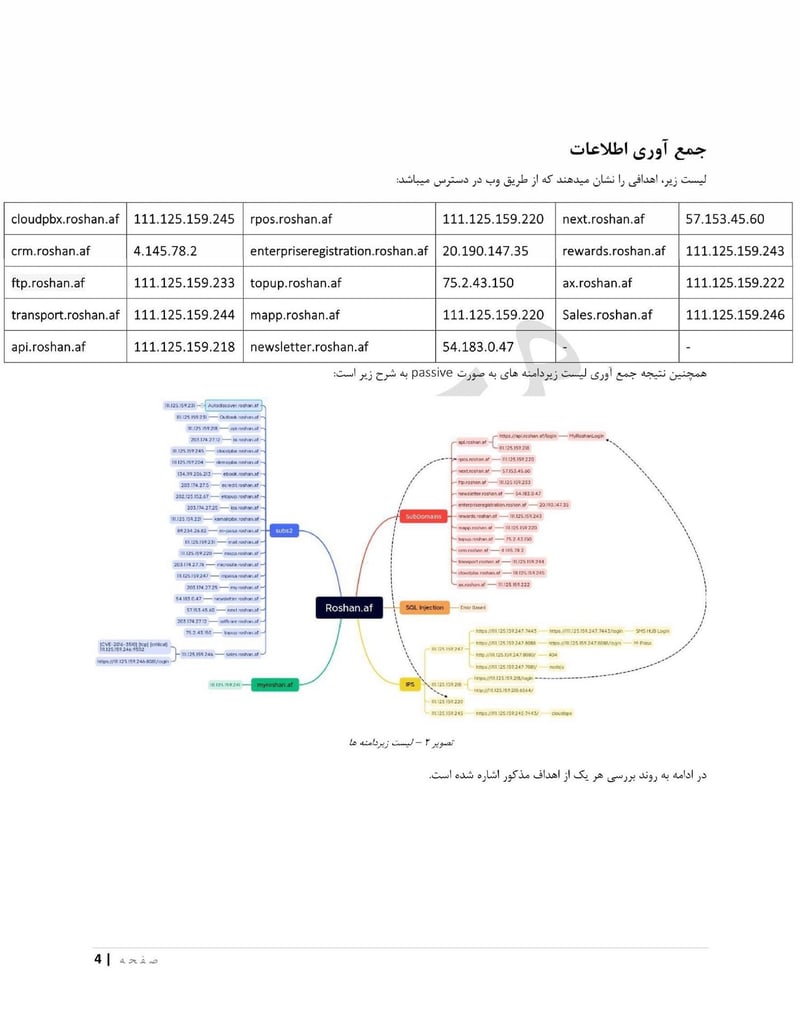
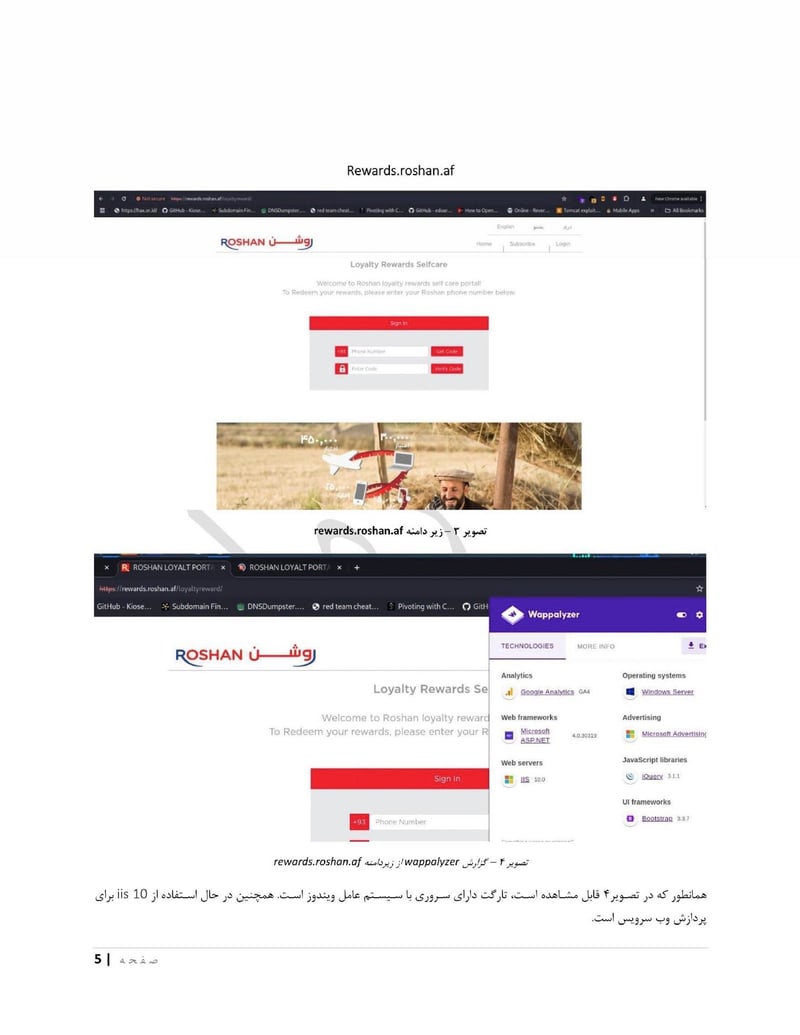
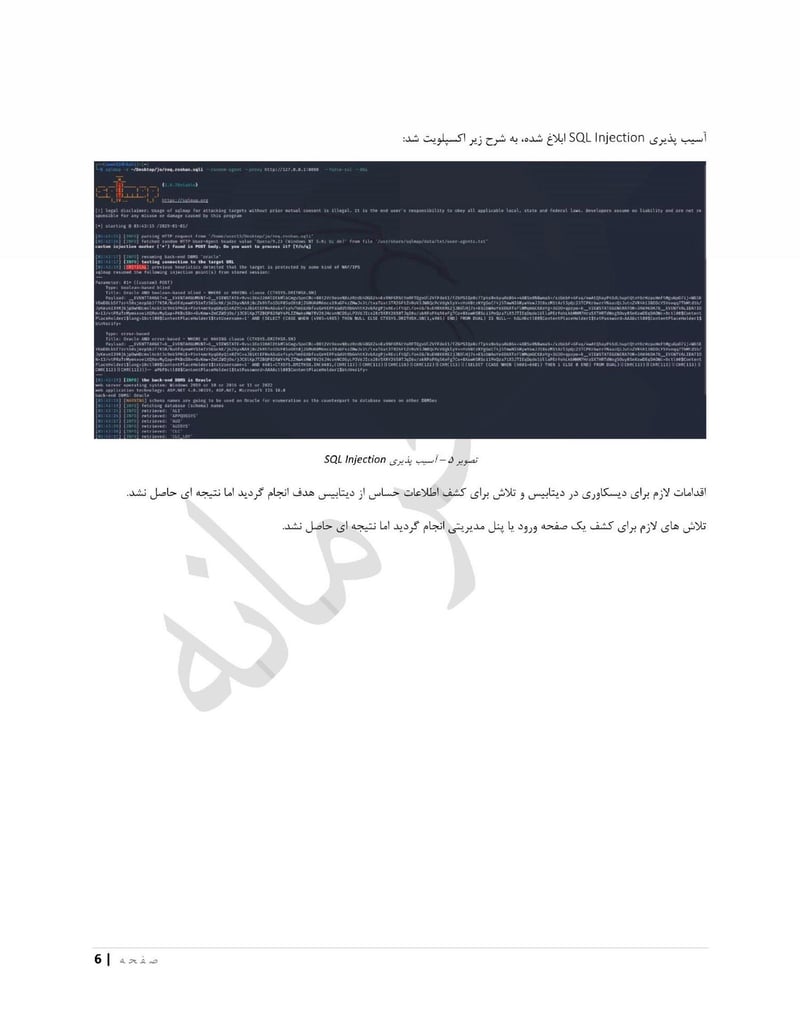
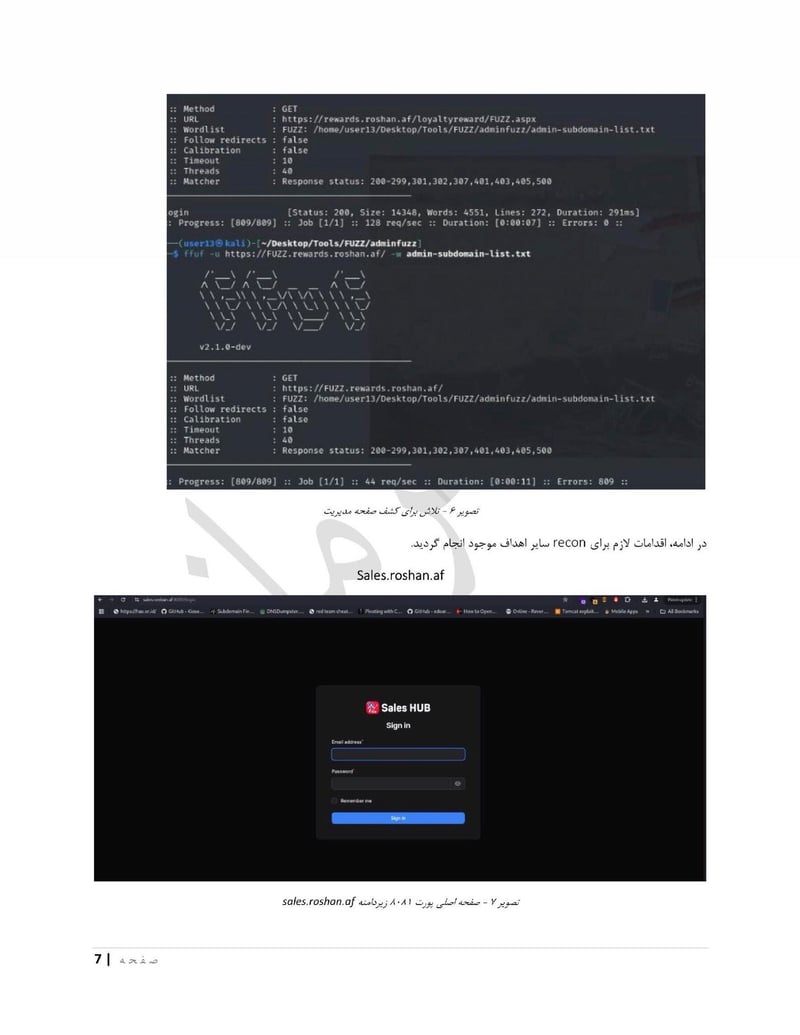
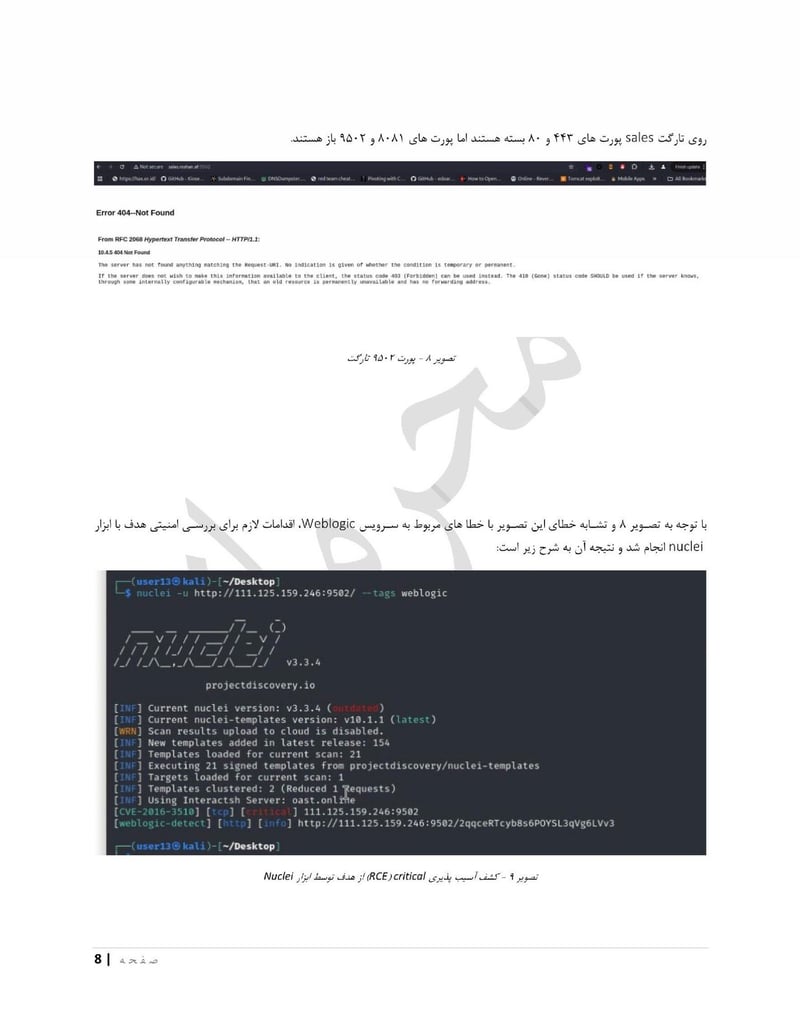
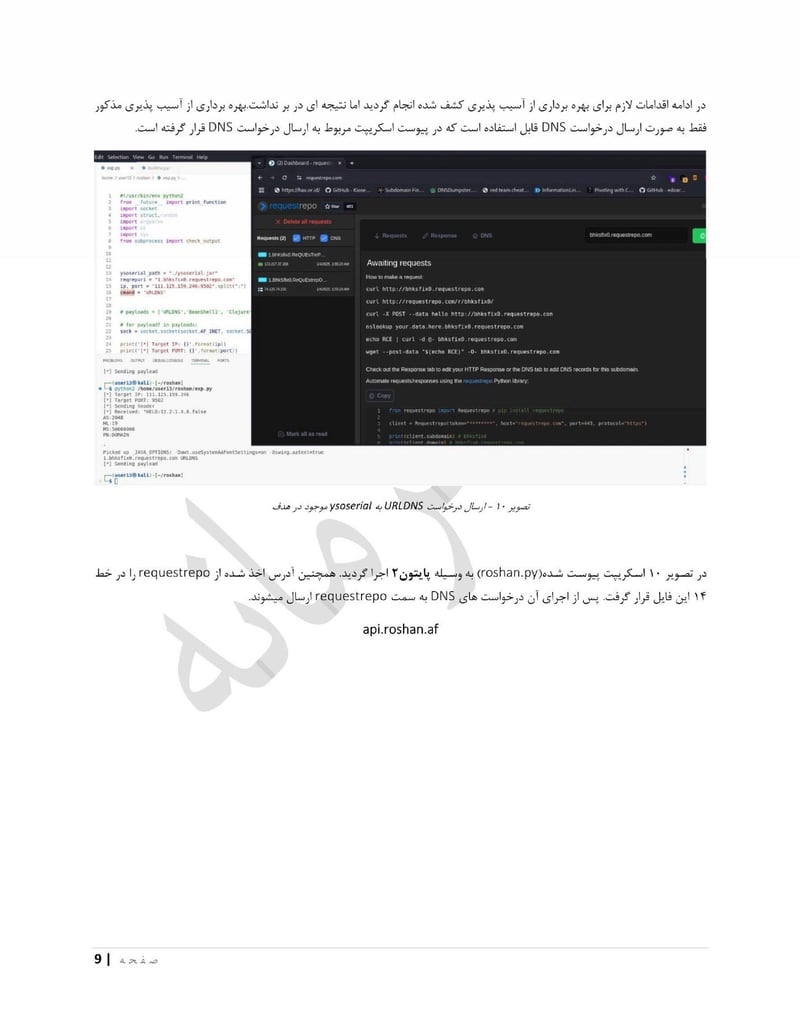
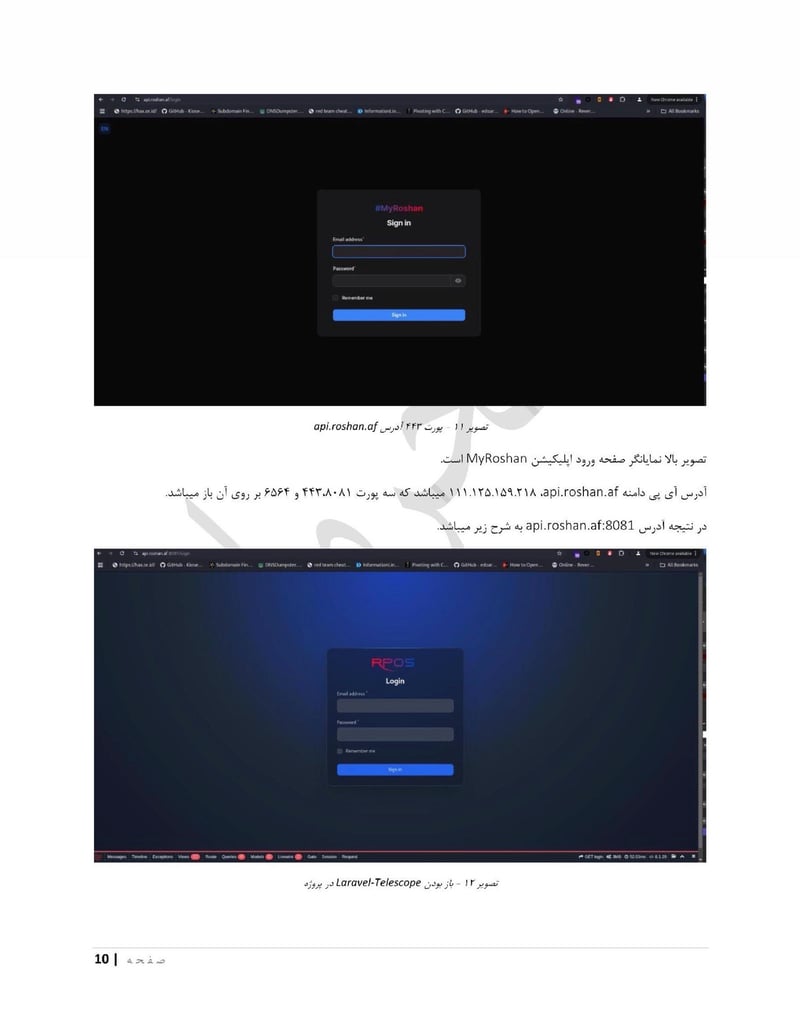

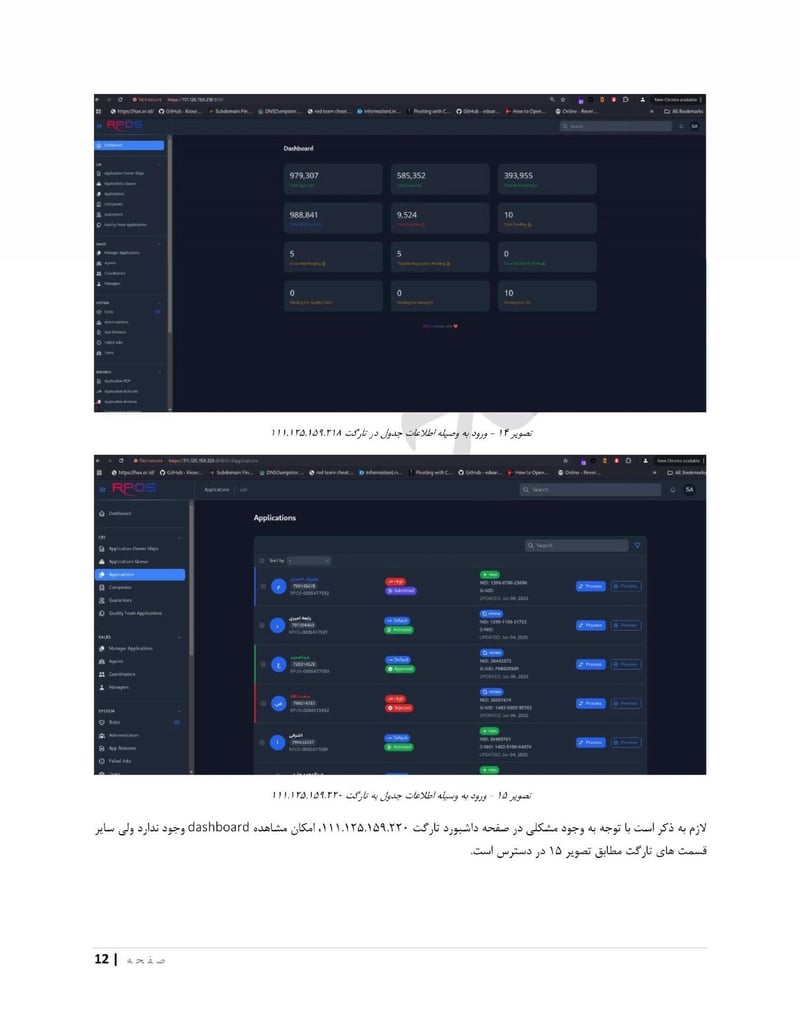
Roshan is one of Afghanistan's largest telecommunications providers. Compromising a telecom gives access to call records, subscriber data, and potentially communications content. The department can identify who is talking to whom, build social network maps, and track the movements of phones across cell towers.
Etisalat af


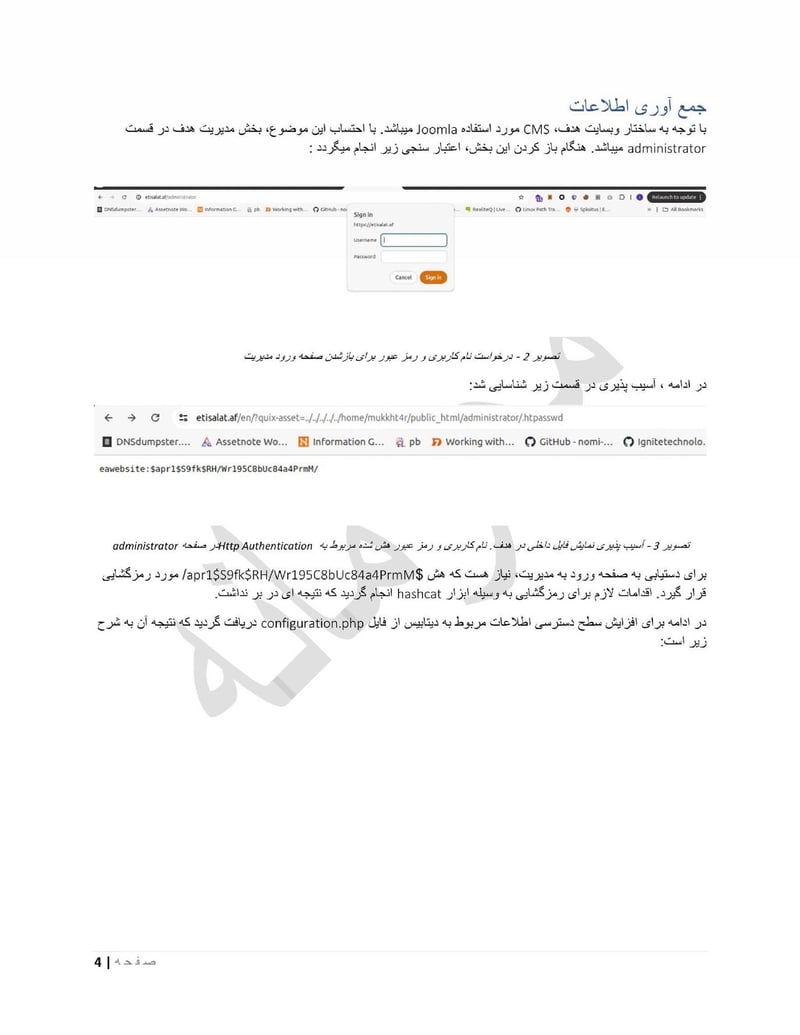
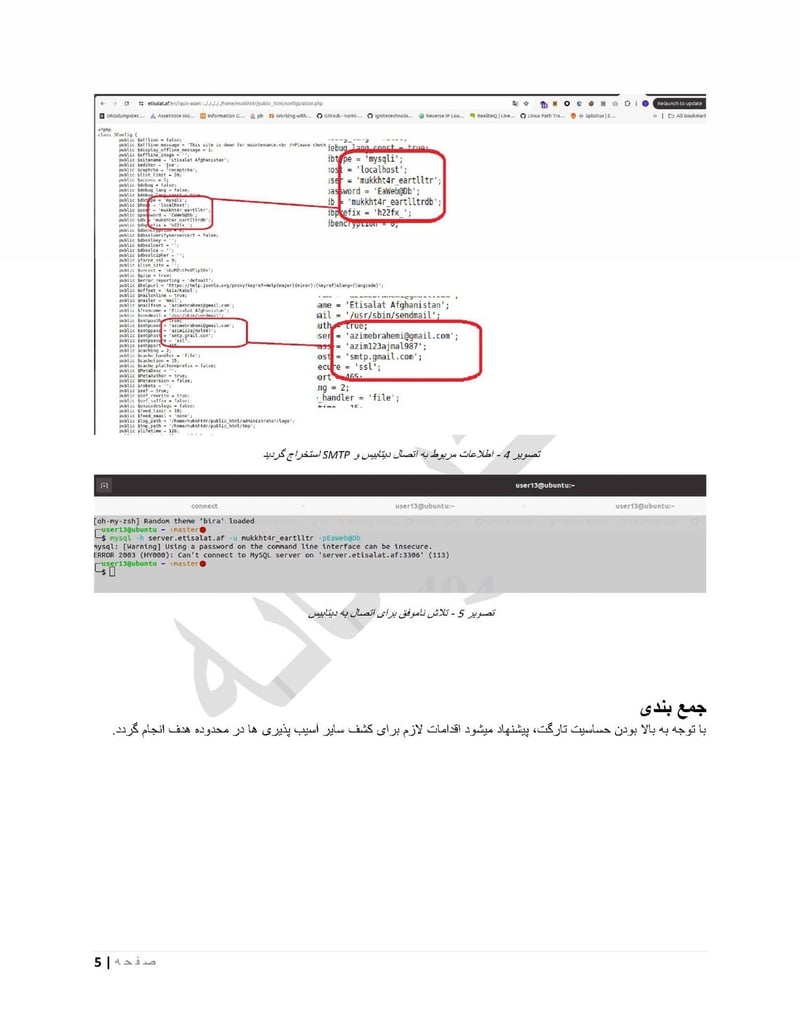
Etisalat Afghanistan provides similar value as a second major telecom provider. Having access to multiple carriers ensures comprehensive coverage and the ability to correlate data across networks.
The leaked documents also reference, targeting the Ministry of Foreign Affairs (mfa[.]gov[.]af), Ministry of Interior (moi[.]gov[.]af), and Saalam, another telecommunications company. The combination of government ministries and telecoms gives the department both official communications and the private communications of Afghan officials and citizens.
European and North American Targets
The leaked files reveal extensive operations beyond the Middle East, targeting infrastructure across Europe and North America specifically designed to locate and track individuals.
Greece - Maritime and Hospitality Sector
Greece represents one of the department's most extensive European targeting operations, with over 30 Exchange servers compromised. The targets reveal a clear pattern: tracking people and ships in real time.
- mail.ammosbeachhotel[.]gr - A hotel's mail server. Access to hotel booking systems allows the department to identify guests in real time: who is staying where, their check-in and check-out dates, passport details, and payment information. For a unit that supports assassination operations, this is precision targeting data.
- mail.globalmaritimegroup[.]com - A maritime company's mail server. The leaked files include extracted data showing 78 employee accounts compromised, including distribution lists for chartering, crew, marine operations, technical, and compliance departments. This access enables real-time tracking of ship locations, cargo manifests, and crew rosters across the Mediterranean.
- webmail.optimabank[.]gr - Greek banking institution
- hermes.froika[.]com - Greek pharmaceutical company
- ex.nuntiusbrokers[.]com - Financial services
- Multiple Greek Parliament and government systems (documented in previous reporting)
The maritime targeting is particularly significant. Greece hosts one of the world's largest shipping registries. Access to maritime companies gives the IRGC visibility into vessel movements, which can be used to track targets traveling by sea or to monitor shipping routes for potential interdiction.
Canada - Property and Location Tracking
- geowarehouse[.]ca - This Canadian property database was targeted to identify the home addresses of individuals who purchased property in Canada. For Iranian dissidents, journalists, or activists who fled to Canada, this database would reveal their exact residential locations. The department can cross-reference property records with their other intelligence holdings to build comprehensive targeting packages on regime opponents living abroad.
The Canadian target list also includes approximately 500 Exchange server IP addresses, suggesting broad reconnaissance of Canadian organizations for future exploitation.
Austria, Belgium, and Beyond
The leaked ProxyShell target files include folders for Austria (AT) and Belgium (BE), indicating active operations against European Union member states. The specific targets in these countries have not been fully analyzed, but the pattern suggests similar focus on travel, financial, and government infrastructure.
Azerbaijan Targets
Attack reports




AIC, an Azerbaijani oil company, represents the department's interest in energy sector intelligence. Azerbaijan's oil and gas infrastructure, pipelines to Turkey and Europe, and its position between Iran and Russia make energy companies valuable intelligence targets.
The Target Status Report reveals persistent access:
AIC Extraction Details:
- Full Email Review: Complete access to company email communications
- Network Expansion: Lateral movement through company systems
- Active Backdoors at Multiple IPs:
- 37.xx.xx.xxx - backdoor placed
- 9x.xx.xxx.xxx - backdoor placed
- 18x.xxx.xx.xxx - backdoor placed
The multiple backdoors indicate this wasn't a one-time breach. Department 40 established a persistent presence to collect ongoing intelligence about Azerbaijan's energy sector operations.
Saudi Arabia Operations
The leaked documents reference operations against Saudi Arabia that go beyond typical cyber espionage.
The master operations document outlines a planned operation against Saudi Prince Turki Al-Faisal, the former head of Saudi intelligence and former ambassador to the United States and United Kingdom. Prince Turki led Saudi Arabia's General Intelligence Directorate for over two decades (1977-2001), making him one of the most knowledgeable figures on Middle Eastern intelligence operations. He subsequently served as ambassador to the UK (2003-2005) and the US (2005-2007), giving him extensive connections to Western intelligence and diplomatic communities.
Targeting a senior member of the Saudi royal family with this level of intelligence and diplomatic experience represents a significant escalation. The department's interest in Prince Turki likely stems from:
- His deep knowledge of Saudi intelligence operations and personnel
- His relationships with Western intelligence agencies
- His public criticism of Iranian regional policies
- His potential value as a high-profile assassination target that would send a message to the Saudi leadership
The same file describes broader covert operations against Saudi Arabia and its leadership. The combination of targeting a specific royal family member alongside general operations against Saudi leadership suggests coordinated intelligence gathering on the kingdom's decision-makers, the kind of comprehensive profiling that precedes either recruitment attempts or assassination planning.
Western Embassies in Iran
Department 40 also conducts domestic counter-intelligence operations. The leaked documents reference espionage activities against Western embassies operating inside Iran.
The master operations document contains documentation of the department's surveillance and intelligence gathering on diplomatic missions in Tehran. Department 40 conducts both external cyber operations and domestic counter-intelligence. They monitor foreign diplomats on Iranian soil, likely trying to identify intelligence officers operating under diplomatic cover and gather information on embassy communications and activities.
The Istanbul Attack Plot Connection
One of the most significant revelations is the direct connection between Department 40's cyber operations and physical attack planning.
The Sister's Team was directly involved in gathering intelligence on Israeli targets in Turkey to support an assassination plot led by Division 1500. This plot, targeting Israeli businessmen and tourists in Istanbul, was exposed by Turkish authorities in June 2022.
This isn't cyber espionage in isolation. The department's women spent time identifying and profiling Israeli nationals in Turkey so that IRGC operatives could attempt to kill them. The cyber reconnaissance directly enabled planned terrorism.
This connection demonstrates how Department 40 fits into the IRGC's broader operational structure. They're not a standalone hacking group. They're an intelligence and targeting arm that supports kinetic operations across the region.
The Kashef System
For years, the department has been hacking companies and stealing data. But what do they do with it all? They built a system called Kashef (کاشف) - "Discoverer."
Kashef is a comprehensive surveillance platform for tracking Iranian citizens and foreign nationals. The leak includes a video from the department's internal network showing the system in use. An employee walks through the interface, demonstrating how they track people.
The platform pulls data from multiple IRGC Intelligence divisions:
- Department 1530 - Persian Gulf Region (حوزه خلیج فارس)
- Department 1540 - Zionist Regime/Israel (رژیم صهیونیستی)
- Department 1550 - America (آمریکا)
- Department 1560 - Nationals Administration (اداره اتباع)
The capabilities and stored and extracted data in the third version of the Kashef software are:
Personal Data:
- Personal information and identity IDs
- Contact numbers (landline, mobile, virtual)
- Personal characteristics
Travel and Movement:
- Foreign travels of Iranians
- Entry of individuals to diplomatic premises
- Vehicle entry to diplomatic premises
Citizenship and Status:
- Dual citizenship records
- Holders of Iranian second citizenship (Ministry of Interior data)
- Students abroad
Business and Networks:
- Companies related to foreign affairs
- Social networks
- List of international colleagues
The Drone Program
This is where Department 40 crosses from cyber operations into terrorism.
The leaked documents reveal that Abbas Rahrovi and department members have been producing explosive drones in collaboration with other Iranian companies. The program isn't a side project. It's designated as an official task of the Department.
One document explicitly lists the purpose of this activity as "Terror" (ترور). There's no ambiguity in the language. The array categorizing the activity clearly registers that the purpose is terrorism.
The Safir Explosive Drone Contract
The most significant document is the Safir Project contract, a procurement agreement for 30 explosive gliders signed in October 2021.
Drone
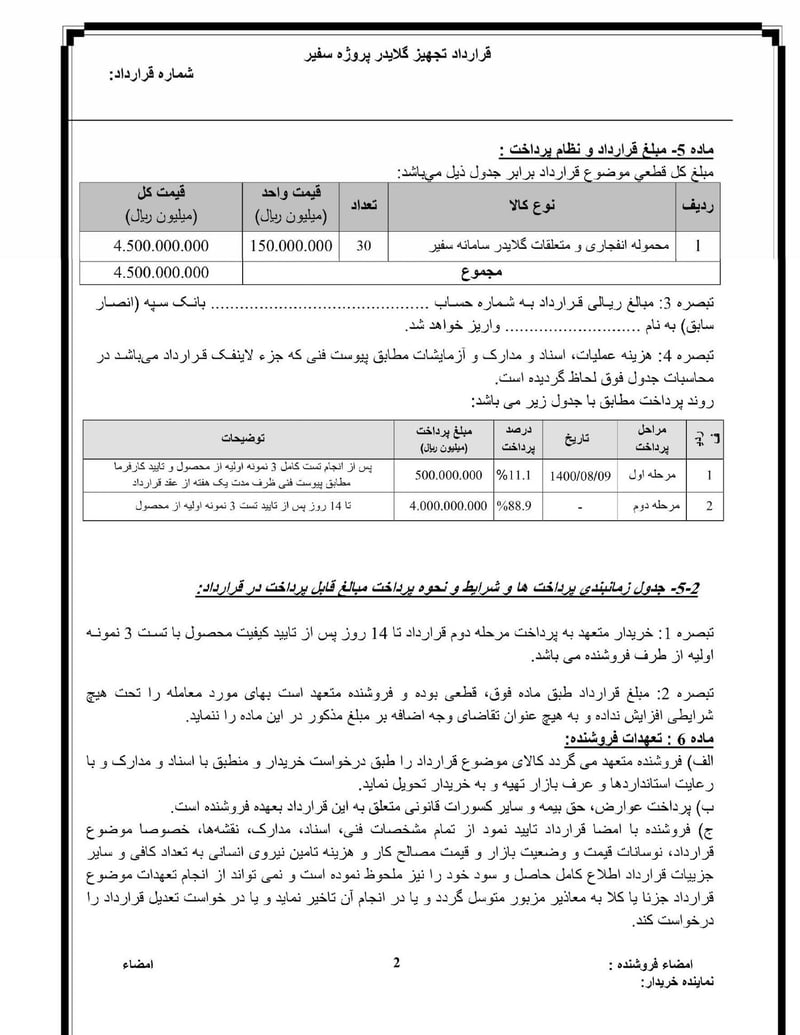





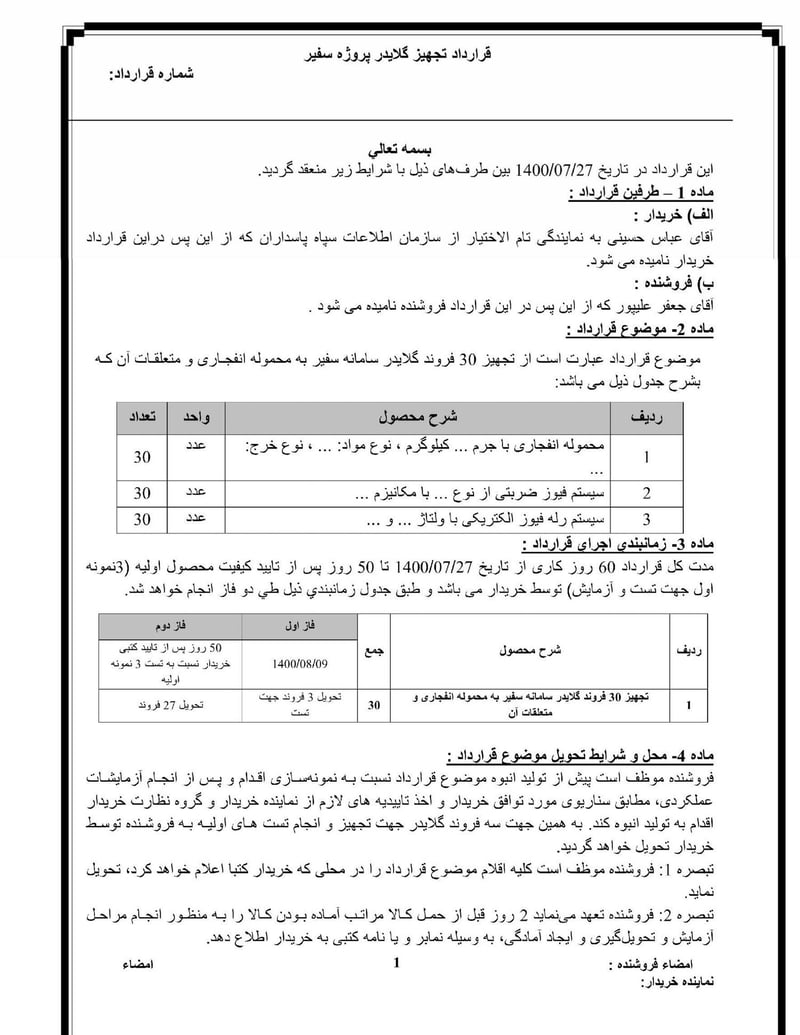
The contract is signed by Rahrovi using his Abbas Hosseini identity, the same alias he uses for front company registrations. This creates a paper trail between the cyber unit head and weapons procurement for terrorist operations.
The Safir system is designed for assassination operations. Unlike larger military drones, these gliders are portable and can be deployed by small teams. The combination of impact and electrical fuses gives operators flexibility: immediate detonation on target or delayed detonation based on surveillance of target movements.
For a unit that tracks targets through compromised airline databases, hotel booking systems, and medical clinics, these weapons represent the kinetic end of the intelligence cycle. First they locate targets through cyber operations. Then they kill them with explosive drones.
The Master Operations Document
Perhaps the most significant leak is a five-page master operations document that details Department 40's complete operational portfolio. Each page covers a different category of activity, from assassination targeting to advanced weapons development.
The Morianeh Project





Page 1: The Morianeh Project - Targeting Saudi Prince Turki Al-Faisal
The document opens with details of a planned operation against Prince Turki Al-Faisal, codenamed the "Morianeh Project."
Prince Turki led Saudi Arabia's General Intelligence Directorate for 24 years (1977-2001), overseeing Saudi intelligence operations through some of the most critical periods in Middle Eastern history. He subsequently served as ambassador to the United Kingdom (2003-2005) and to the United States (2005-2007), building extensive connections with Western intelligence agencies and policymakers.
The Morianeh Project documentation includes:
- Intelligence Requirements: Specific collection tasks focused on Prince Turki's movements, security arrangements, communications, and personal networks
- Operational Planning: Coordination between Department 40's cyber reconnaissance and Division 1500's operational units
- Target Assessment: Analysis of vulnerabilities in the prince's security posture
Targeting a senior member of the Saudi royal family with this level of intelligence and diplomatic experience represents a significant escalation. Prince Turki's knowledge of Saudi intelligence operations, his relationships with Western agencies, and his public criticism of Iranian policies make him a high-value target for both intelligence collection and potential assassination.
Page 2: Turkey Operations - Medical Clinics and Kidnapping Infrastructure
The second page details operations in Turkey, a critical theater for Iranian intelligence given the large number of Israelis who travel there for medical procedures, tourism, and business.
Forensic Tools Arsenal: The document lists the department's reverse-engineered forensic software for extracting data from mobile phones:
- UFED (Cellebrite)
- Oxygen Forensic
- SPF9139 SmartPhone Forensic System
- Final Mobile forensics
- FAW - Forensics Acquisition Of Web Sites
- xw_forensics
- RX-Unlocker
- Elcomsoft Phone Password Breaker
- Symphony Senstar
- AmpedFIVE
Sayyad Phishing Platform: The document describes the "Sayyad" (Hunter) platform designed for phishing operations. This system gives the cyber team the capability to bypass Google security layers and access Gmail accounts of targets. The platform represents a custom tool specifically designed to defeat Google's account protections.
Page 3: 2021 Technical Operations
The third page documents Department 40's 2021 technical equipment and surveillance operations. The document lists eight specific projects completed that year:
Technical equipment of Hani case (Naser Hadian) - Surveillance operation against an individual target
Technical equipment and monitoring of UAE Embassy in Tehran
Technical equipment and monitoring of Swiss Embassy garden in Tehran - The Swiss Embassy represents US interests in Iran
Identification for technical equipment of Oman Embassy in Tehran
Technical equipment of Maneli office unit
Technical equipment of atomic energy car case - Surveillance of a vehicle connected to Iran's atomic energy sector
Purchase of storage equipment from Russia (latest version of Papyrus system) - Procurement of Russian surveillance technology
Prepare drone images from British Embassy garden - Aerial surveillance of British diplomatic compound
These operations demonstrate the department's dual function: conducting foreign cyber operations while also running domestic counter-intelligence and surveillance against Western embassies and internal targets. The "atomic energy car case" and "Naser Hadian" operations suggest monitoring of individuals with access to sensitive information.
The document also notes the department completed over 40 forensic extraction missions, including email accounts, virtual accounts, mobile phones, personal computers, and storage devices.
Page 4: Advanced Weapons Systems
The fourth page provides specifications for two weapons systems under development or procurement.
Safir Balloon/Glider System
The Safir system detailed here goes beyond the contract documentation. The specifications describe:
- Launch capabilities from various platforms
- Guidance systems for precision targeting
- Payload capacity for explosives
- Range and endurance parameters
- Recovery or impact detonation modes
The system is designed for covert deployment by small teams operating in foreign countries.
Ofogh Suicide Drone
The Ofogh ("Horizon") is a jet-powered suicide drone developed by "knowledge-based teams" with specifications that make it suitable for high-value target assassination:
- Payload: Over 60 kilograms of explosive material
- Speed: Over 600 kilometers per hour
- Range: Over 100 kilometers to target, with capability for longer ranges by adjusting payload and adding fuel
- Guidance: Precision targeting systems for single-target elimination
Unlike the slower Safir glider, the Ofogh is designed for rapid strikes against moving or time-sensitive targets. Its combination of heavy payload, high speed, and extended range makes it suitable for assassination operations deep in enemy territory. The speed makes interception extremely difficult.
Page 5: 2022 Programs
The final page outlines Department 40's 2022 operational programs and development priorities. The document lists six specific programs:
Nuclear Facility Cyber Attacks
Identification and cyber offensive action on centers related to "Zionist regime atomic energy" to strike and create disruption in nuclear activities.
Public Services Disruption
Cyber offensive action to create disruption in public services to Israeli citizens and disrupt urban life processes.
Psychological Operations Campaign
Design perception operations and cyber offensive to create "negative psychological state and bewilderment" using online media and collective communication to occupy public attention and intelligence services.
Long-Range Audio/Visual Interception System
Design and development of audio and image interception systems with range over 1 kilometer for use in special technical missions.
Vehicle-Based Surveillance System
Design of audio and image interception system for vehicle deployment in special technical missions.
Suicide Quadcopter for Targeted Terror Operations
Design and construction of suicide quadcopter specifically for assassination operations.
This commercial drone technology adapted for targeted killing offers:
- Low cost per unit
- Easy procurement of components
- Quiet approach to targets
- Urban operational capability
- Difficult attribution
The 2022 programs show Department 40 expanding across multiple domains: cyber attacks on critical infrastructure, psychological warfare, advanced surveillance systems, and drone-based assassination capabilities. The explicit reference to "targeted terror operations" removes any ambiguity about the program's purpose.
The exposure of their identities, their organizational structure, and their operational details represents a catastrophic security failure for the IRGC. Every front company is burned. Every facility is compromised. Every operative is exposed.


