The fourth release of leaked documents from Iran's APT35 (Charming Kitten) operation exposes something previous leaks haven't: the complete financial backbone and infrastructure procurement system that keeps this IRGC-affiliated hacking group operational. Three CSV files released by the anonymous KittenBusters collective reveal a detailed accounting system tracking everything from Bitcoin payments to ProtonMail credentials to Iranian LTE network allocations.
This isn't just another list of domains or malware samples. These files represent the group's operational ledger from 2021 through late 2024, documenting how state-sponsored cyber operations actually fund themselves, what services they buy, and how they blend international anonymization infrastructure with domestic Iranian networks.
The Service Registry
The file labeled "0-SERVICE-Service.csv" reads like a procurement database for a cybercrime operation. Spanning from 2021 to 2025, it catalogs every piece of infrastructure the group purchased or maintained, complete with credentials, costs, and in some cases, explicit notations of purpose.
The registrar preferences tell their own story. Namecheap and Namesilo dominate the domain registration entries, with occasional use of Shinjiru for operations requiring less Western oversight. Each entry includes the email account used for registration, typically ProtonMail addresses like may[.]arnold@protonmail[.]com or ronald[.]iverson@protonmail[.]com, along with the full passwords.
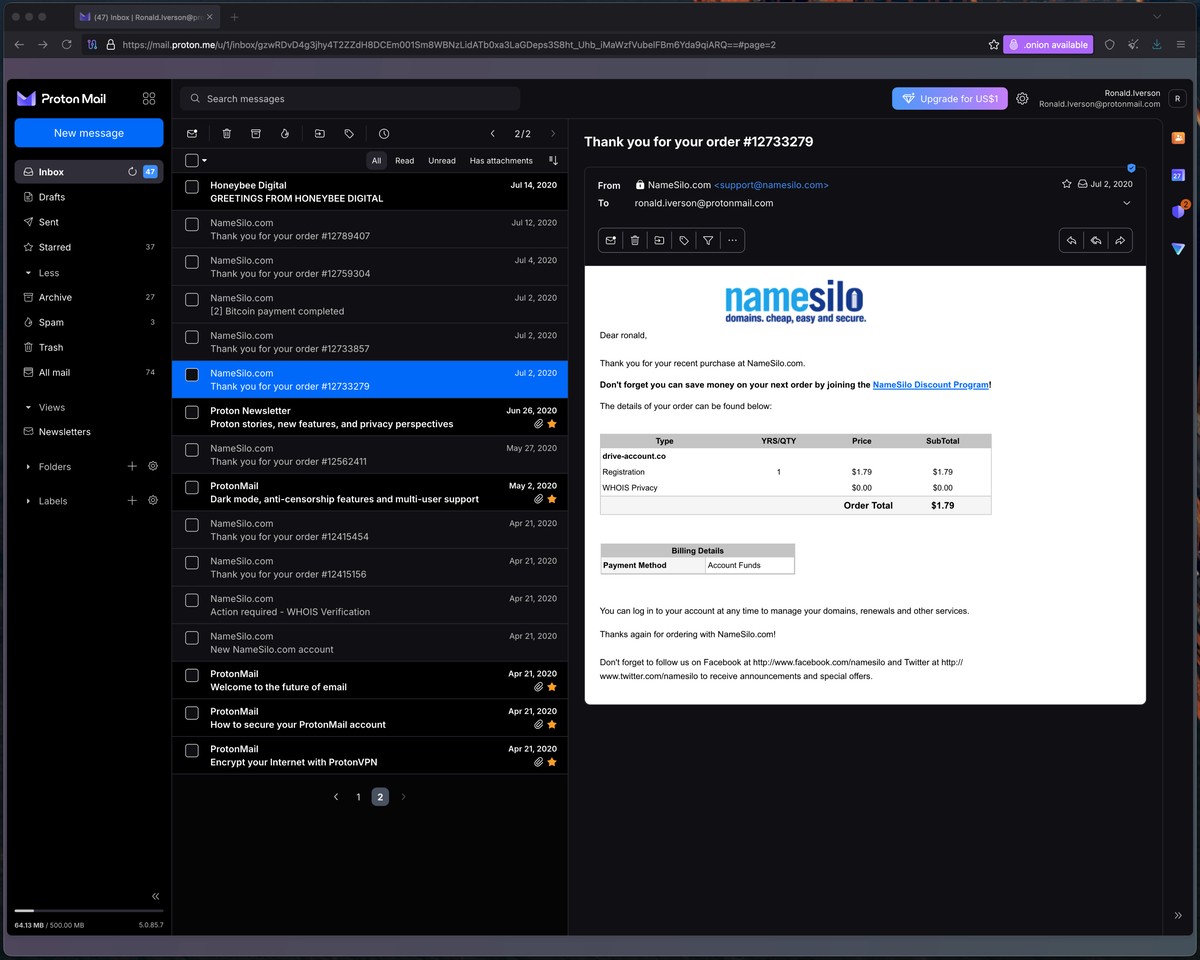
I verified access to both the may[.]arnold and ronald[.]iverson ProtonMail accounts using the leaked credentials. Both accounts remain active as of this writing.
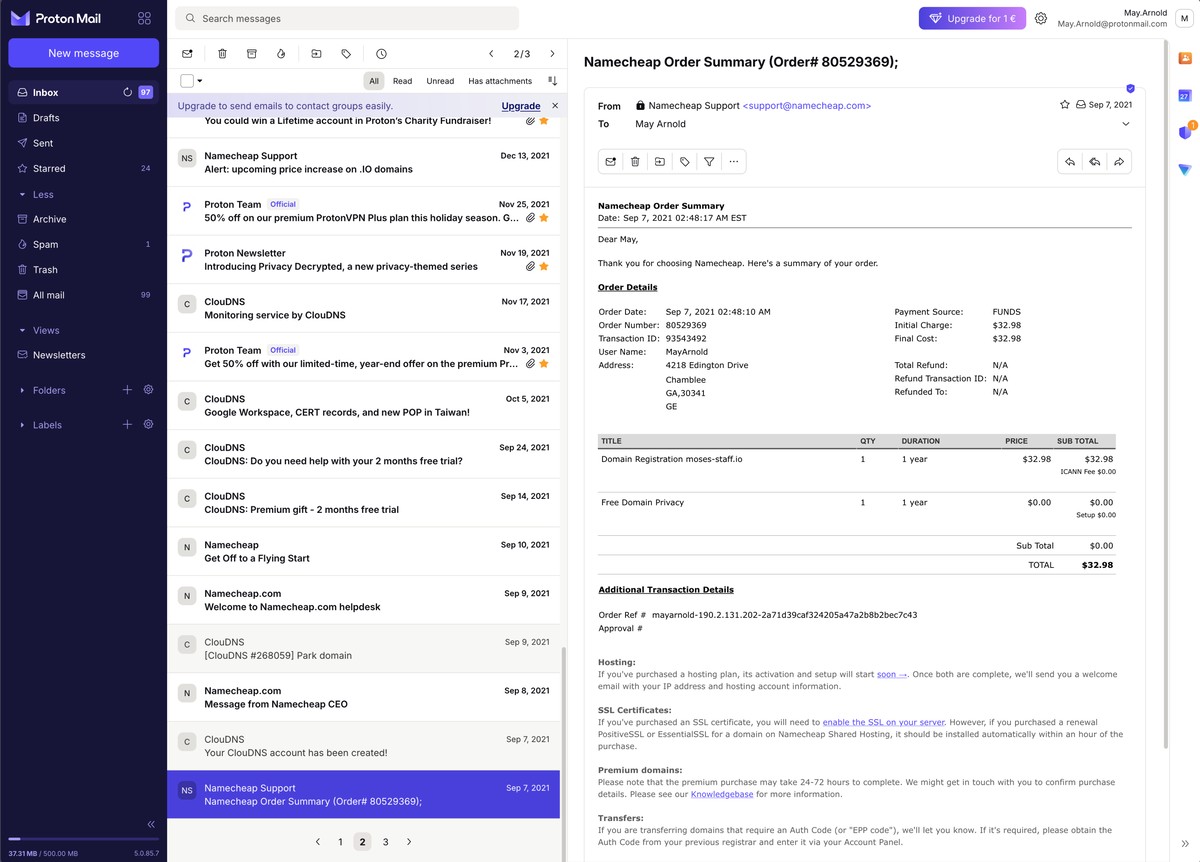
DNS management runs primarily through Cloudns[.]net, with some operations using Modern Izmir as a backup provider. The spreadsheet documents dozens of domains across these services, with costs ranging from $3 for basic DNS to $15-20 for premium registrations.
The hosting infrastructure breaks into two distinct categories: legitimate European providers and services explicitly designed for anonymity. For standard operations, the group uses EDIS Global, EDIS AT, and DediStart for dedicated servers. The leaked data shows IP allocations primarily in these ranges: 95[.]169[.]196[.]* (multiple addresses), 185[.]141[.]63[.]* (multiple addresses), and various European datacenter ranges.
The more sensitive operations run on anonymization-focused hosts. TheOnionHost and Impreza Host, both known Tor-friendly providers, appear multiple times with costs ranging from $50 to $85 per service. ISHOSTING and Ultrahost handle additional VPS instances across geographic locations.
What makes this documentation particularly damning is the notation field. Several entries include tags like "phishing," "malware," or specific operation identifiers. These aren't accidental classifications; someone maintaining this spreadsheet knew exactly what each piece of infrastructure supported.
The email infrastructure deserves special attention. The spreadsheet lists dozens of ProtonMail accounts with complete credentials. Each email follows a pattern of Western names: ronald.iverson, may.arnold, and similar constructions designed to appear legitimate in phishing operations.
SMS verification services get equal attention. The group maintains accounts with SMSpva[.]com, OnlineSim[.]io, and PVAPins[.]com, services that provide temporary phone numbers for account verification. These entries include API keys, account credentials, and cost tracking, with prices typically ranging from $5 to $15 per service.
Several Skype accounts appear in the registry as well, used for what the notes describe as "communication" operations. The inclusion of social media-style accounts alongside technical infrastructure suggests these personas get developed as complete digital identities, not just throwaway addresses.
The leaked credentials connect directly to previously identified IRGC personnel. Many of the usernames and passwords appearing in these files show connections to Mohsen Foroughi (national ID: 1467932698), identified in earlier reporting as the equipment procurement officer responsible for acquiring technical supplies on behalf of the IRGC. The operation itself operates under Abbas Rahrovi, also known as Abbas Hosseini (national ID: 4270844116), who commands overall operations through multiple shell companies.
One such front company, "Zharf Andishaan Tafakkor Sefid" (Deep White Thinking Institute), bears the signature of Manouchehr Vosoughi Niri, an official IRGC Intelligence Organization authority. Documents from this shell company identify Mohammad Erfan Hamidi Aref (national ID: 0023199709, born June 12, 2000) as operational staff. The appearance of these names and identification numbers throughout the leaked infrastructure files provides direct attribution linking this technical infrastructure to specific IRGC-IO personnel and their cover organizations.
One domain that appears in this infrastructure list gained particular notoriety in Google Cloud's threat intelligence reporting: dreamy-jobs[.]com. In March 2024, Mandiant (now Google Cloud Threat Intelligence) published detailed analysis of an Iranian counterintelligence operation running at least 35 fake recruitment websites targeting Iranian, Syrian, and Hezbollah security personnel. The "VIP Human Solutions" cluster, which included dreamy-jobs[.]com, operated from 2017 through 2023 as a sophisticated honeypot.

The site presented itself as "VIP job selection is a recruitment center for respected personnel and employees of Iran's security and intelligence organizations and institutions." It collected comprehensive personal information: names, birth dates, addresses, education history, and professional backgrounds. The operation used Israeli country codes (+972) for contact numbers and maintained a Telegram channel at t[.]me/DreamyJobs_com.
Google's report assessed with high confidence that this represented Iranian state activity supporting counterintelligence objectives, with weak operational overlaps to APT42, another IRGC-IO affiliated group. The appearance of dreamy-jobs[.]com in Charming Kitten's infrastructure registry directly links this counterintelligence operation to APT35's broader activities, confirming what researchers suspected: these aren't separate teams working independently, but rather different operational focuses within a coordinated intelligence apparatus.
The Bitcoin Ledger
The financial records in "0-SERVICE-payment BTC.csv" provide something rare in state-sponsored hacking analysis: a complete 19-month financial trail showing exactly how the operation paid for its infrastructure.
The ledger runs from April 10, 2023, through November 12, 2024, documenting approximately 50-60 transactions. Each entry includes transaction date, USD amount, Euro amount when applicable, Bitcoin amount, transaction fee, service description, total dollar payment, and receiving wallet address. Bitcoin amounts range from 0.004532 BTC at the high end down to 0.000323 BTC for smaller purchases. The dollar equivalents span $10 to $197, with most transactions falling in the $30-70 range.
The "For Service" column reveals operational priorities. Domain registrations appear frequently, often with specific domain names listed. SSL certificate purchases show up regularly, indicating attention to appearing legitimate. Hosting renewals track numbered operations: #44, #70, #73, and similar designations that likely correspond to specific campaign infrastructure.
Some entries reference services by name: gassam[.]su, pvaipins, and other identifiable vendors. Others use generic descriptions: "domain," "hosting," "ssl," or just operation numbers. Transaction fees tell their own story. Fees range from $0.69 to $16.14, with higher fees appearing during periods of Bitcoin network congestion or for transactions requiring faster confirmation. Someone managing these payments understood Bitcoin fee markets and adjusted accordingly.
The pattern of payments suggests regular operational funding. Transactions don't cluster around specific dates but instead spread relatively evenly across the 19-month period, indicating sustained operational tempo rather than campaign-specific surges.
Blockchain Verification
To verify the authenticity of the leaked payment ledger, I independently queried the Bitcoin blockchain using the mempool[.]space API for wallet addresses listed in the leaked documents. The blockchain data confirms these are real transactions that occurred exactly as documented.
Every verified wallet shows an identical operational pattern: exactly 2 transactions (one incoming, one outgoing), with current balances of zero. This "receive and immediately forward" behavior is deliberate operational security. The group uses single-use wallets for payments, immediately forwarding all received Bitcoin to another address. This makes tracking the ultimate destination of funds significantly harder.
Sample of verified addresses and amounts received:
- 3F2KWMSkjFdskQ2gV6pm4NA7JH2dx3jfCA (0.0029021 BTC)
- 3Ck5dxmGXG3u1i3H7CM4vBpTeohDweJuYL (0.00732509 BTC)
- 38Ai21L6mt7Qe2jnpxAZvjTLqKCYfjx9Am (0.00599523 BTC)
- bc1q9a8k39xpxeflsetdw92mzd98kg7gpcwsm2malh (0.00376661 BTC)
- bc1qtf2a865s7ncxcsdcwee8yyyqjhhkk9nn7ww98q (0.00381 BTC)
- 16JMV9srqVDrK9u6z5cgKQjxnbJJp6gSxi (0.00283809 BTC)
- 19cChyRjku4zMKPr7PtkNSAdp9JE6AmiL2 (0.00219417 BTC)
- bc1q567mrap7x4mwva2wlea3x9nc78pgp7dxspe6su (0.00053183 BTC)
- bc1qw0fqr597dqh3j8pe3c9gnl7vvkpgumxsak646g (0.00037153 BTC)
- 17cHK7neWyAq1imHgjc6wKqoX3gqPcUx4N (0.00097498 BTC)
The blockchain amounts precisely match the amounts listed in the leaked CSV file, confirming these aren't fabricated records but actual financial transactions. From just this sample of 10 addresses, the verified total is approximately (0.031 BTC), representing roughly $700-$1,400 USD during the 2023-2024 transaction periods. The leaked ledger contains 32+ additional wallet addresses, suggesting the complete financial trail documents significantly more transactions.
Not a single verified wallet retains any balance. This indicates funds were either immediately forwarded to operational wallets, converted to fiat currency, or consolidated into larger wallets for operational management. The uniformity of this pattern across all addresses shows sophisticated financial operational security practices.
The third file, "1-NET-Sheet1.csv," shifts focus from international anonymization services to domestic Iranian infrastructure. Though portions of the file show encoding corruption, the recoverable data reveals the group's Iranian operational base. Multiple entries document TD-LTE network services with Iranian characteristics: service codes in the 989412299914X series, 250-300GB data plans, 12-month service periods, and service dates in the Islamic calendar (1403, corresponding to 2024-2025).
IP allocations use Iranian address space: 5[.]202[.]186[.]76/30, 5[.]202[.]45[.]174, and 5[.]202[.]45[.]175. These aren't VPN endpoints or proxy servers. These are domestic Iranian network allocations, indicating the group's operational presence within Iran itself.
The file documents multiple network access points with their specifications. AsiaTech (Rohi) runs a 50Mbps connection at 185[.]142[.]95[.]244. Pishgaman operates a 40Mbps connection with IP blocks 185[.]212[.]193[.]240/29 and 185[.]212[.]195[.]32/29. Point 1 and Point 2, both designated as Basebox installations, run 50Mbps connections at 109[.]230[.]93[.]128/29 and 109[.]230[.]93[.]168/29 respectively. Heravi Point maintains a 30Mbps connection at 109[.]230[.]80[.]0/30.
The "Basebox" designation suggests wireless point-to-point links, possibly Ubiquiti BaseStation equipment commonly used in Iran for last-mile connectivity. The bandwidth specifications indicate these aren't just backup connections; 50Mbps links represent significant operational capacity.
A VOIP service entry references the domain 1543[.]ir, indicating the group maintains voice communication infrastructure as well. The Iranian top-level domain confirms domestic hosting. Additional entries mention TPLink MR6400 devices, which are 4G LTE routers commonly used for residential and small business internet access. The inclusion of these consumer-grade devices alongside professional infrastructure suggests either safe house operations or compartmentalized access points for operational security.
What started as APT35 malware samples and targeting lists has evolved into a comprehensive documentation of how Iran's cyber espionage apparatus actually operates. The next question is what the fifth episode will reveal.



