They called themselves cybersecurity experts. They're actually Tehran's digital hit squad.
Someone handed me the keys to the kingdom—gigabytes of data ripped from internal servers of Amnban, Sharif Advanced Technologies. This Iranian "security firm" that launched in 2018 with all the right credentials (Sharif University grads, Amir Kabir alumni, professional website at www[.]amnban[.]ir) just got turned inside out. And what poured out should make every airline passenger's blood run cold.
The hackers who promised to protect Iran's networks? They couldn't even protect their own. But their catastrophic failure is our revelation—because these files expose something monstrous: a state-sponsored operation harvesting millions of passengers' personal data for Iran's intelligence machine.

The breach cracked open their entire operation. Behind the legitimate facade of penetration testing and security consulting lurks something sinister. These aren't consultants—they're cyber mercenaries working for APT39, the notorious hacking group tied directly to Iran's Ministry of Intelligence and Security (MOIS).
The evidence is overwhelming: systematic attacks on Royal Jordanian, Turkish Airlines, Rwanda Airlines, Wizz Air, and nearly a dozen other carriers. This isn't security research. It's preparation for digital warfare.
The Intelligence Connection Exposed
Every authoritarian regime needs its digital soldiers. Iran's cyber-espionage units conduct what they call Cyber Network Exploitation (CNE)—spy speak for breaking into foreign networks to steal intelligence. But it doesn't stop at data theft. These operations enable Cyber Network Attacks (CNA) designed to cripple infrastructure, crash airport systems, and worse.
APT39, also known as Chafer, is MOIS's favorite attack dog. They don't chase money—they hunt intelligence on foreign airlines, government systems, telecommunications companies. Jordan. Turkey. UAE. If you're flying through the Middle East, you're in their crosshairs.
Here's where it gets personal: Amnban's CEO is Benham Amiri, already flagged by intelligence agencies for APT39 connections.
Behnam Amiri




But Amiri went further—he actually hired Ali Kamali, a hacker so toxic the FBI sanctioned him in 2020 for attacking American infrastructure. This isn't hiding in the shadows. This is brazen.
Ali Kamali


The internal servers identified another frequent visitor: Hamed Mashayekhi, a MOIS operative who seemed confident enough to walk through Amnban's offices as if he owned them.

The stolen files paint a clear picture: Amnban runs cyberattacks for Iranian intelligence, targeting airlines that hold sensitive data on millions of innocent travelers.
I found out that one of the company’s longtime employees, Arshia Akhavan (father’s name: Reza), has recently immigrated to the United States. It remains to be seen whether Homeland Security will detain him. It is not exactly clear how he was granted permission to enter the U.S., as his period of activity coincides precisely with the FBI announcement and the U.S. Treasury statement regarding APT39.
The Target List
The leaked documents reveal the full scope. Under the cover of "OSINT training," Amnban systematically probed:
A. Airlines: Royal Jordanian, Wizz Air, Turkish Airlines, AZAL, Etihad, Air Arabia, FlyDubai, Qatar Airways, Emirates, Oman Air, Kenya Airways, Air Tanzania, Air Botswana, Rwanda Airlines, LOT Airlines
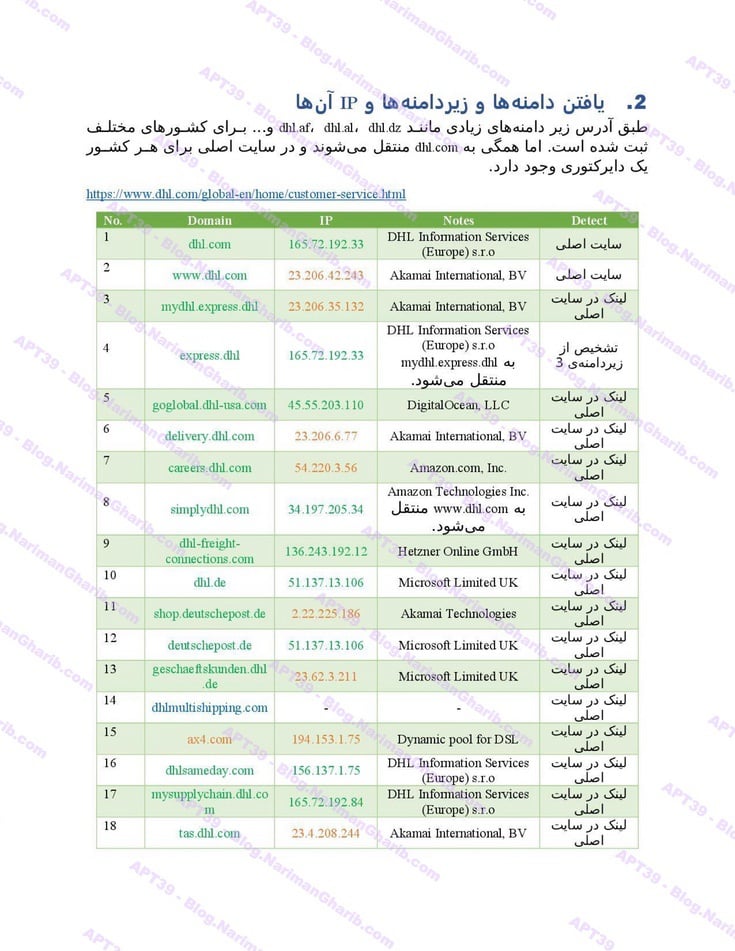
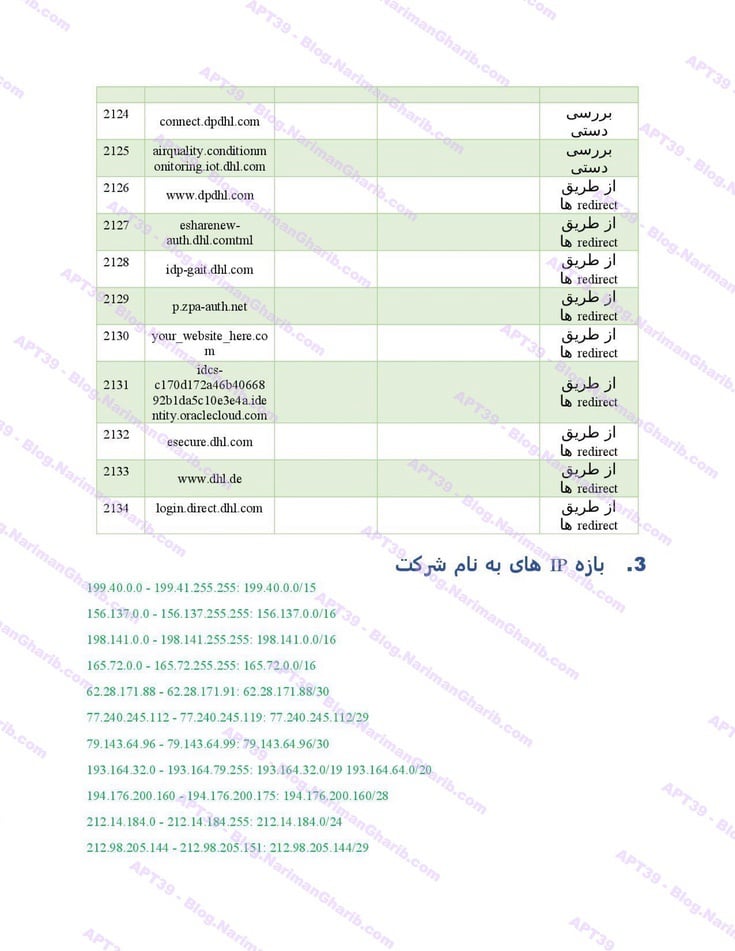
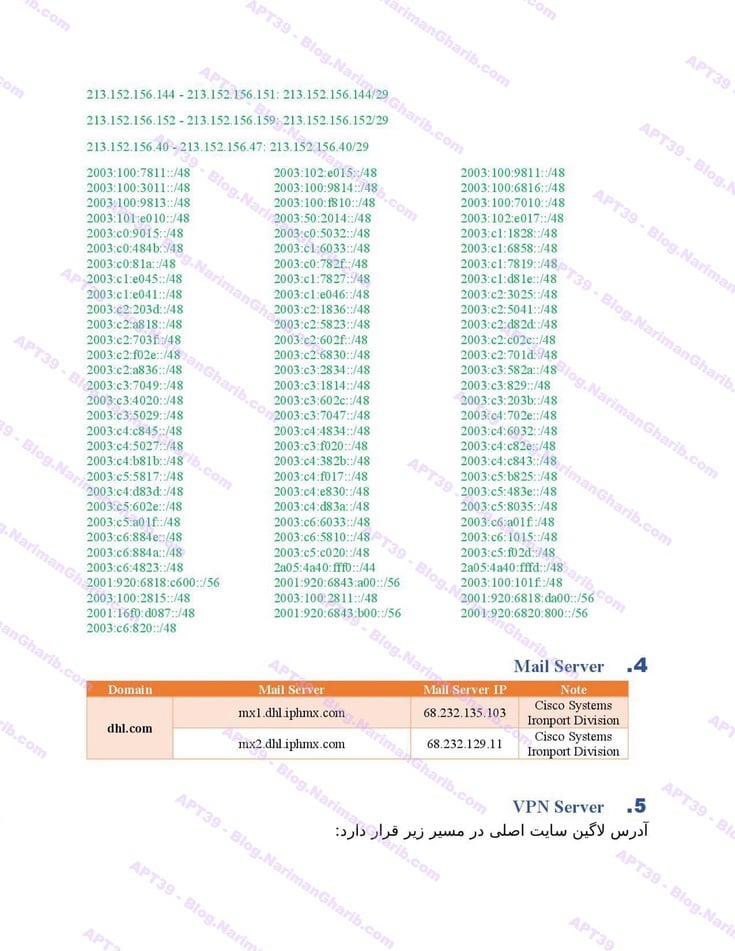
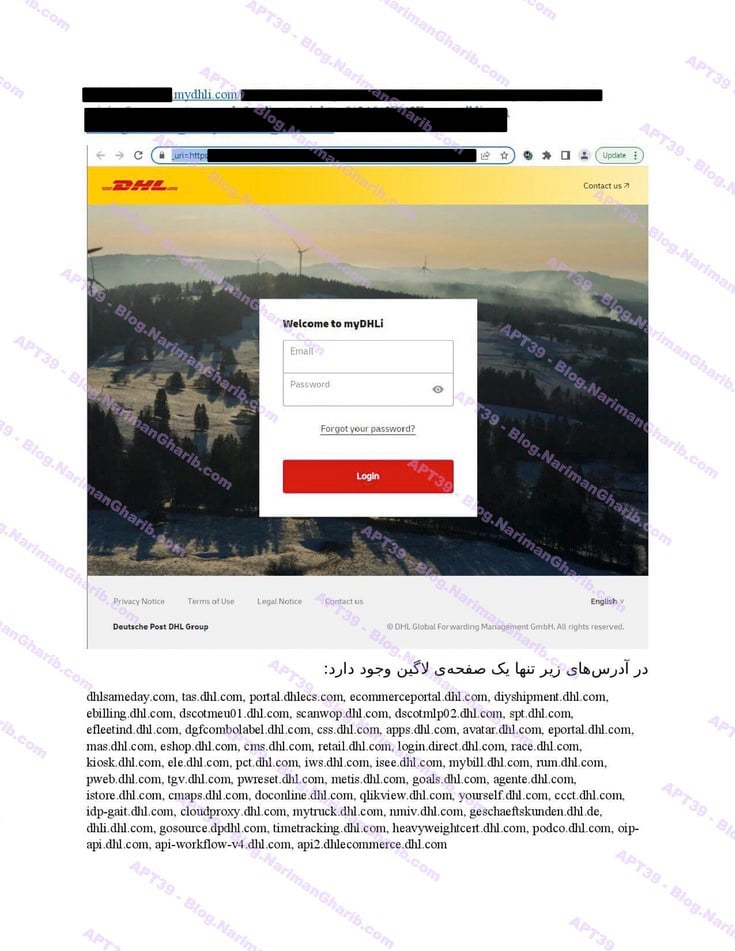
B. United States Freight Companies: FedEx, USPS, DHL
C. Russian Entities: Azimuth airline
D. Additional Freight Companies: Aramex
Note the pattern—airlines from countries aligned with Iran (Russia, Qatar) sit alongside carriers from nations Tehran considers hostile. Everyone's a target when you're building intelligence dossiers.
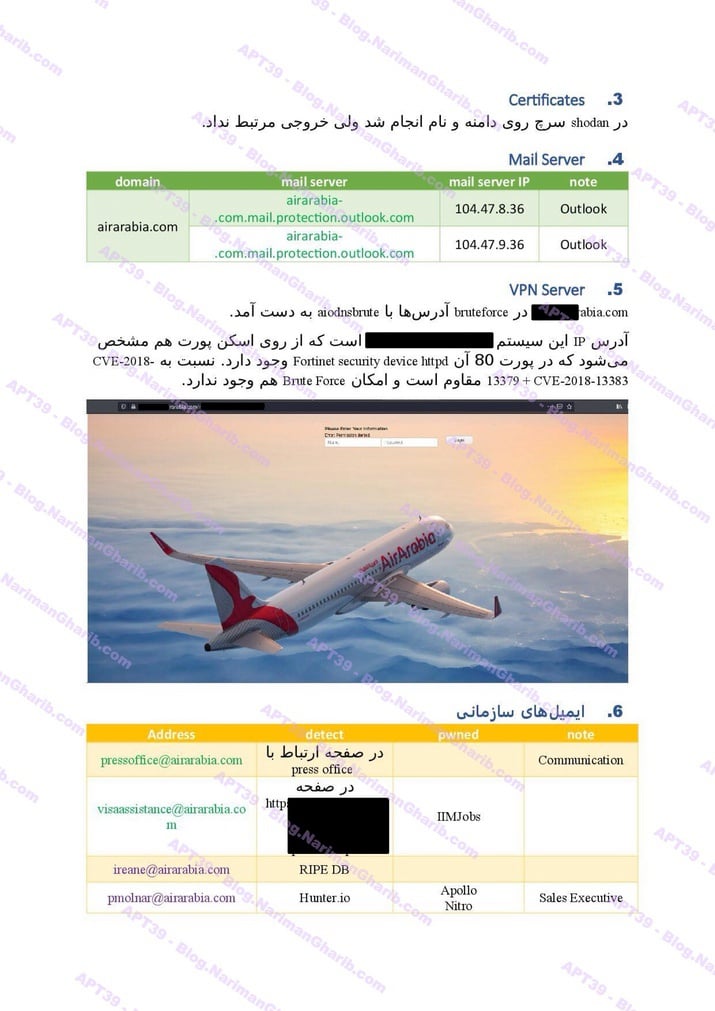
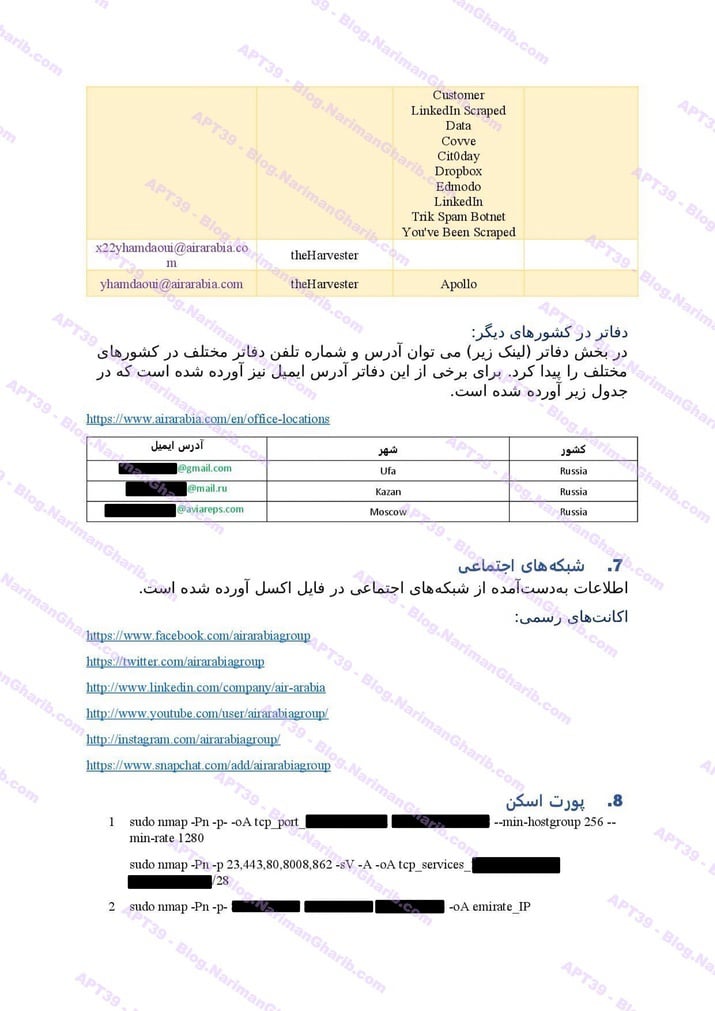
A sample of their reconnaissance reports:
Air Botswana
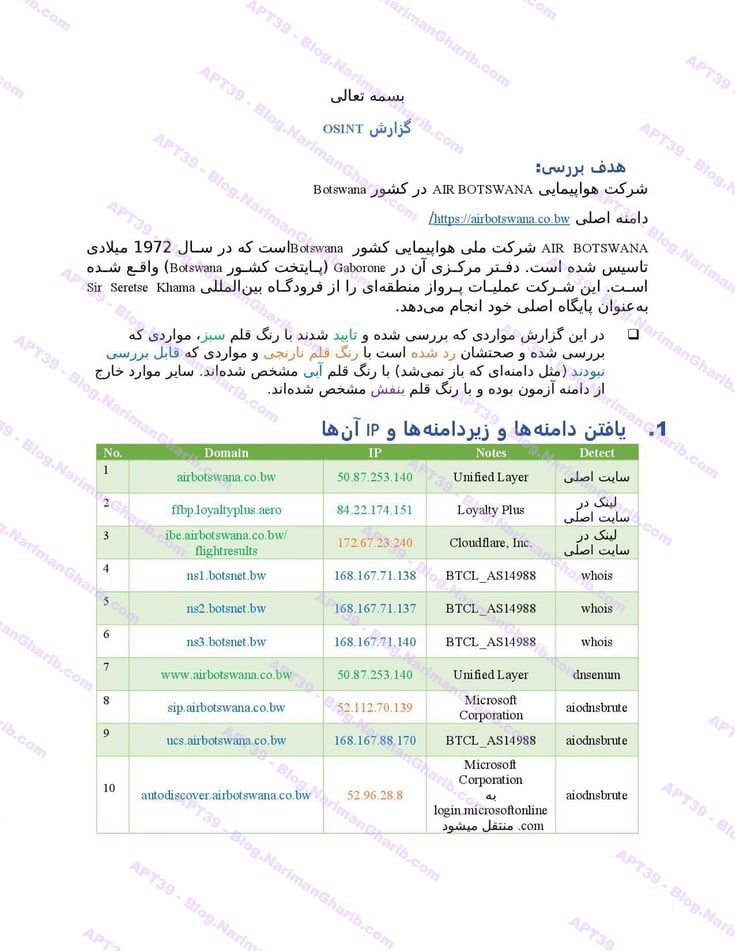
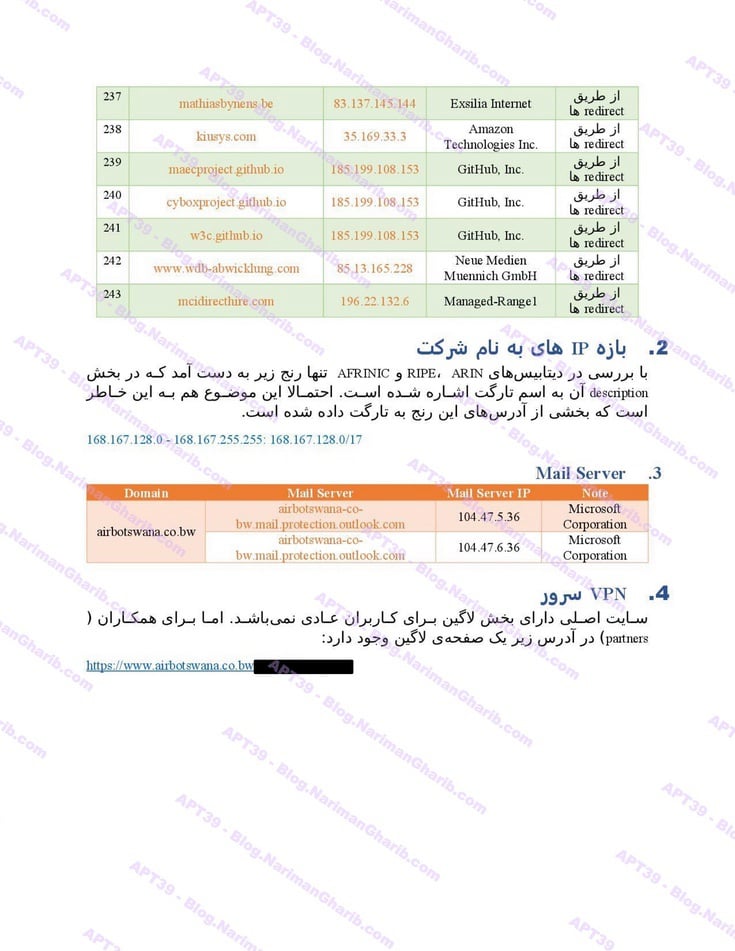
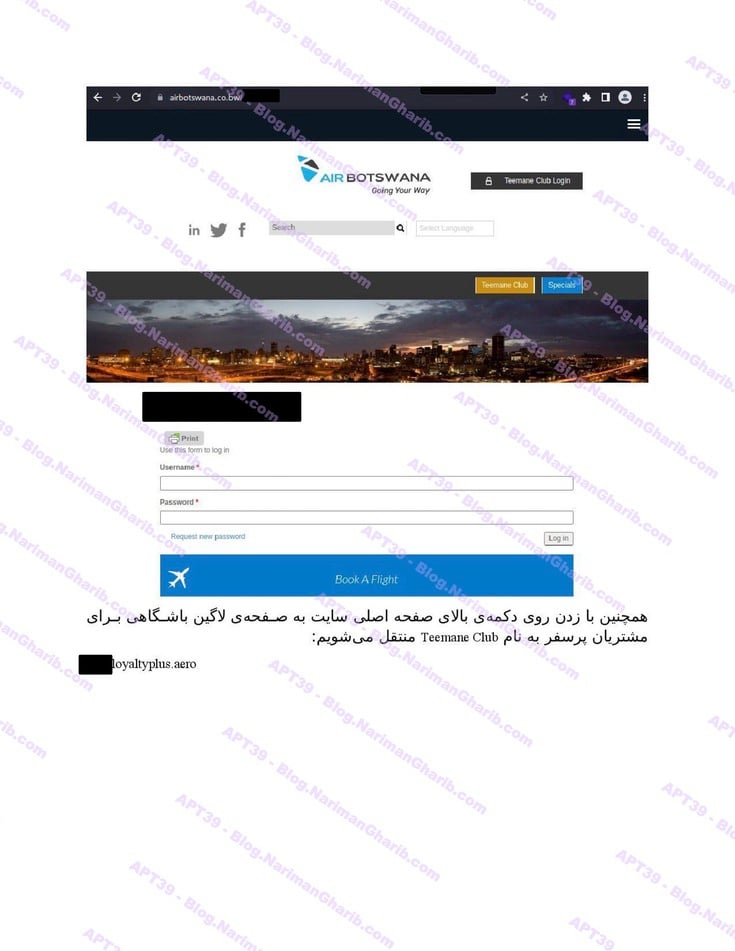
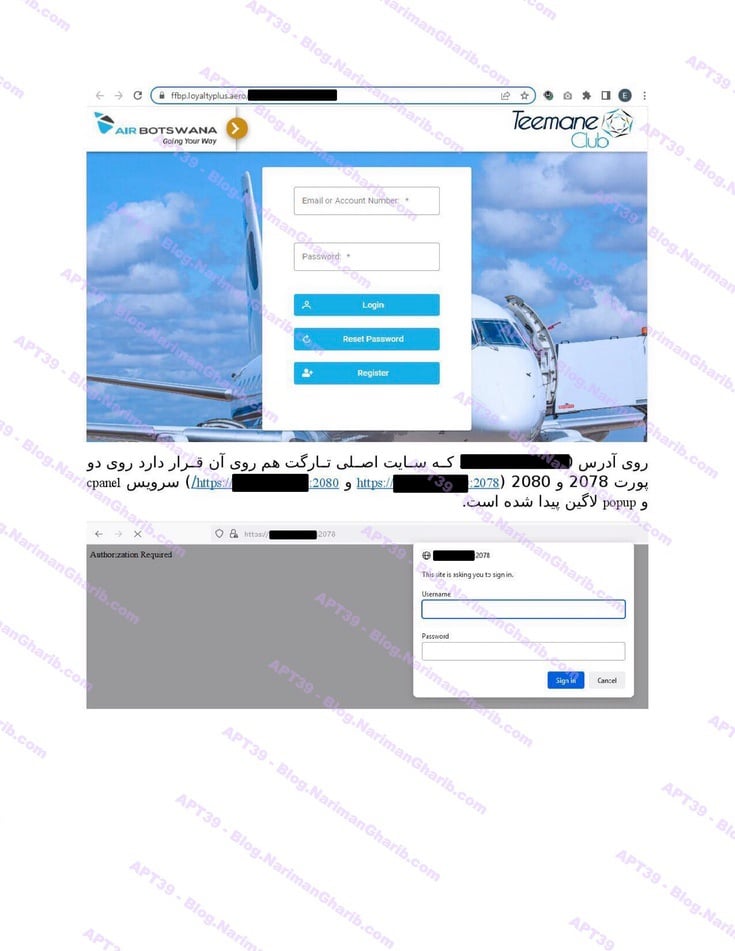
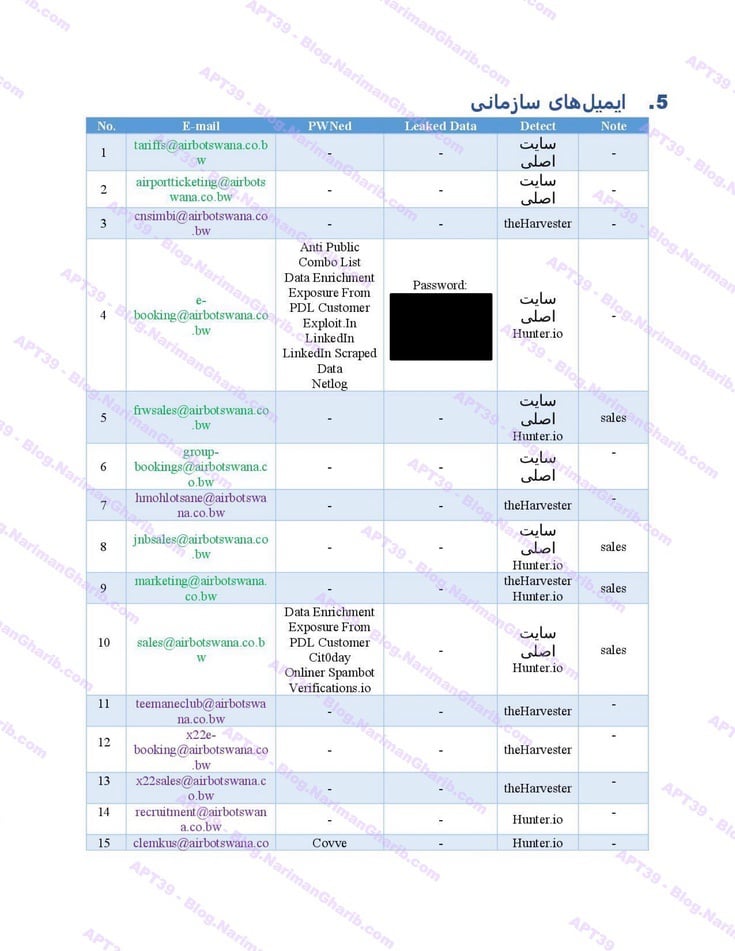
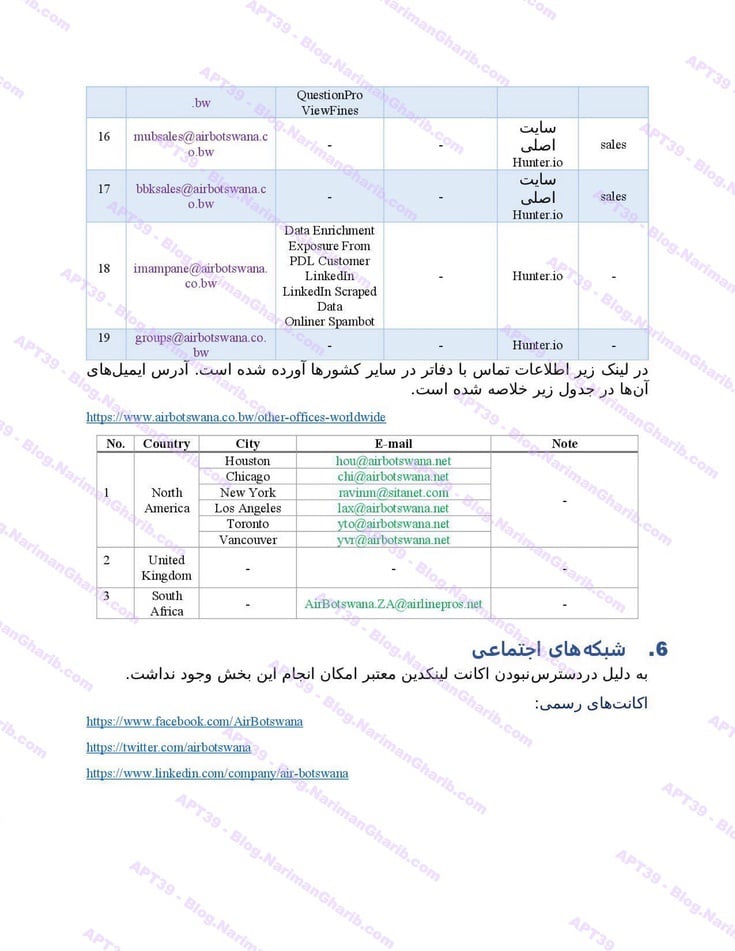
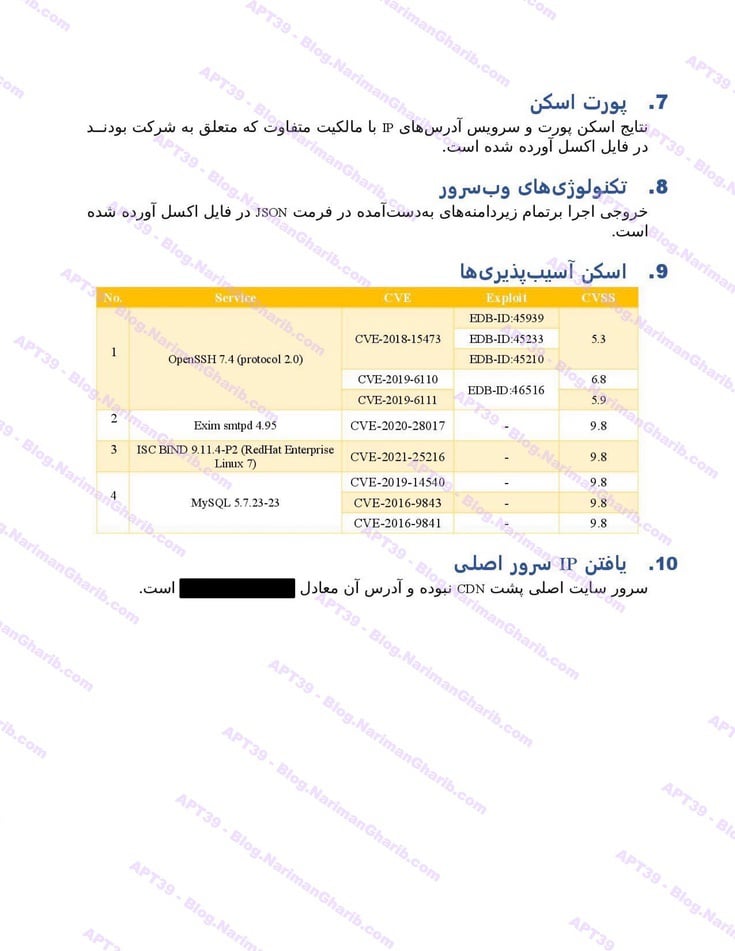
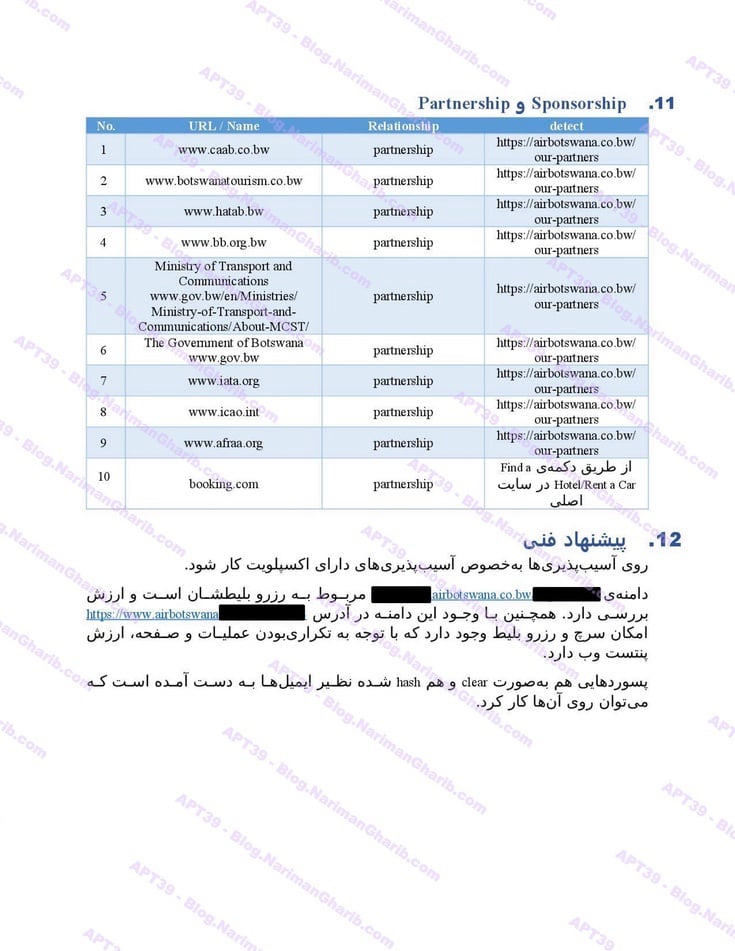
Air Tanzania

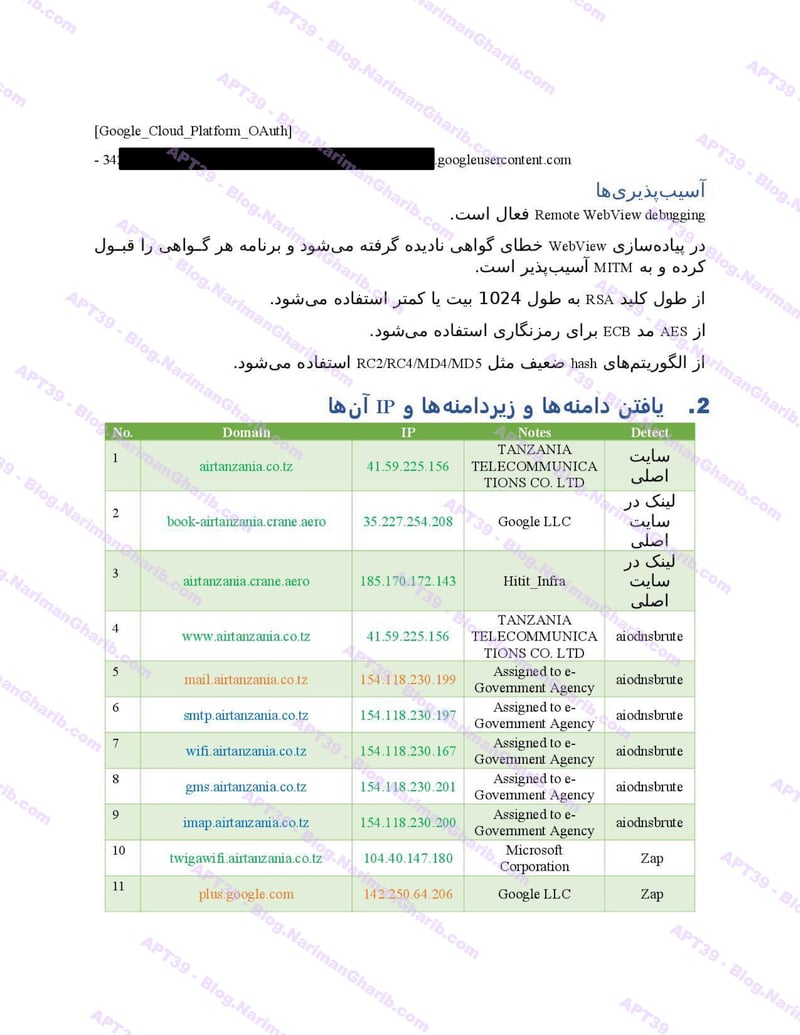
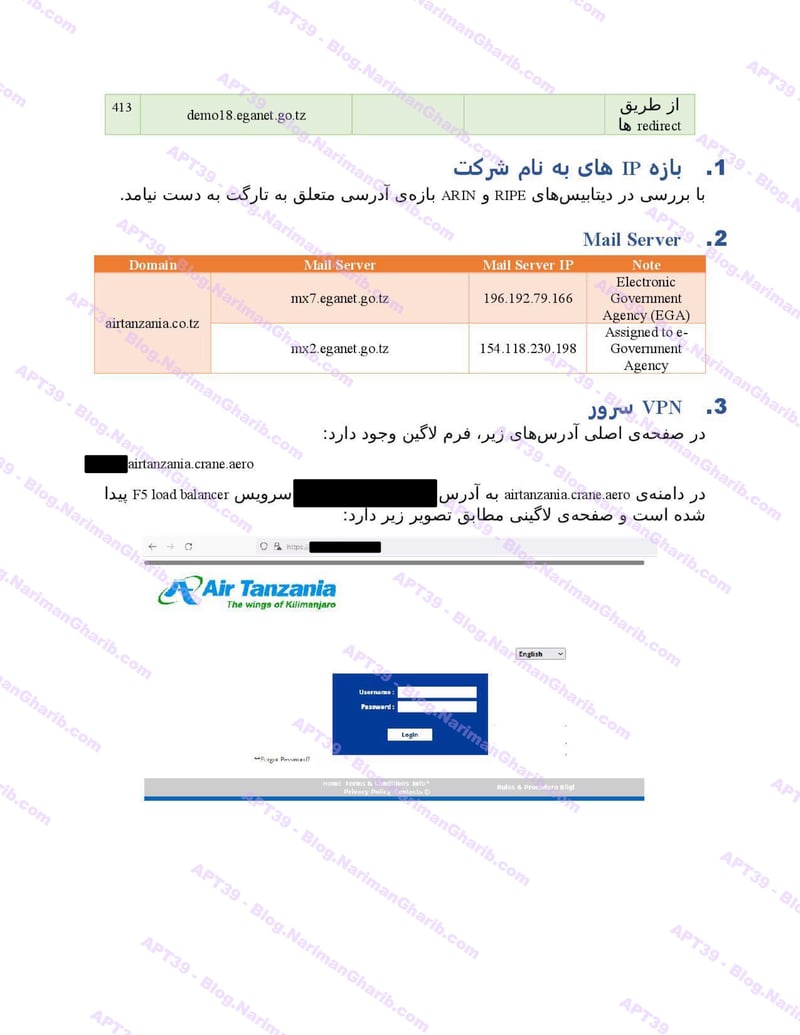
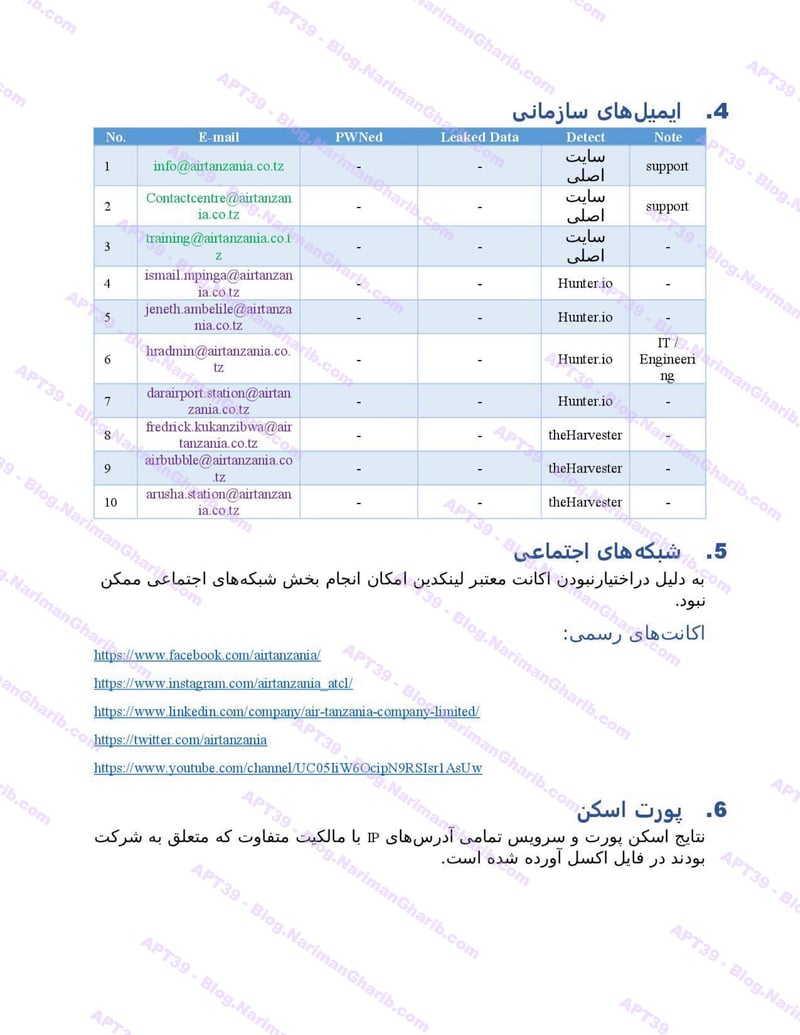
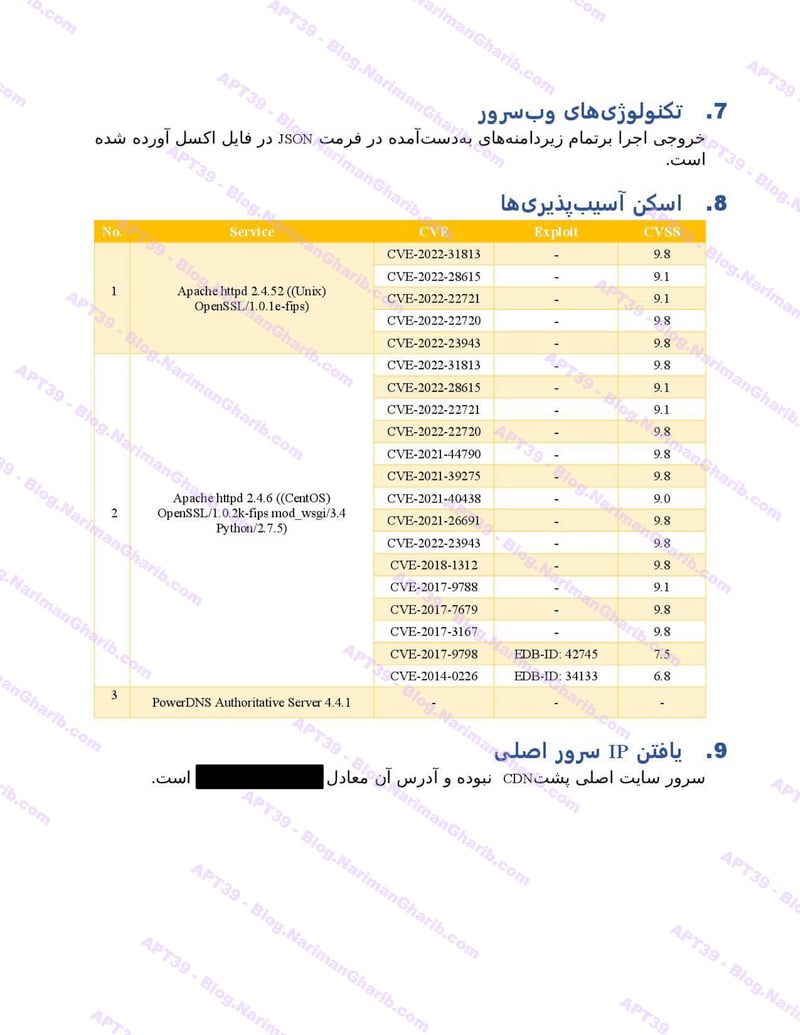
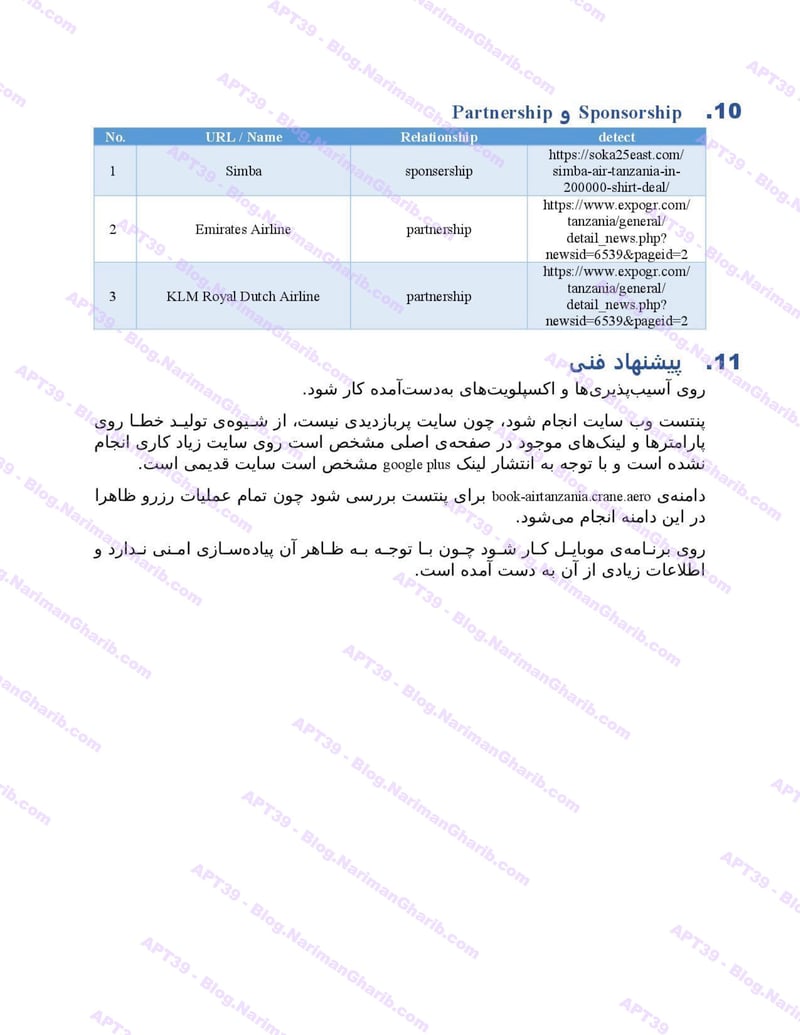
Air Arabia

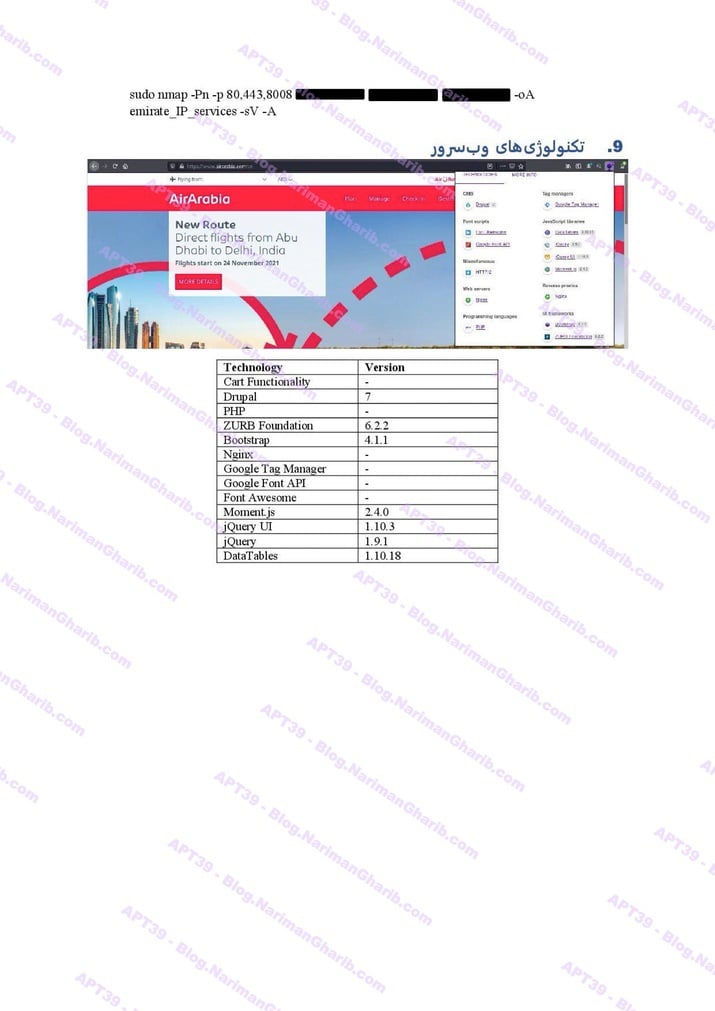
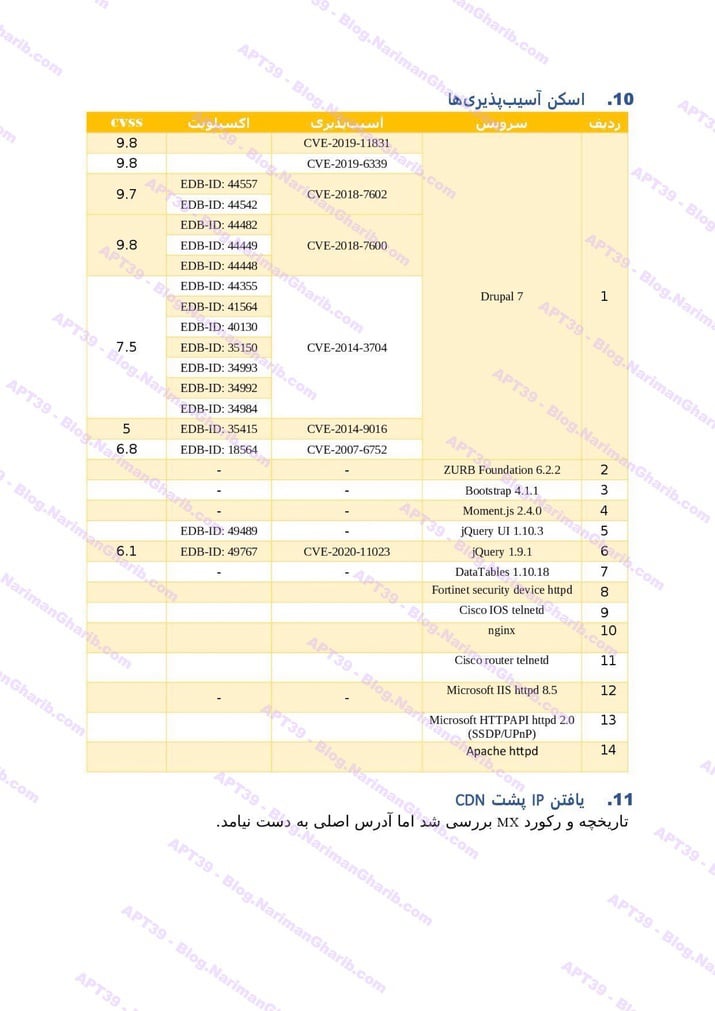
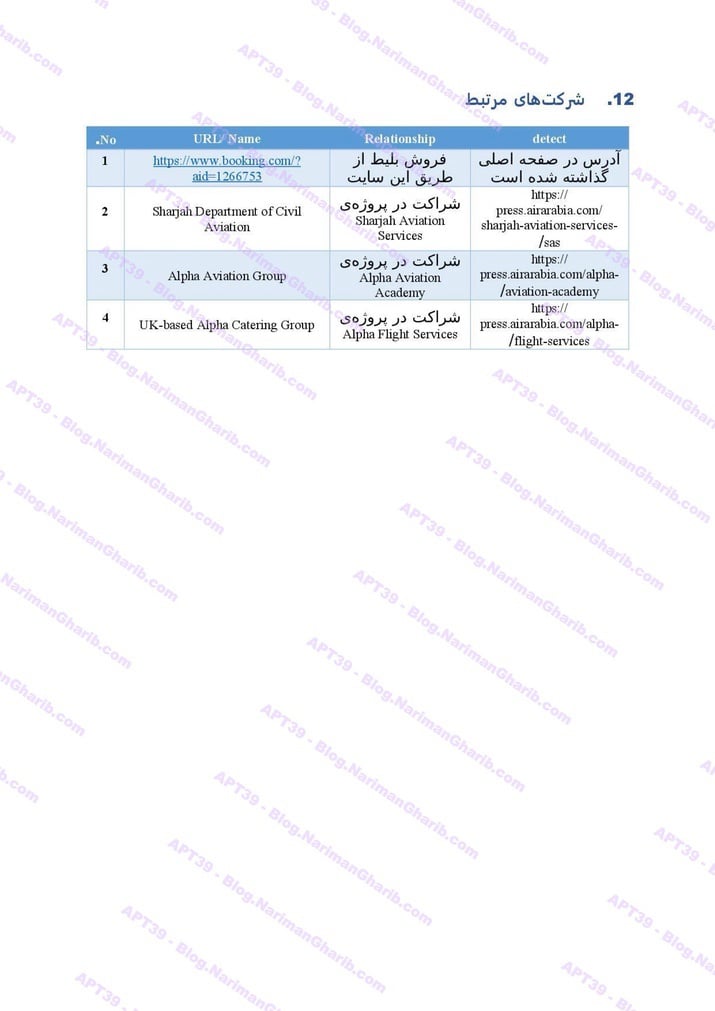
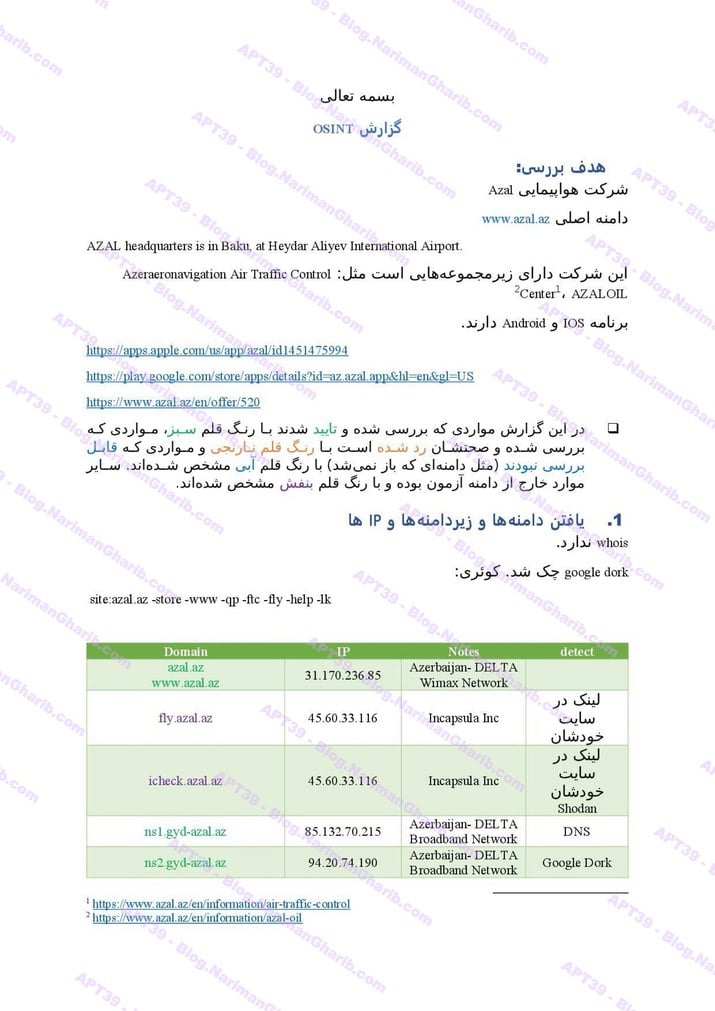
AZAL Air
DHL

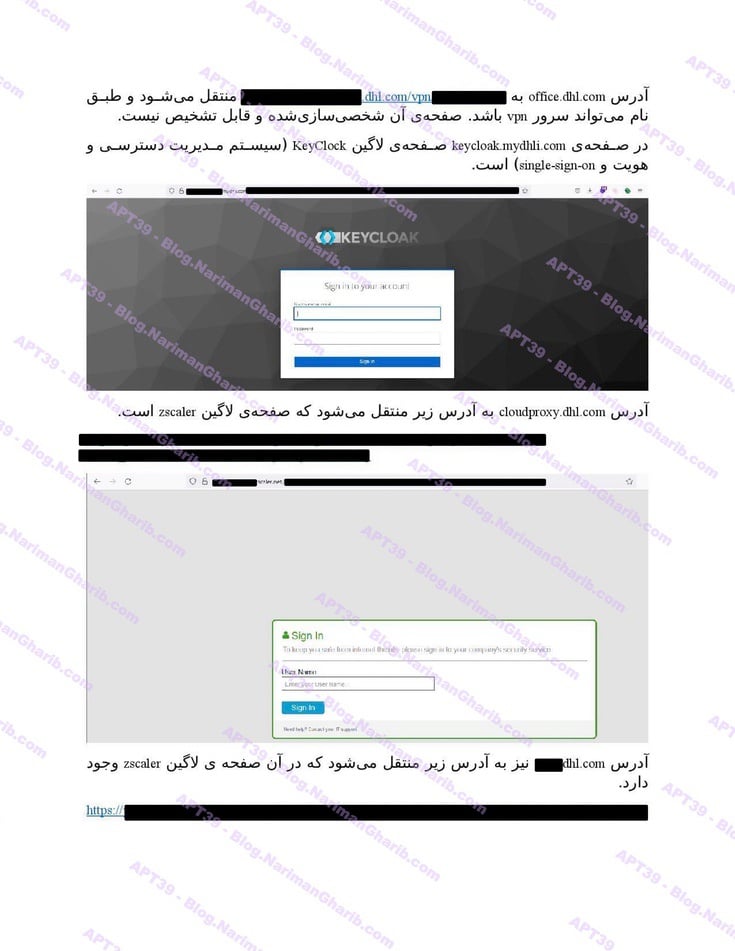
Emirates

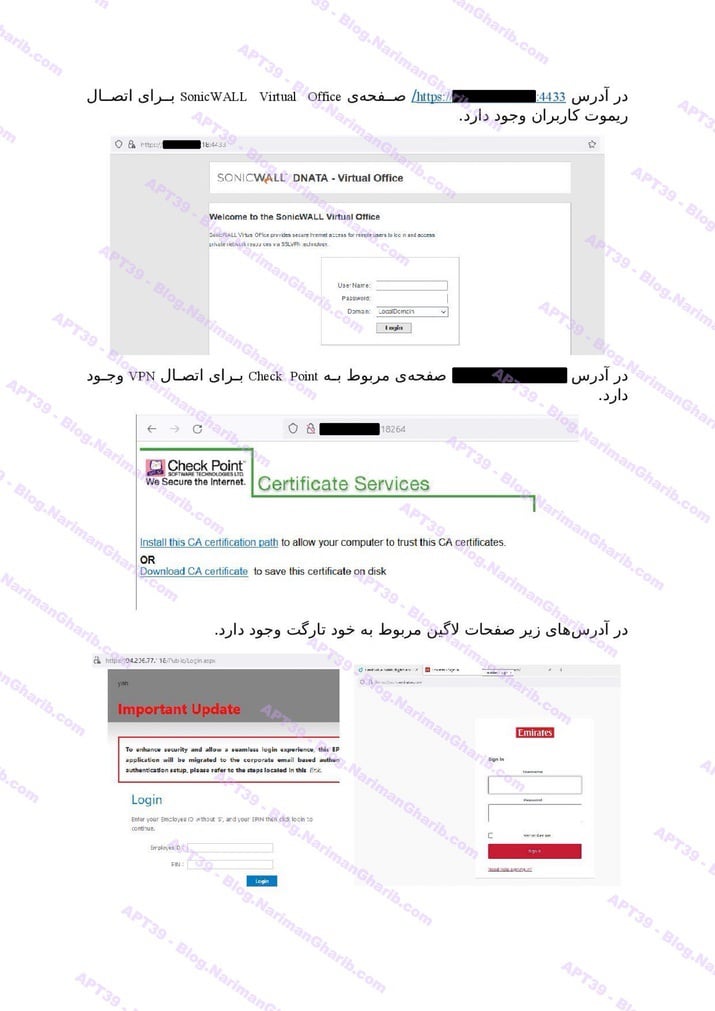
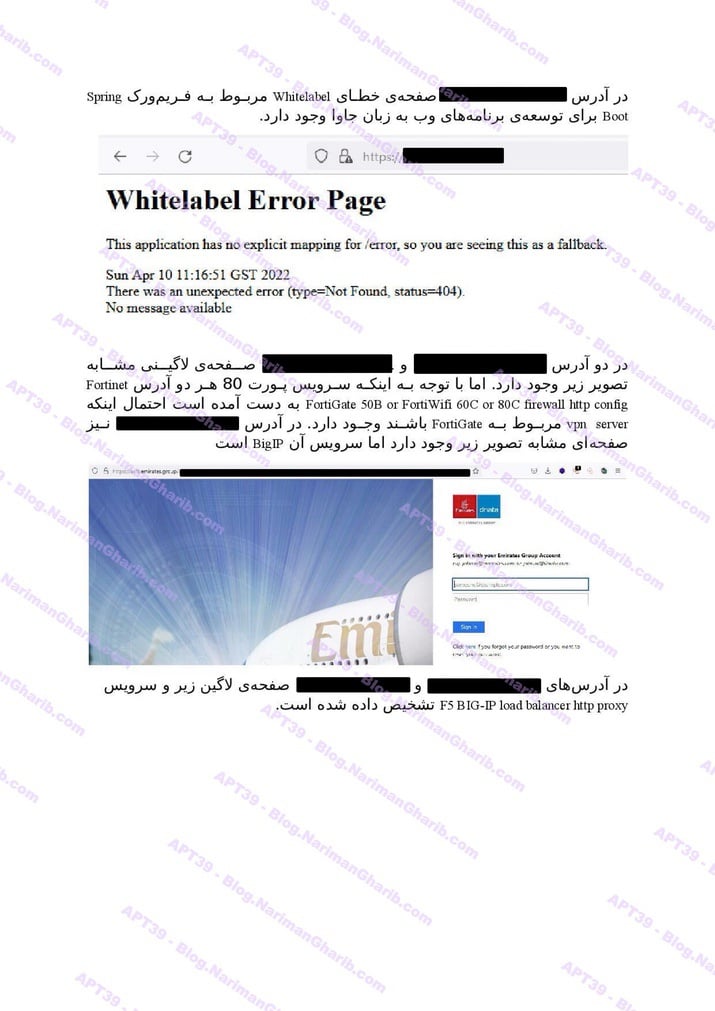
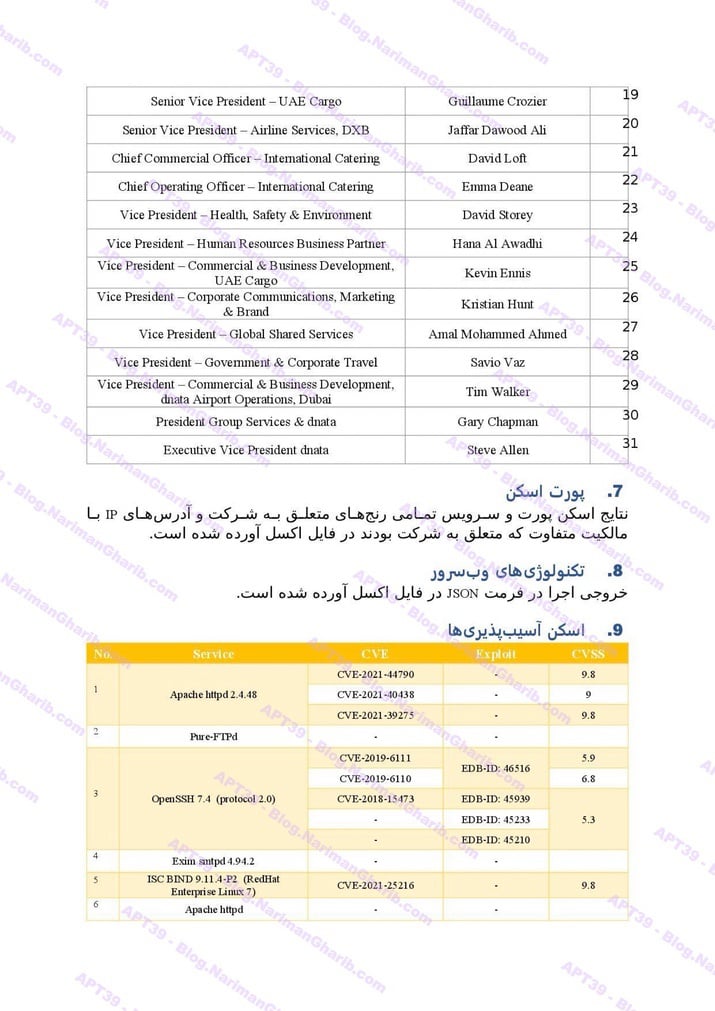
Etihad
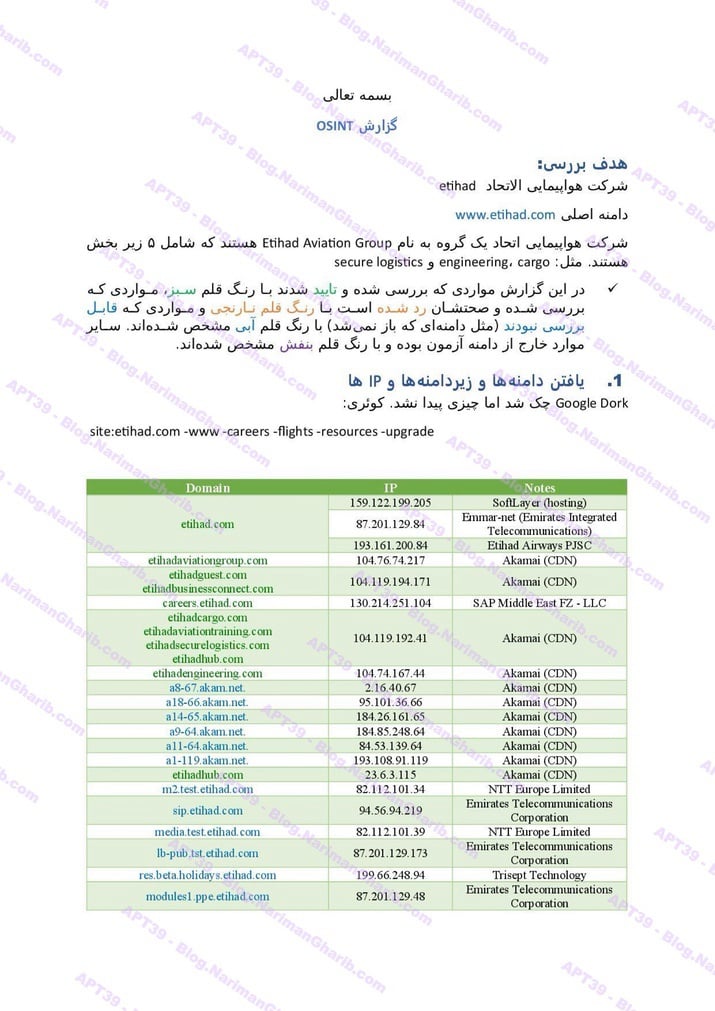
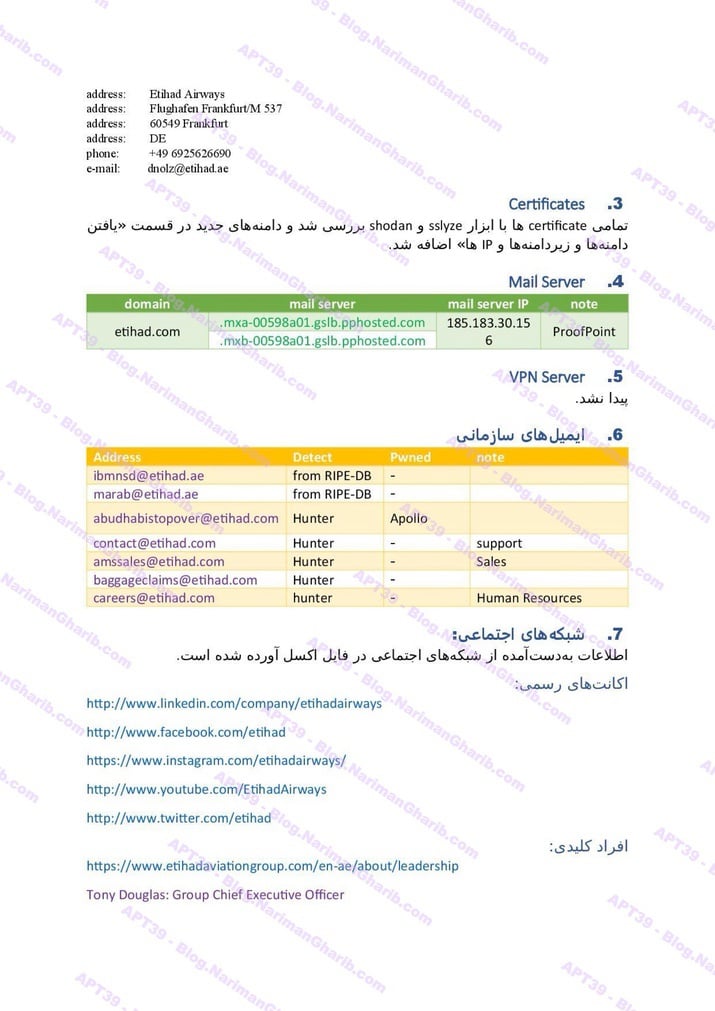
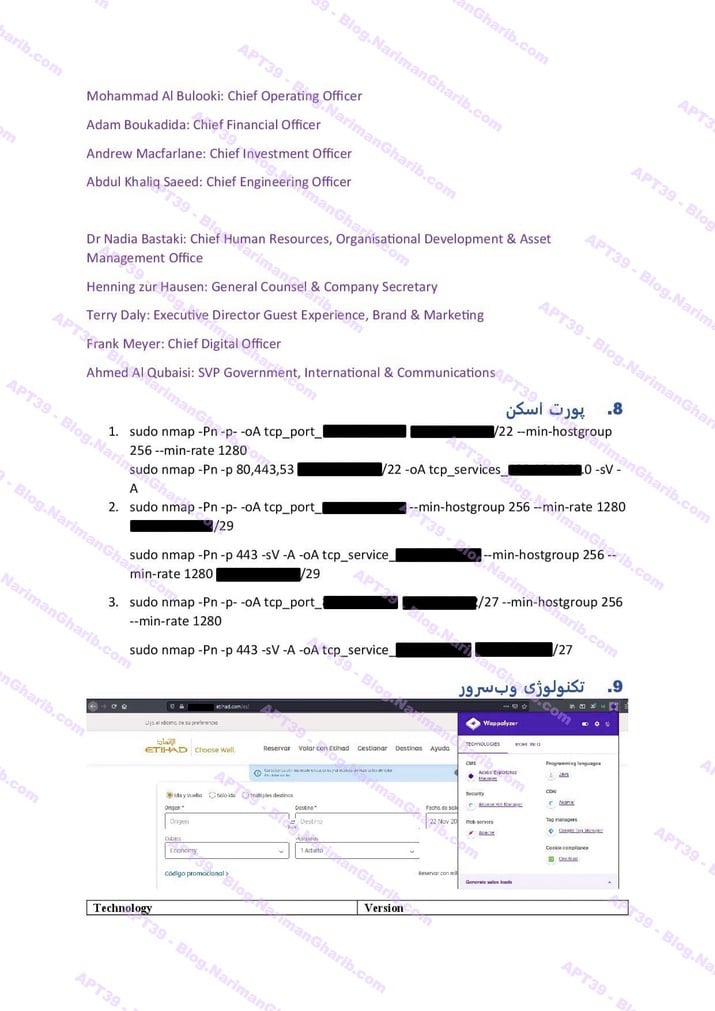
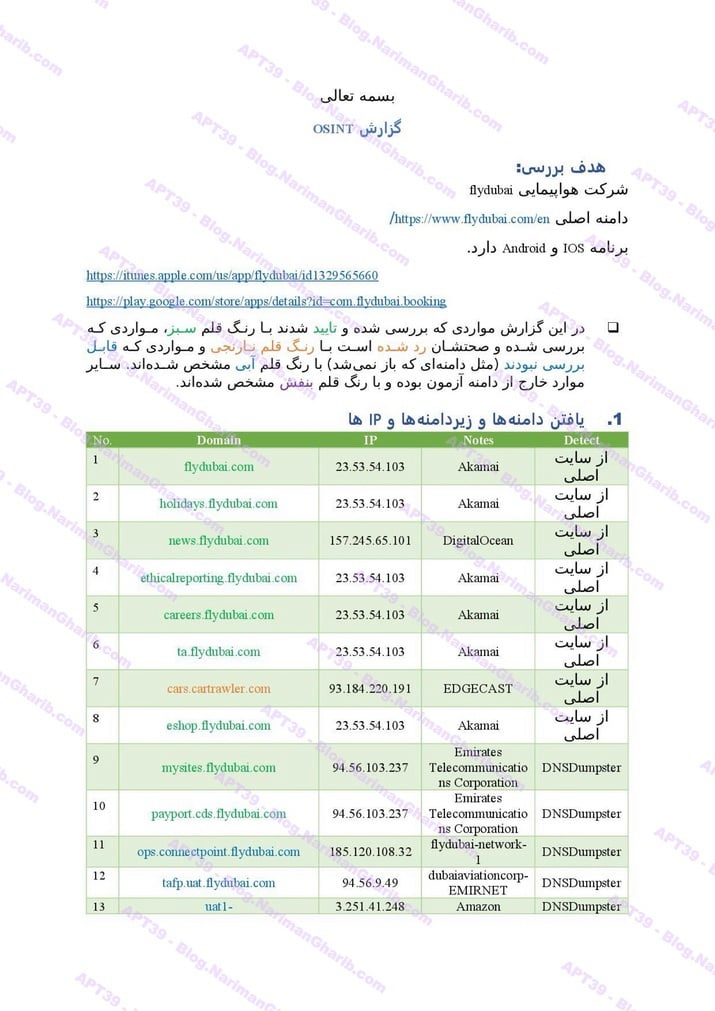
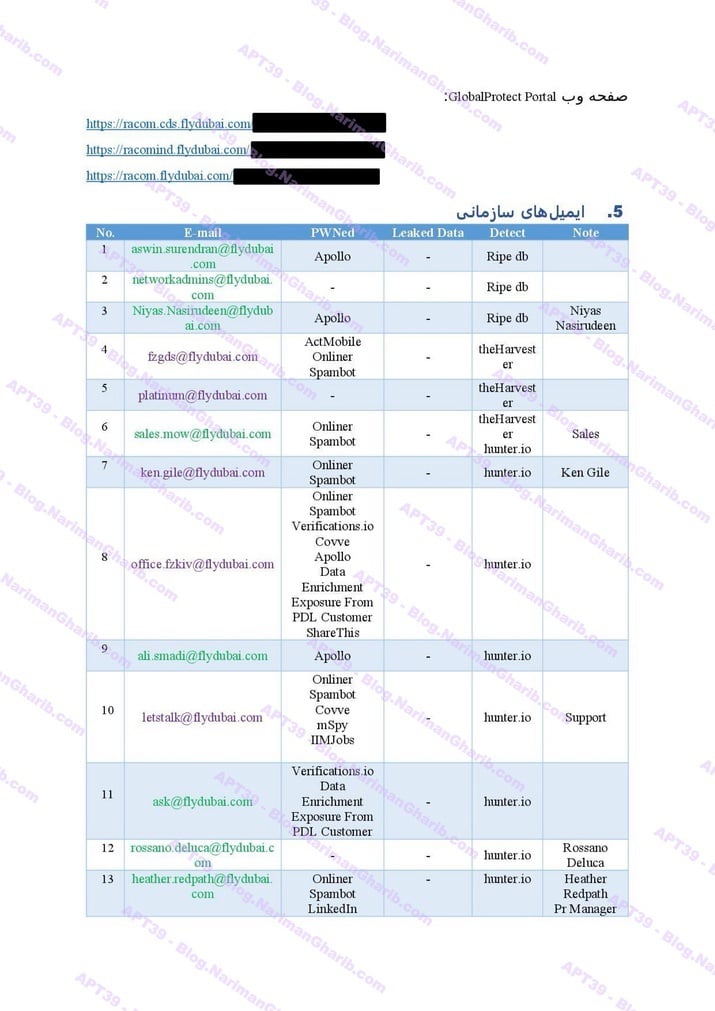
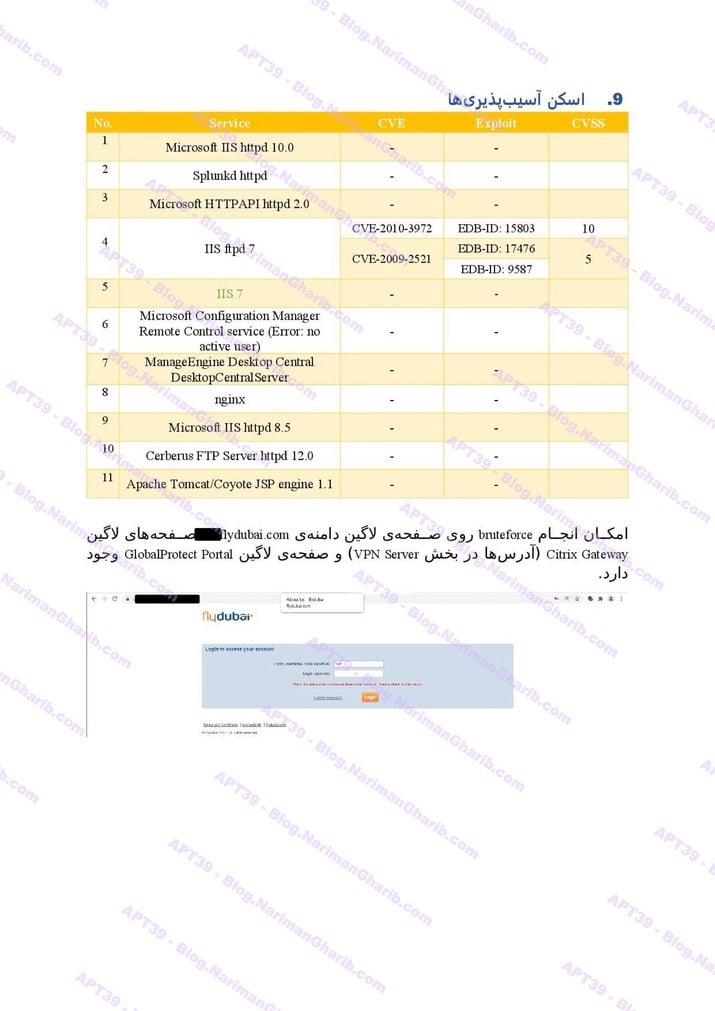
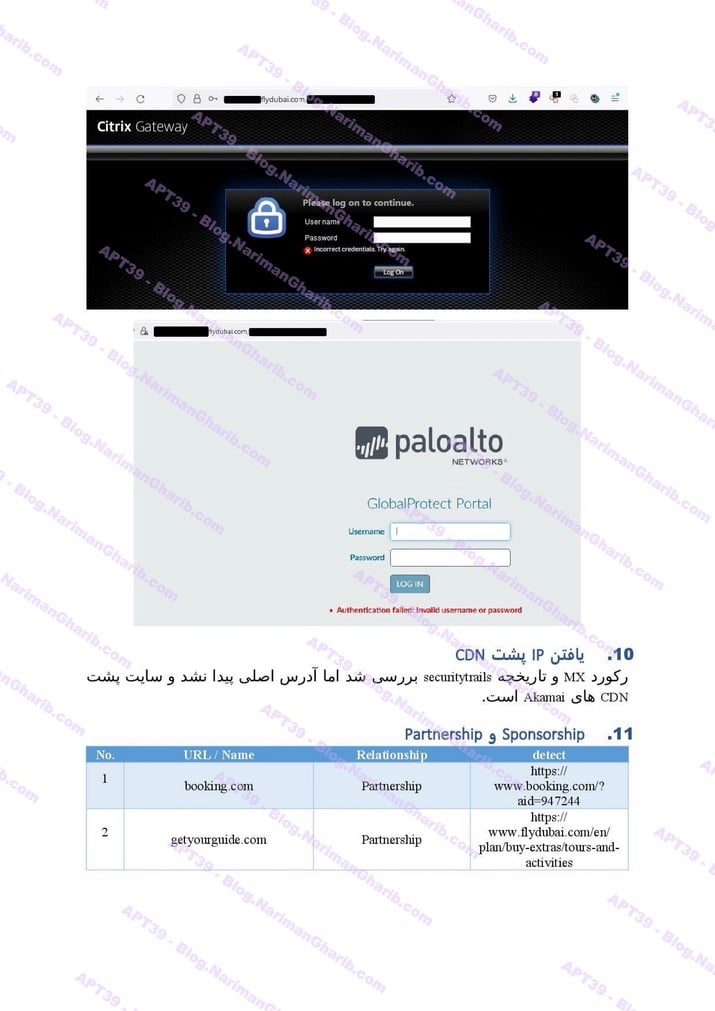
FedEx

Flydubai
Ukraine International Airlines (UIA)


Kenya Airways

Oman Air
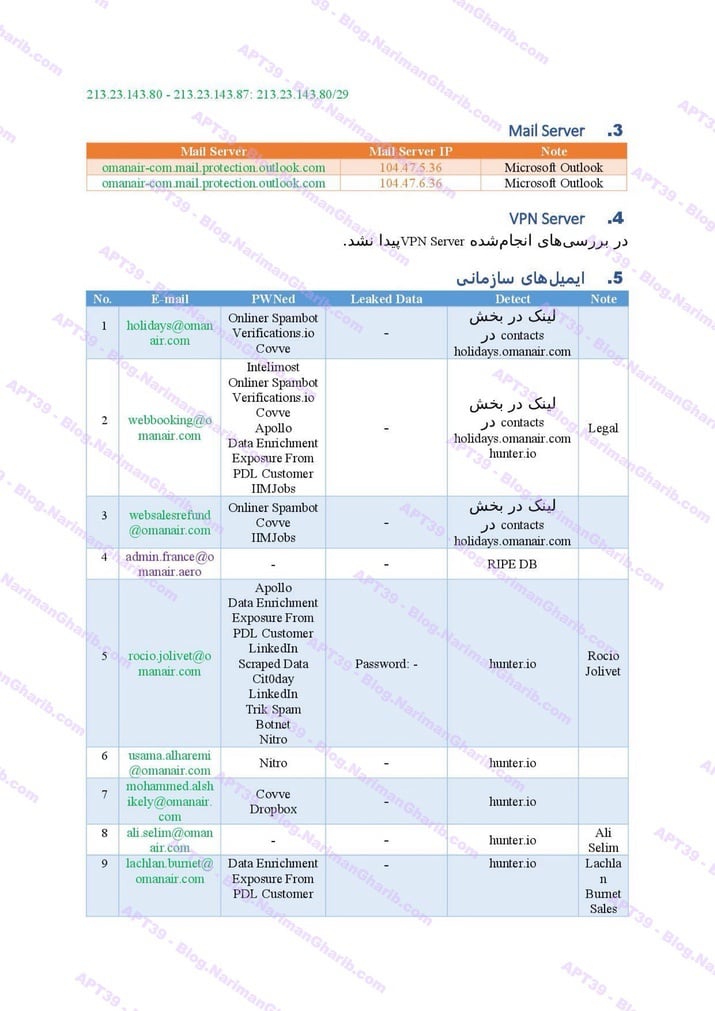
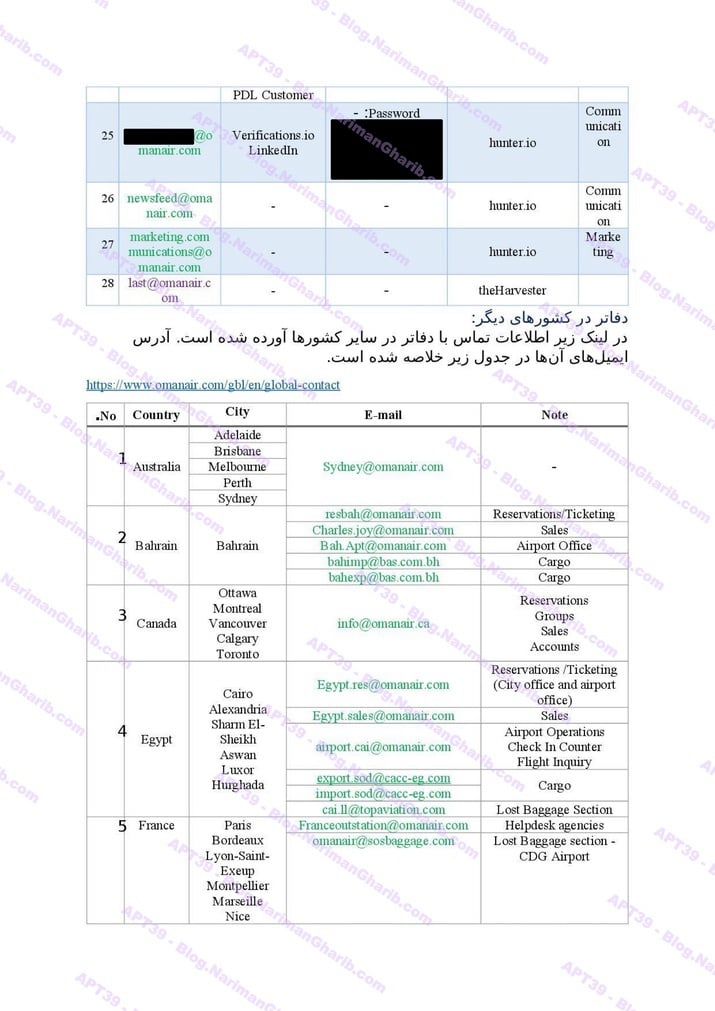
Qatar Airways
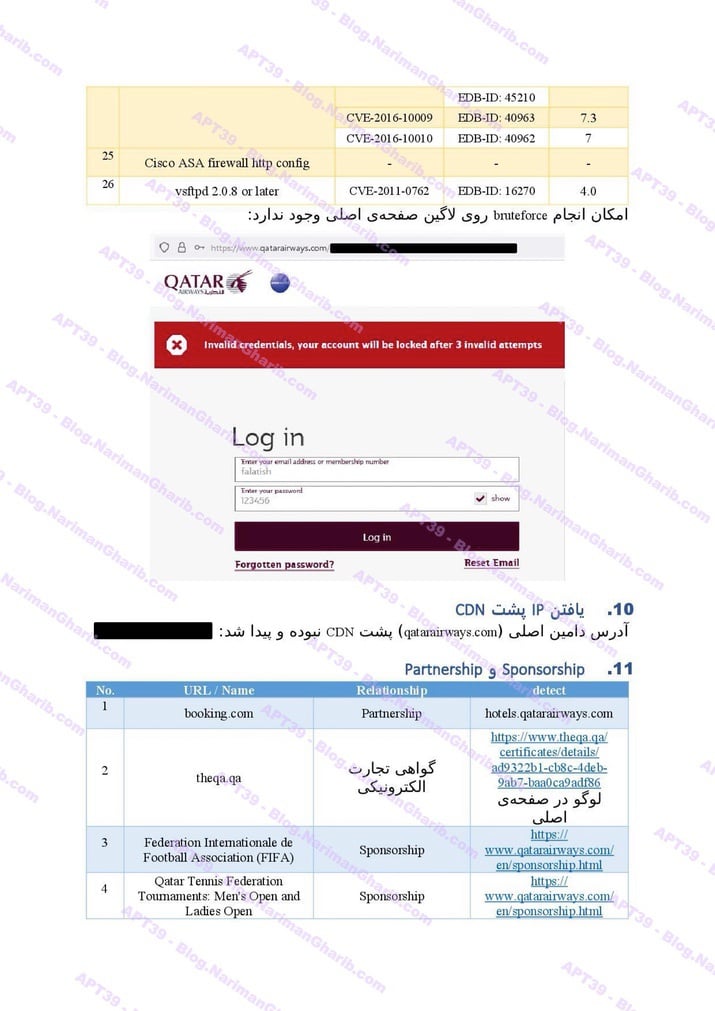
Azimuth Airlines



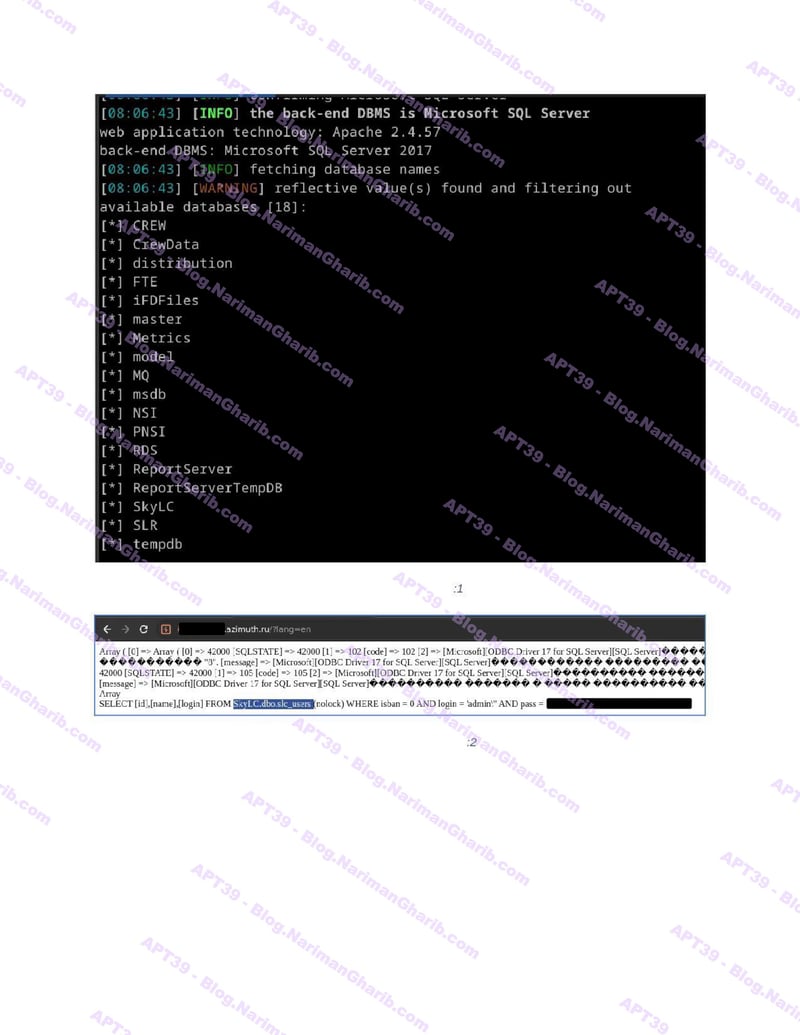
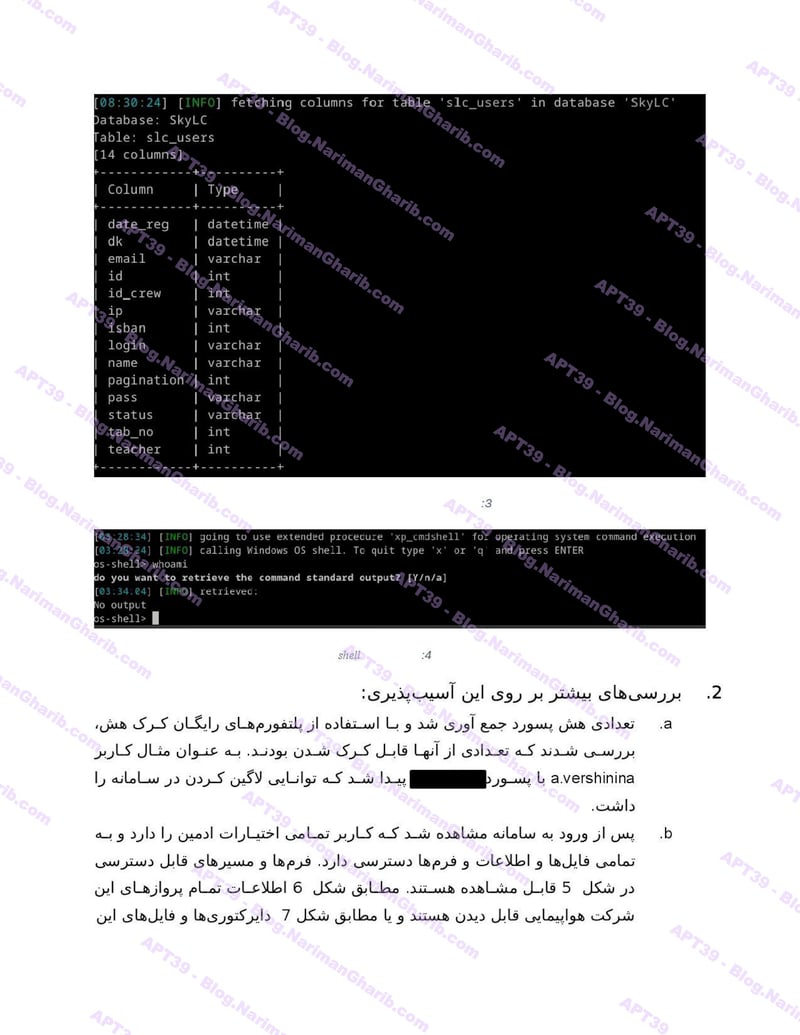
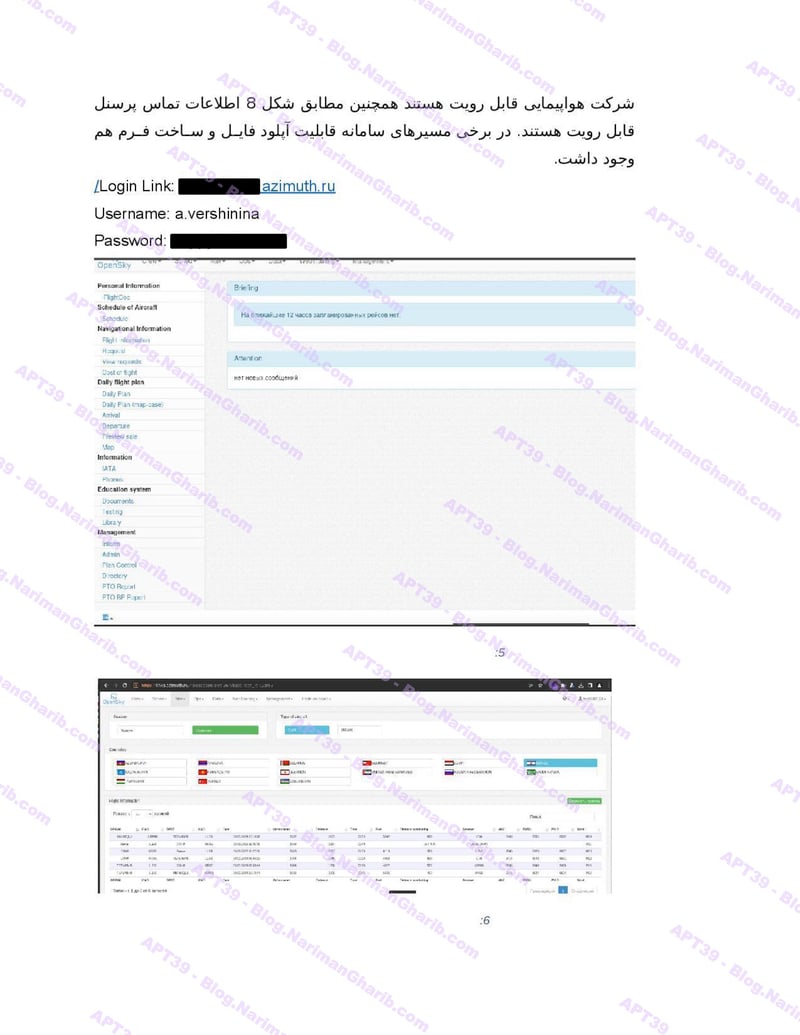
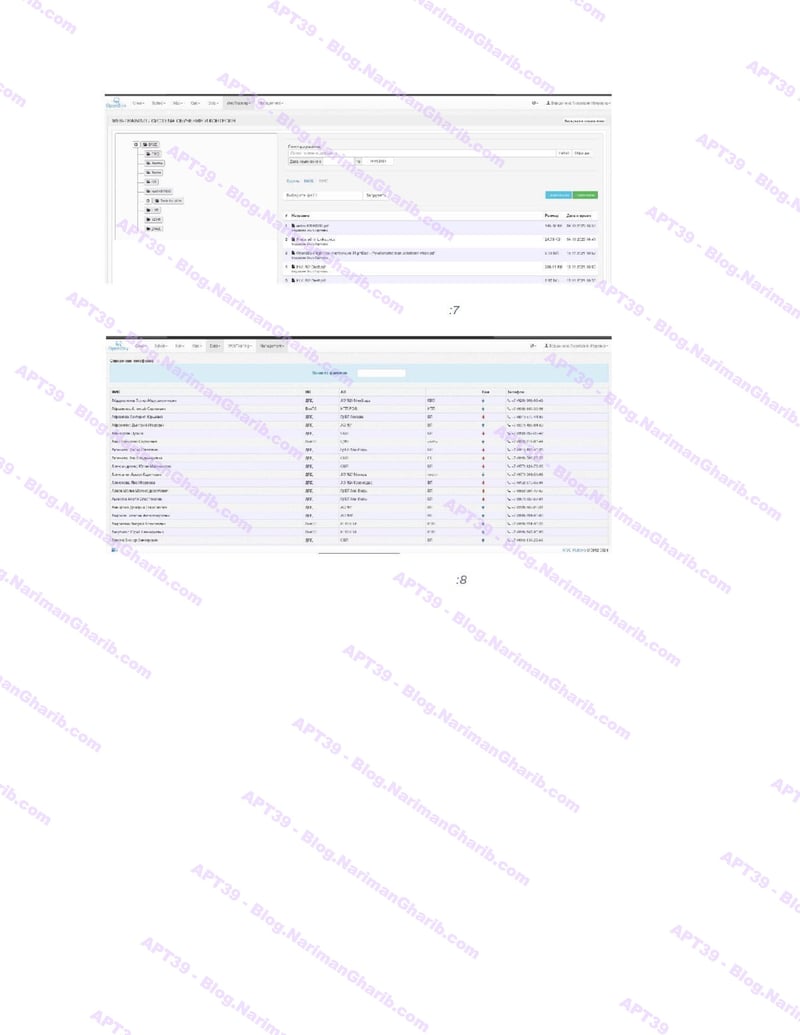
RwandAir
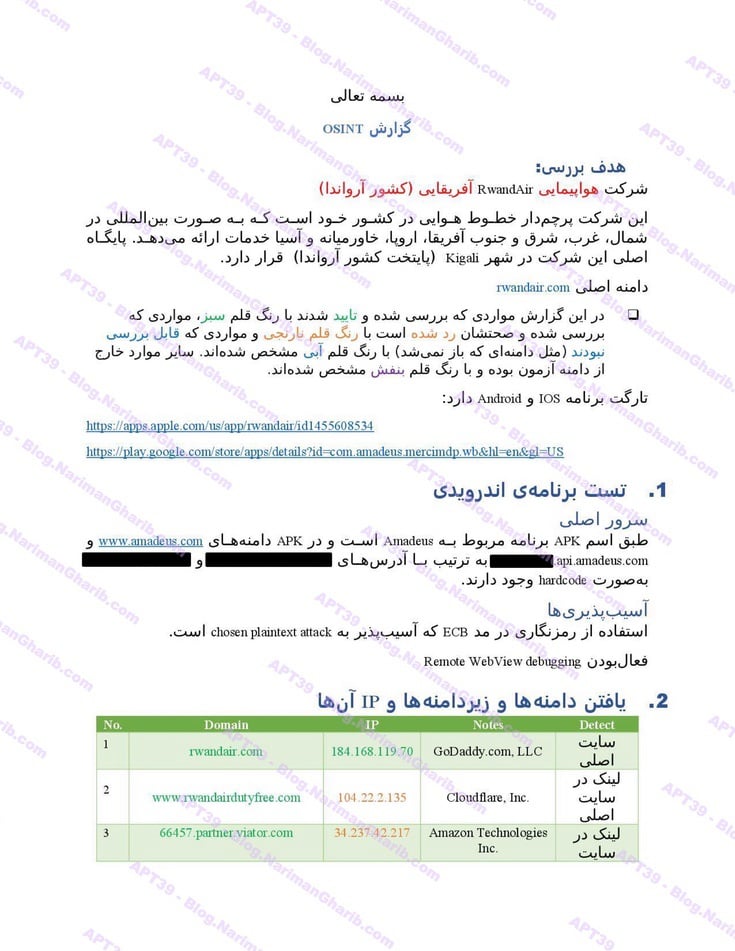
Uganda Airlines
Zambia Airways

Wizz Air


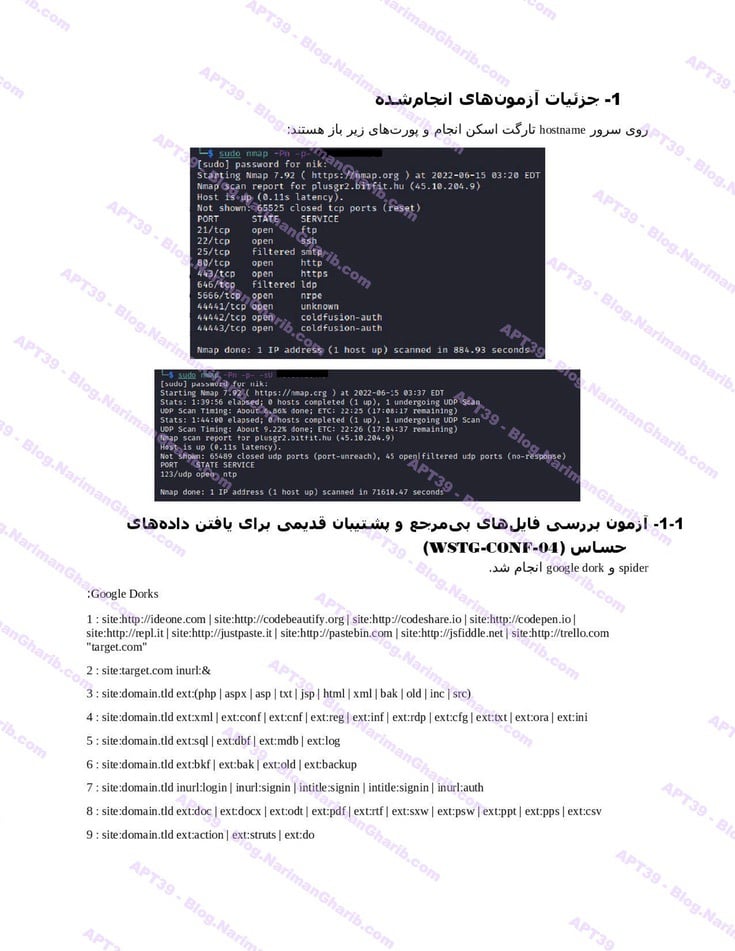
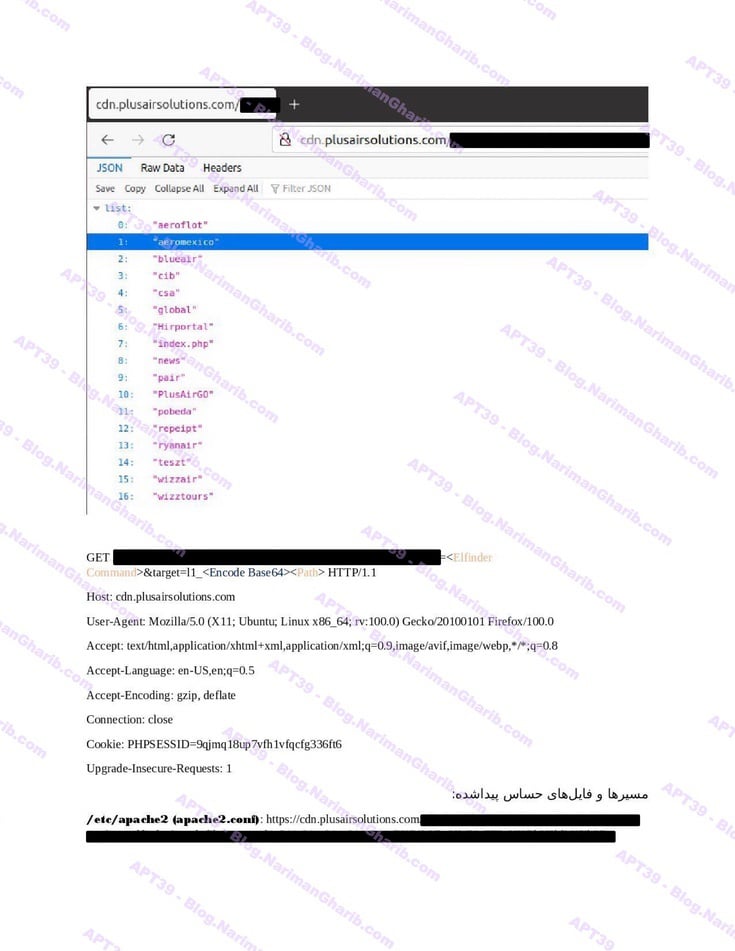
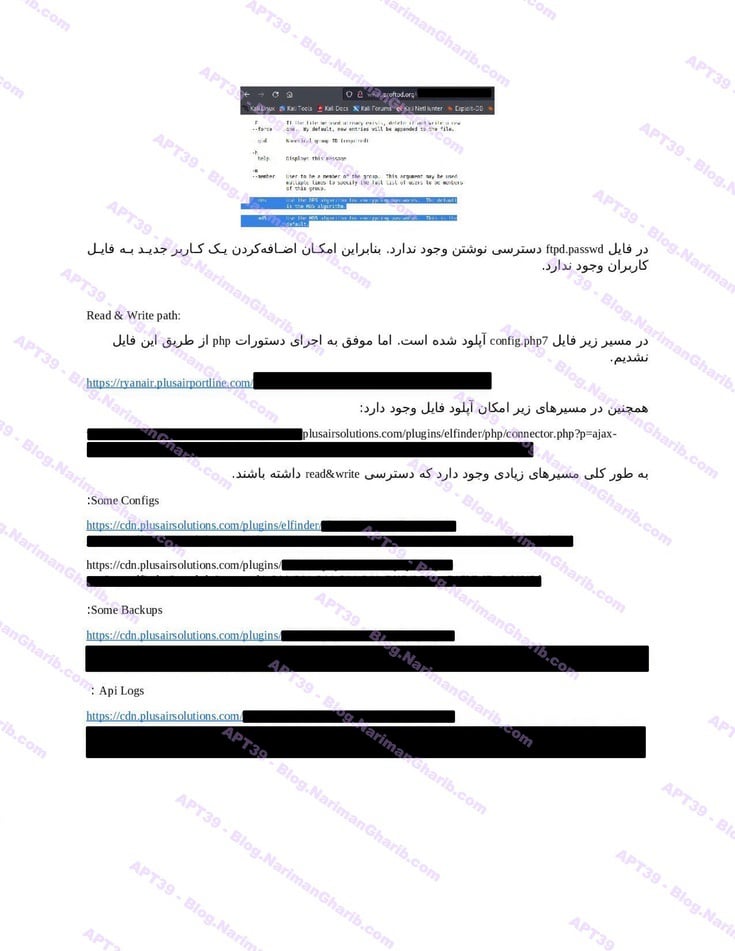
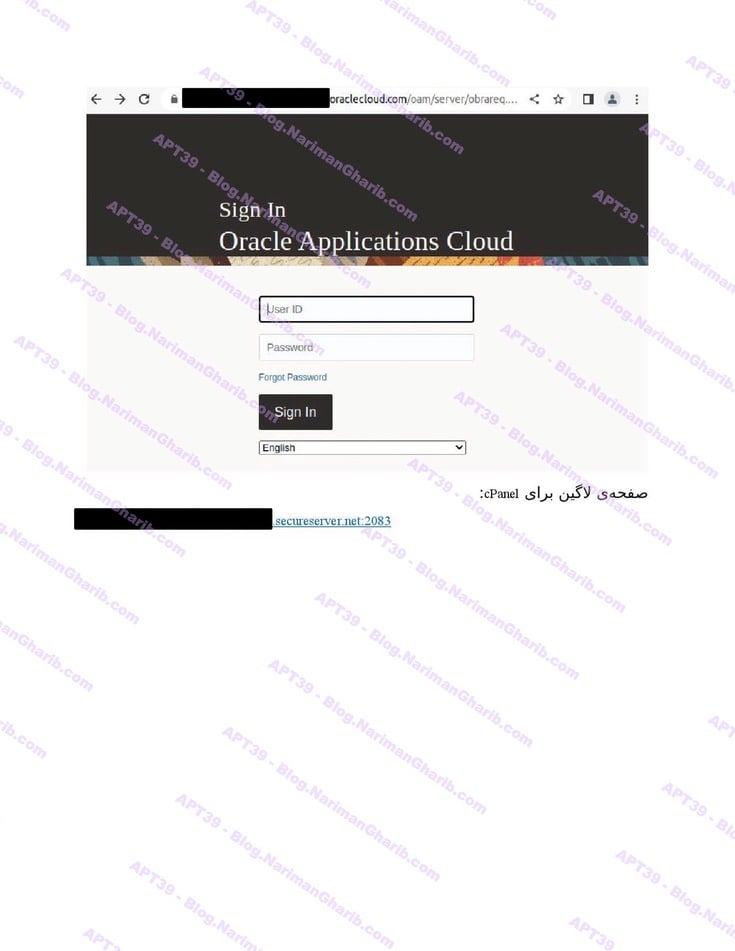
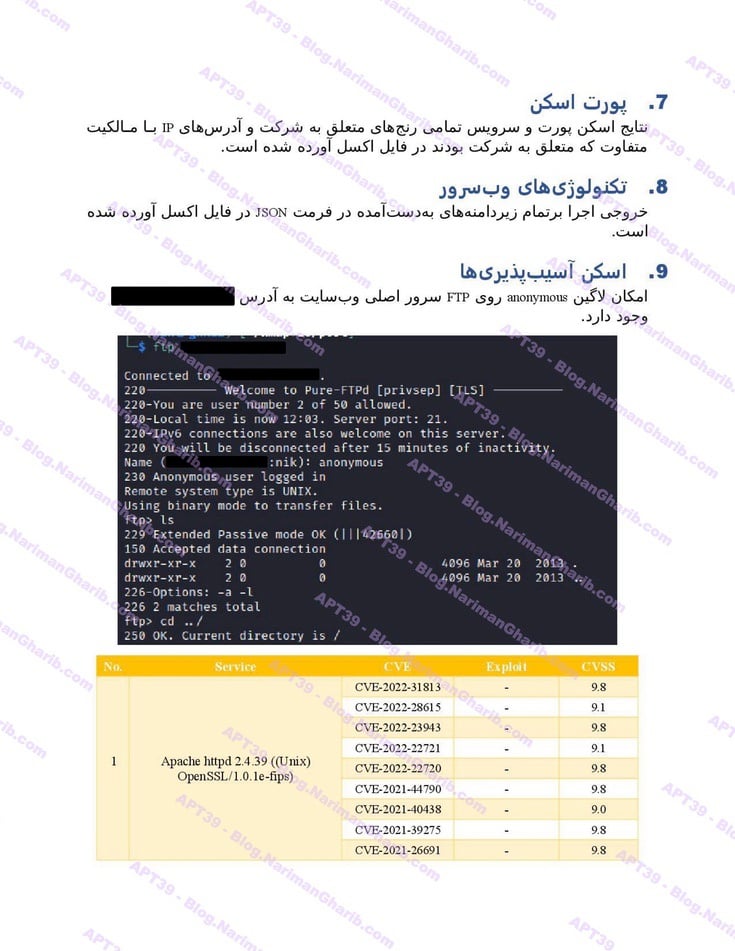
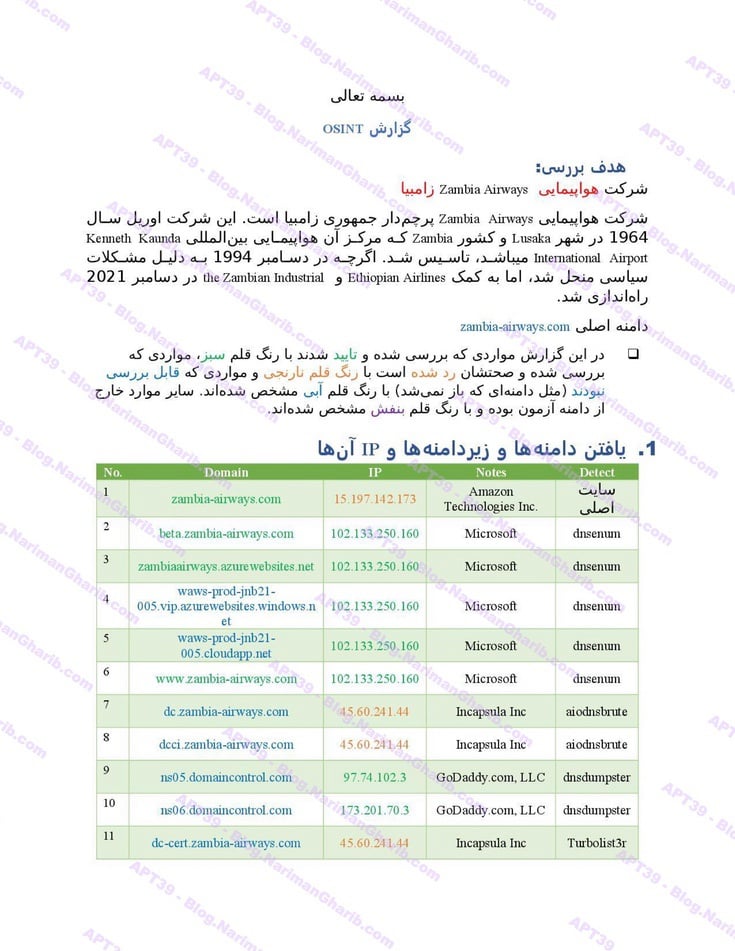
The videos I have are very clear.. Hours of footage showing Amnban operatives methodically mapping attack vectors against each target. This isn't hobbyist hacking or security research. No company requested these "audits." What legitimate Iranian firm would dare probe international airlines without permission—unless they had protection from the very top?
Screenshots taken from their self-produced videos documenting the attacks
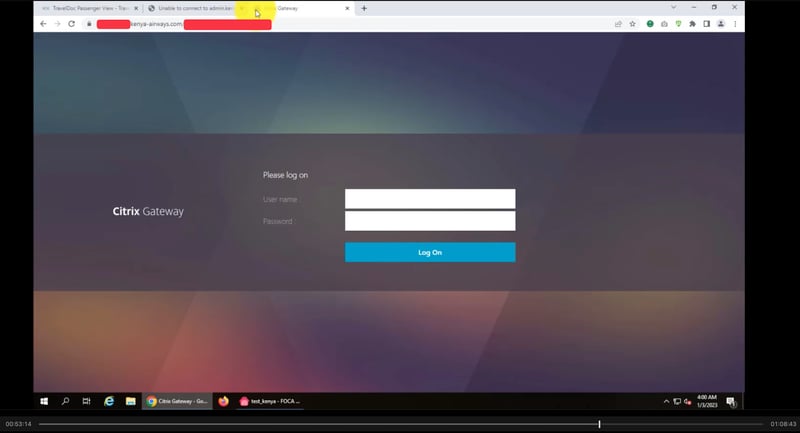
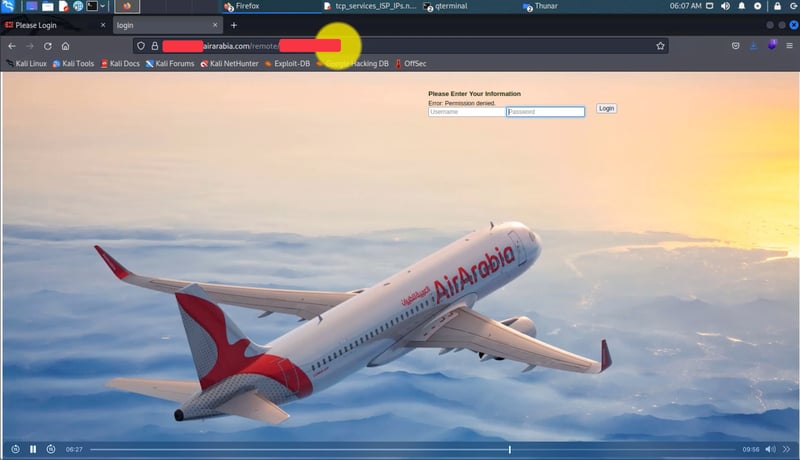
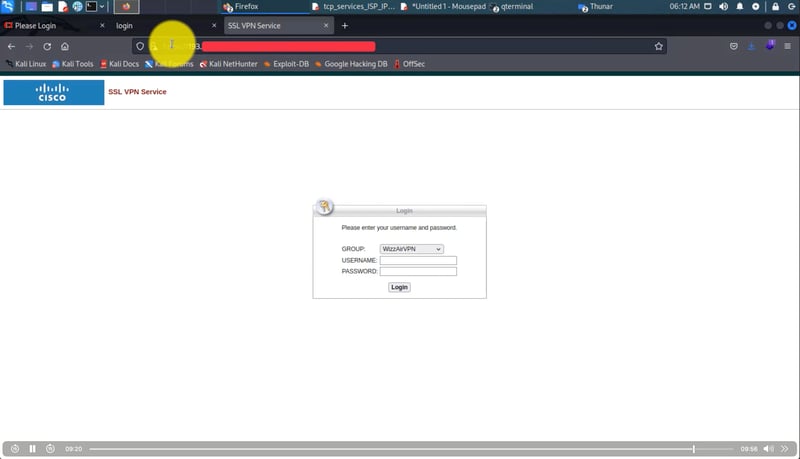
The smoking gun hides in their file structure: folders labeled "Projects" and "R&D." Security researchers don't organize airline hacks as "projects." Intelligence agencies do.
These aren't vulnerability reports—they're operational blueprints commissioned by handlers who need to track specific individuals and compromise international systems.
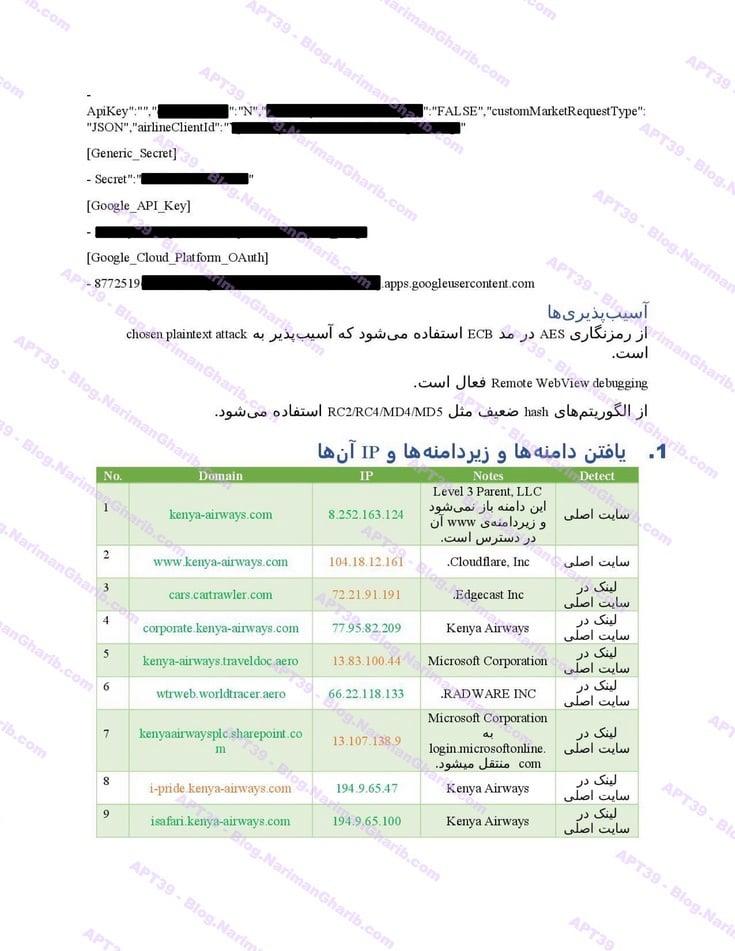
The level of detail is staggering: passenger lists, home addresses, passport numbers, contact information, recent photographs. Everything an intelligence service needs for surveillance, identity theft, or worse. History shows us exactly how Tehran uses such data—to hunt dissidents, plan operations, and violate human rights on a global scale.
The Cryptocurrency Hunt
Airlines were just the beginning. Amnban's "social engineering.docs" file chronicles their parallel campaign against cryptocurrency exchanges. Each entry reads like a stalker's notes, documenting phishing attempts against key employees who might provide network access.
The examples are chilling in their banality:
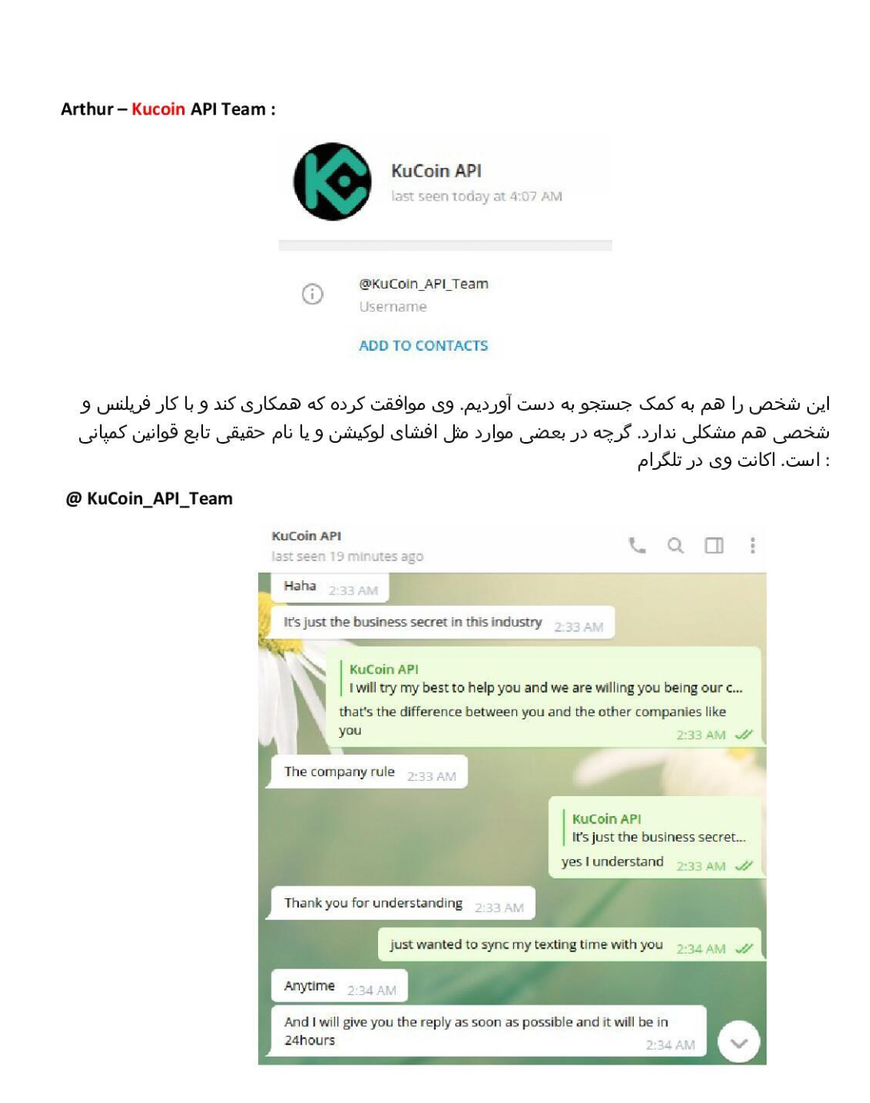
1- Arthur, API Department at KuCoin: "This person was also found through search. He agreed to cooperate and has no problem with freelance or personal work. Although in some cases, such as disclosing location or real name, he follows company rules. His Telegram account: "
They profile him like an asset—cooperation level, security consciousness, personal contacts.
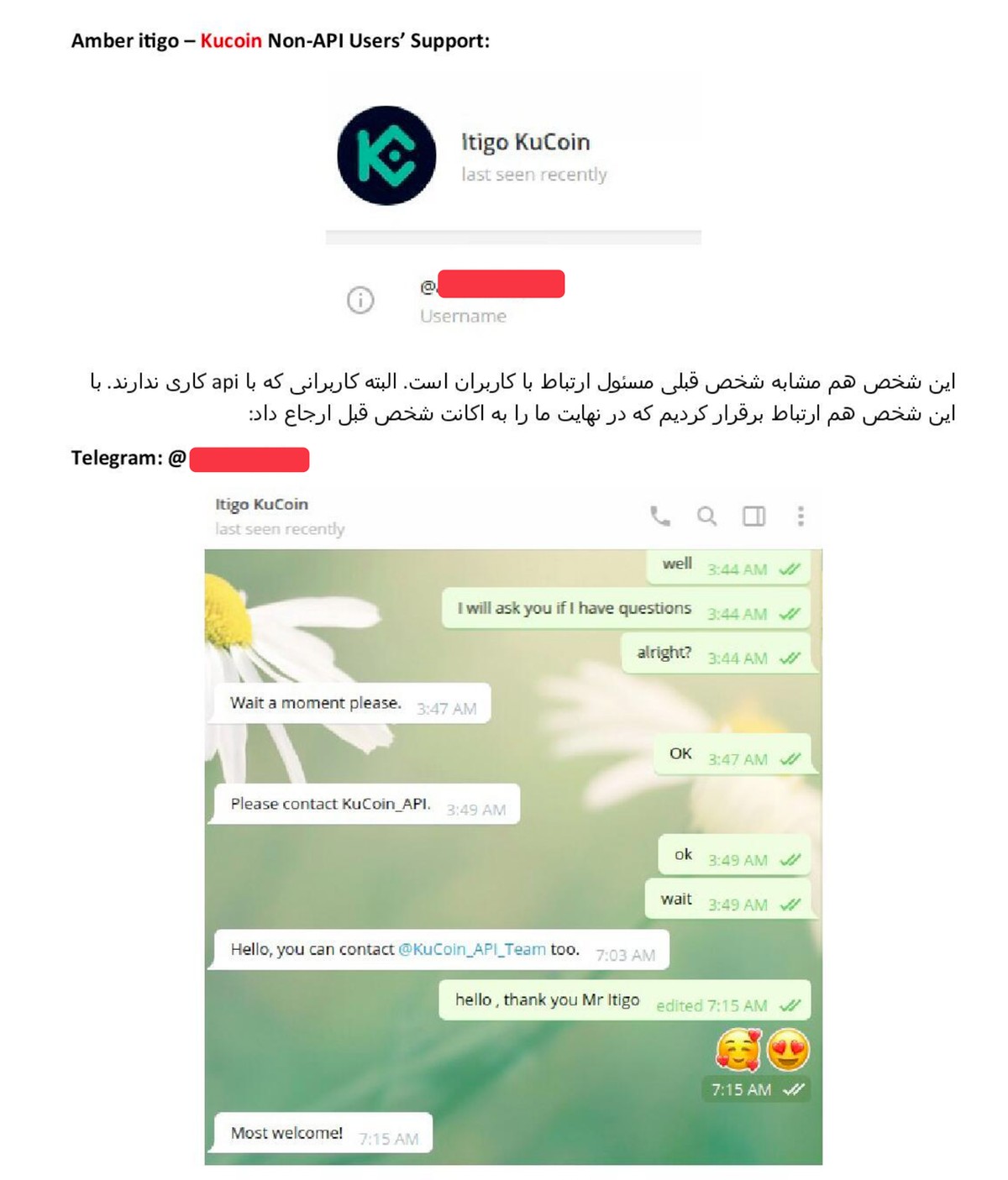
2- Amber support for KuCoin users without API access: "This person is similar to the previous person responsible for communicating with users. However, these are users who do not work with APIs. We also contacted this person, who ultimately referred us to the previous person's account: "
Building networks, mapping relationships, finding the weak links.
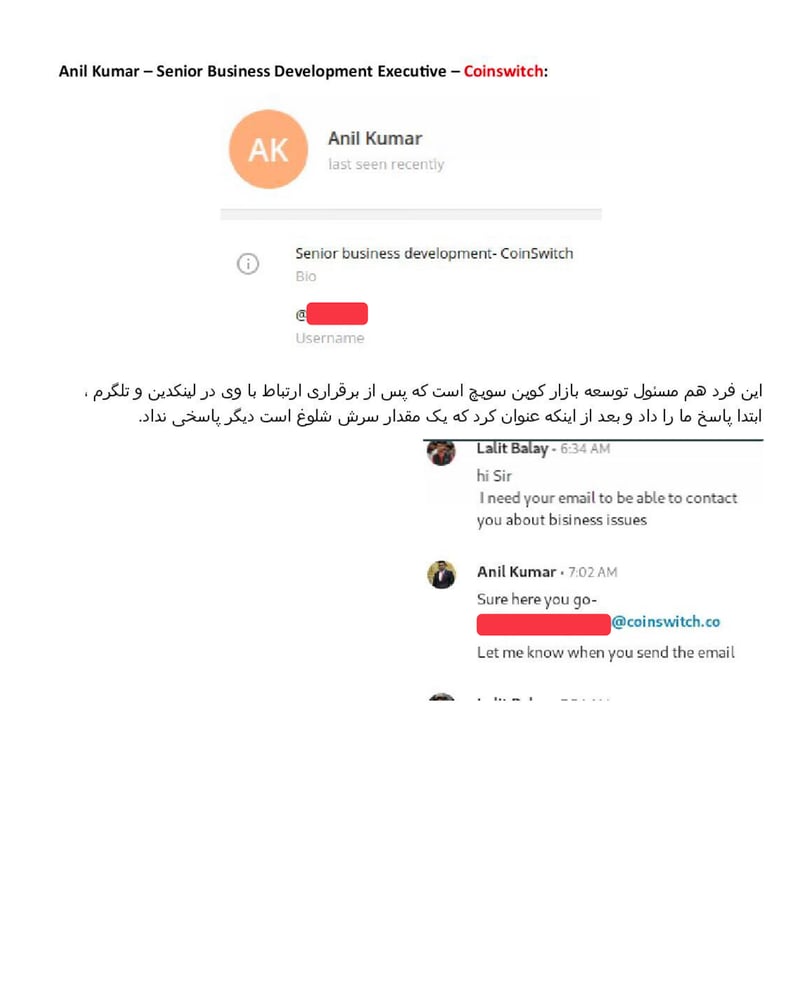
3- Anil Kumar, Senior Business Development Executive at CoinSwitch: "This person is also responsible for market development at CoinSwitch, who after contacting him on LinkedIn and Telegram initially responded to us and then stopped responding after stating that he was quite busy."
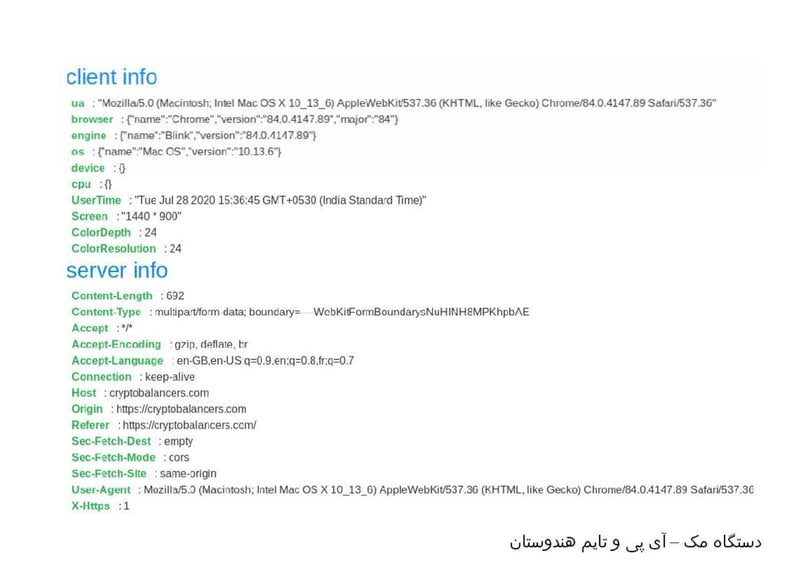
Then APT39 sends a tracking link to harvest his IP and device data. When charm fails, they resort to technical exploitation.
CoinSwitch
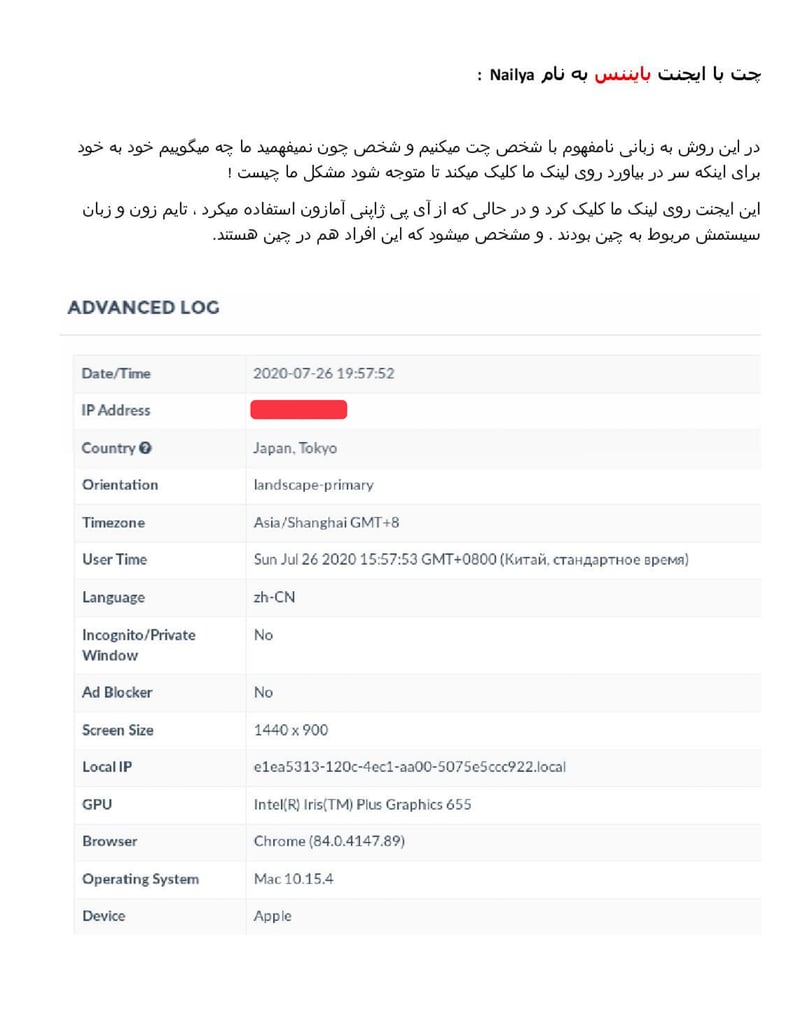
4- Chat with a Binance agent named Naliya: "In this method, we chat with the person in an incomprehensible language and the person automatically clicks on our link to understand what our problem is because they don't understand what we are saying! This agent clicked on our link and while using a Japanese Amazon IP, their timezone and system language were related to China, indicating that these individuals are also in China."
Psychological manipulation at its finest—confuse the target into clicking malicious links.
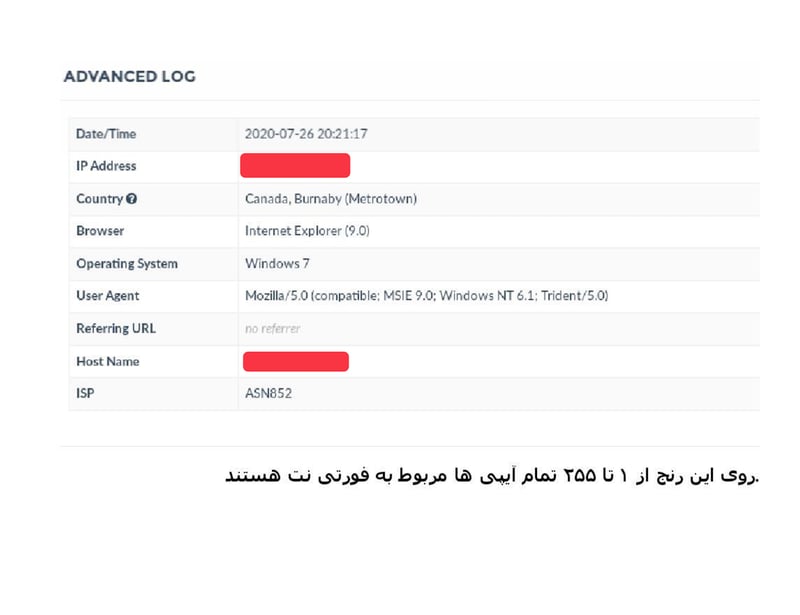
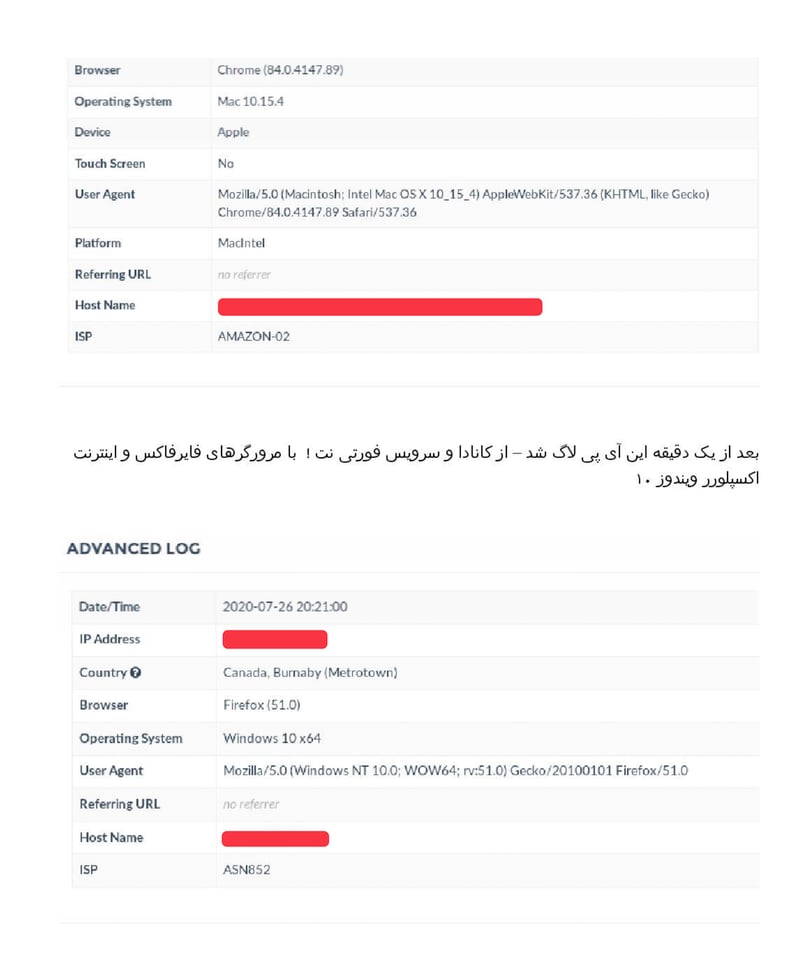
"After a minute this IP was logged - from Canada and Fortinet service! With Firefox and Internet Explorer Windows 10 - all IPs in the range of 1 to 255 are related to Fortinet."
Every click is harvested. Every detail logged.
Binance
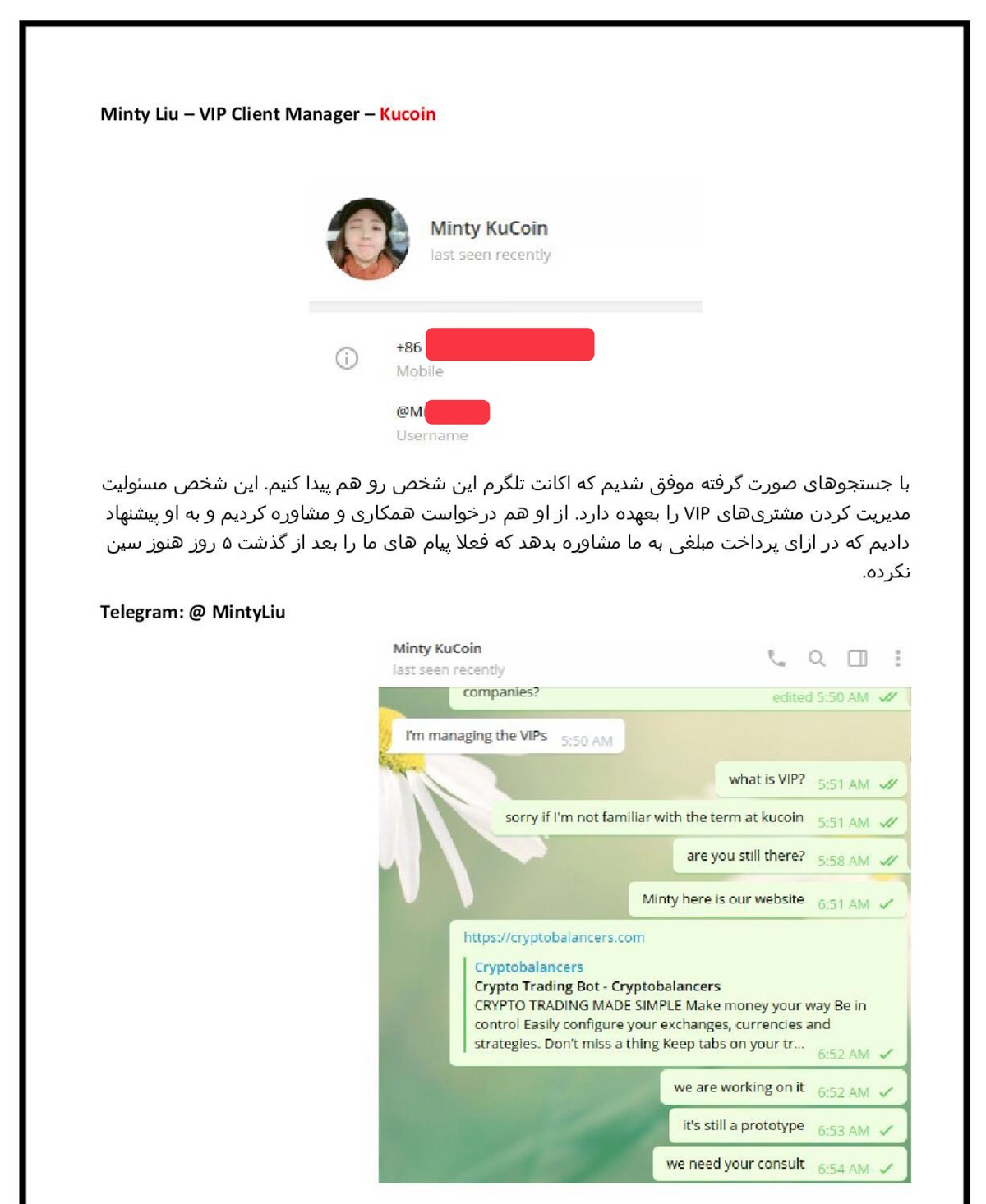
5- Minty Liu – VIP Client Manager at KuCoin: "Through searches, we were able to find this person's Telegram account as well. This person is responsible for managing VIP clients. We also requested cooperation and consultation from him and offered to pay him a fee in exchange for his consultation, but he has not seen our messages after 5 days."
They're not just phishing—they're offering to pay insiders. When hacking fails, try bribery.
Here is the fake LinkedIn profile they created for this purpose, which is still up and Microsoft has not removed it yet.
The Shadow Infrastructure
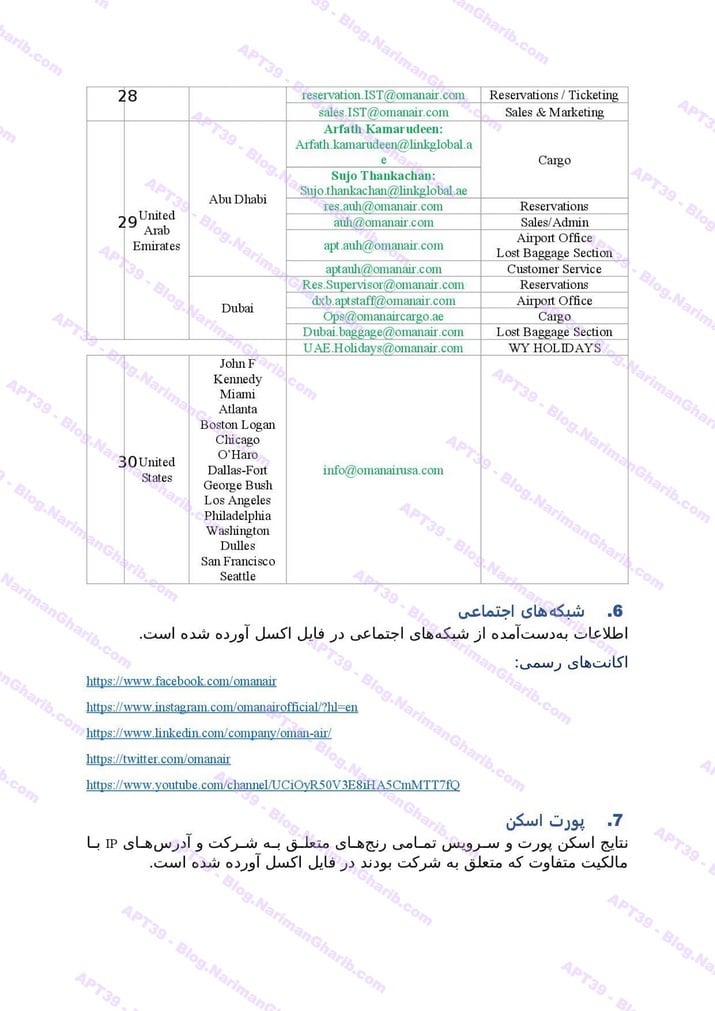
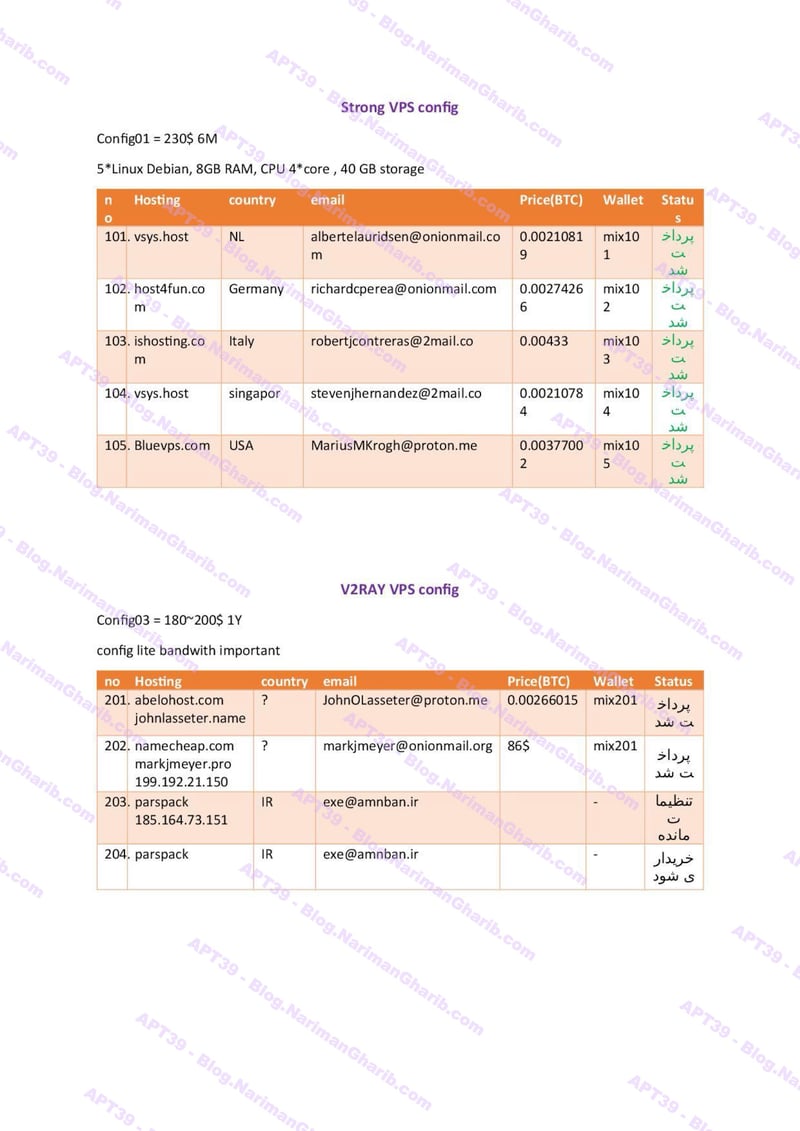
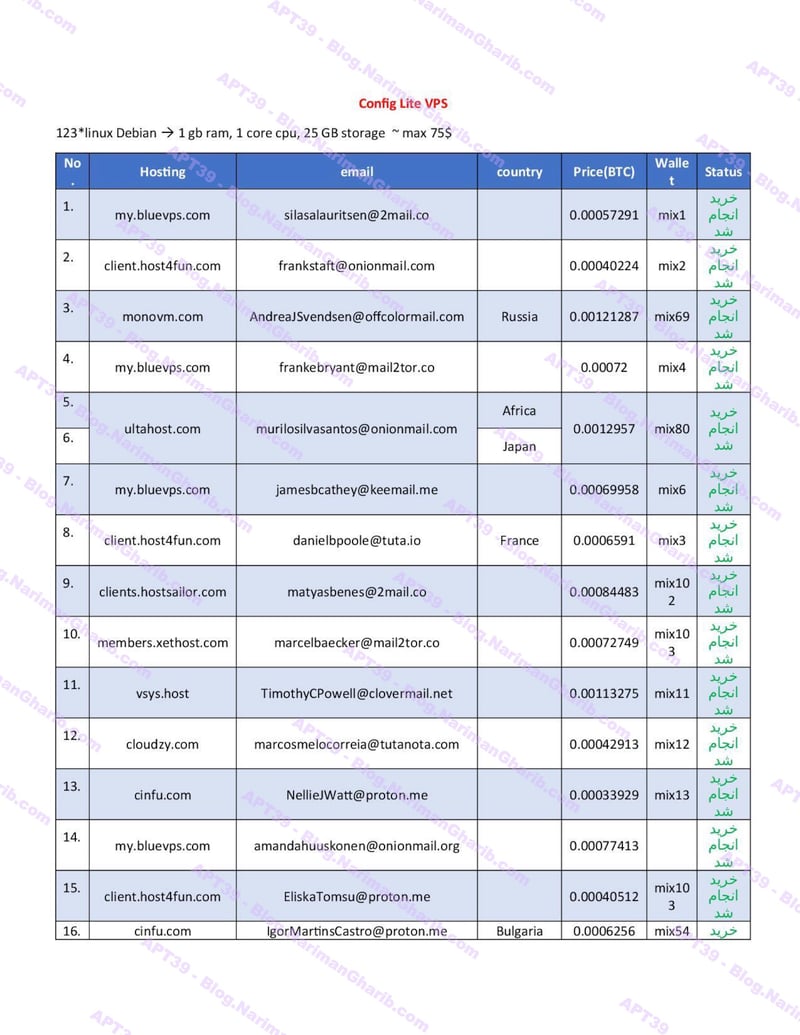
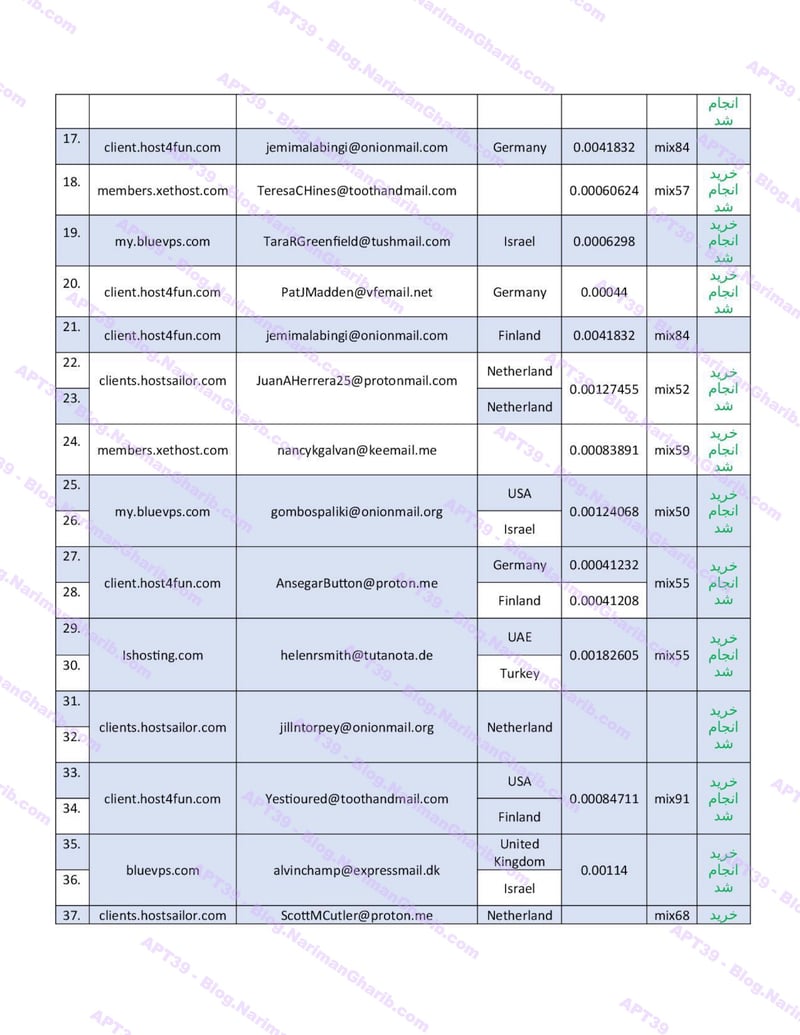
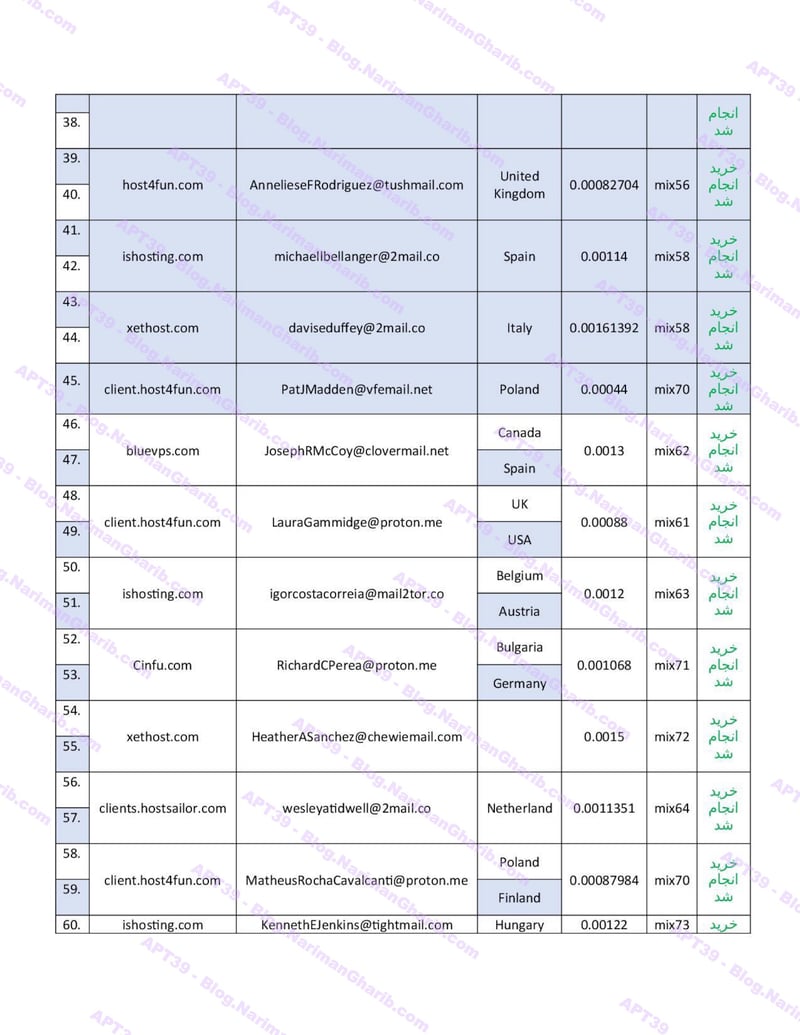
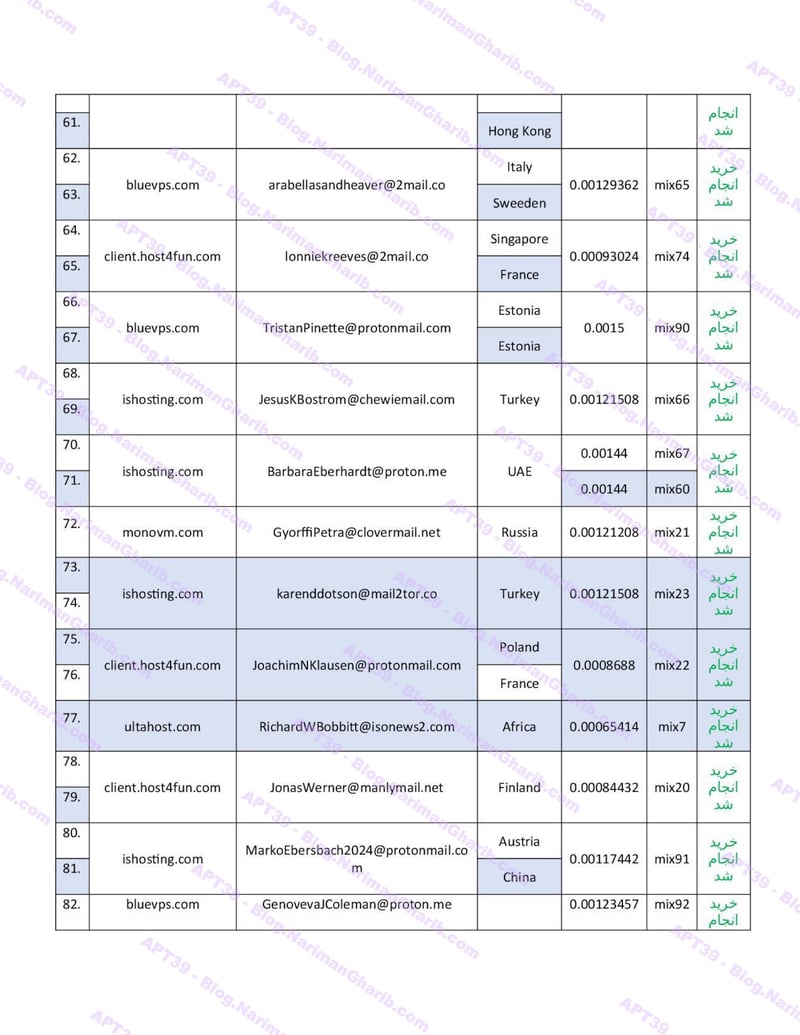
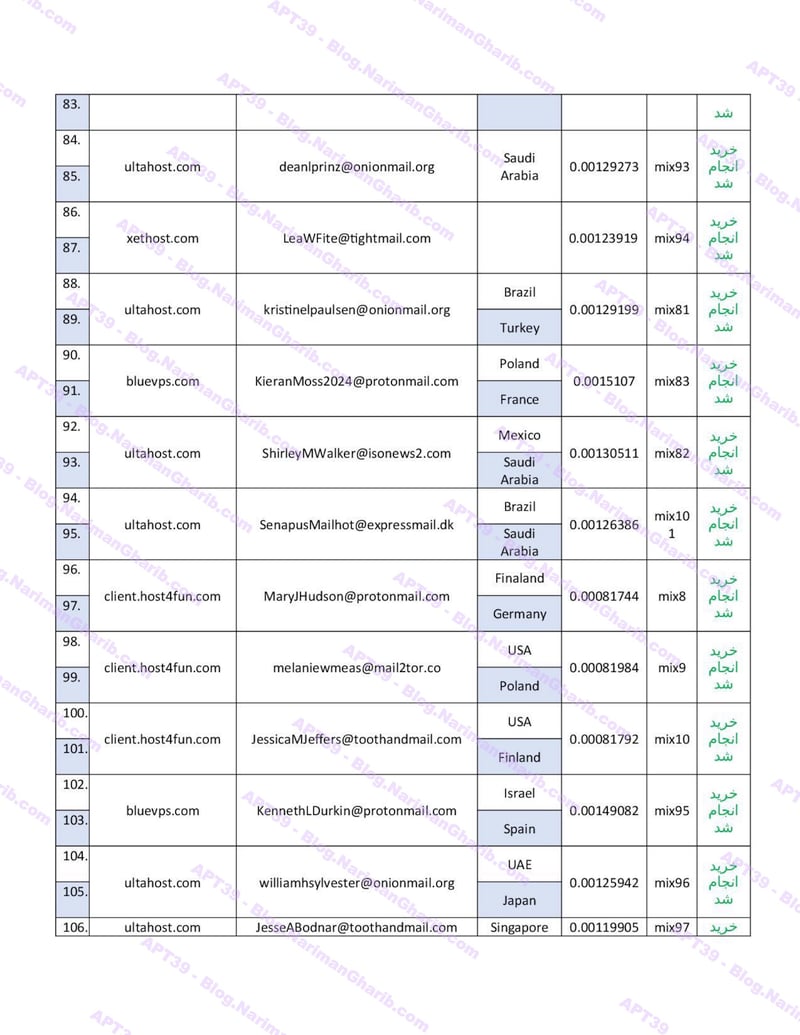
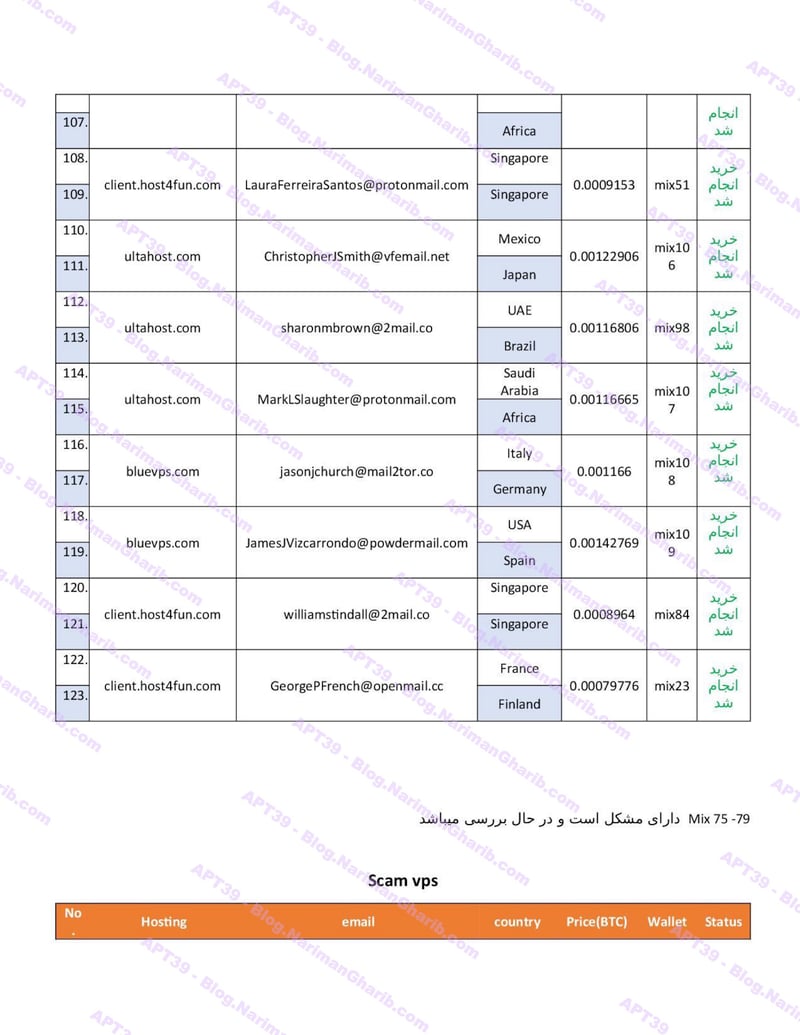
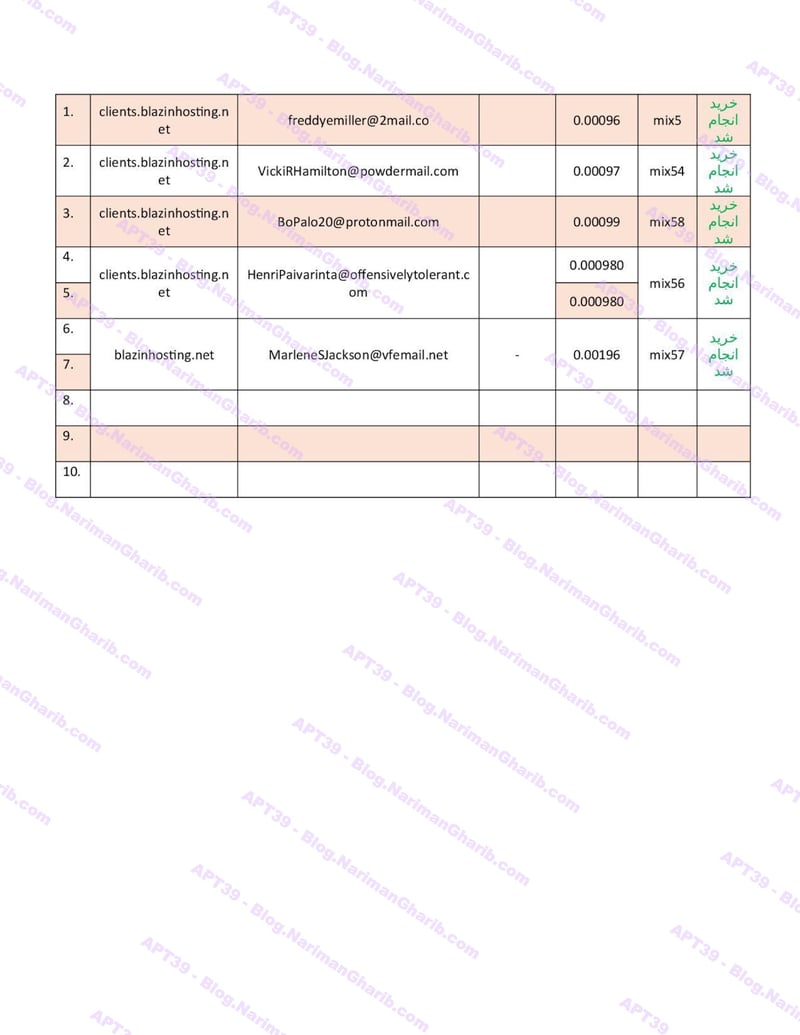
Hundreds of fake email address provision servers worldwide. This isn't one operation—it's a global network of attack infrastructure, each node another launch point for their campaigns. The leaked server list maps their entire operational footprint:
VPS + Emails
If you are employed at one of these European or American companies, please send me an email from your official company email address so that I can send you the file related to your company. Unfortunately, it is not possible to send all the files, but I will provide you with as much of the information you need as possible.



